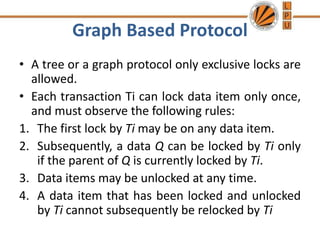
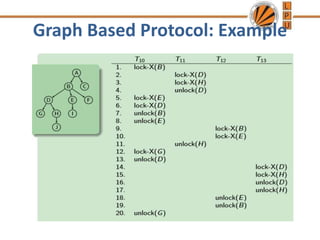
The document discusses various concurrency control protocols used to maintain database consistency with concurrent transaction execution. It describes lock-based protocols that use locks to control transaction access to shared data, including two-phase locking and various lock types. It also summarizes timestamp-based and validation-based protocols as alternative approaches to concurrency control.