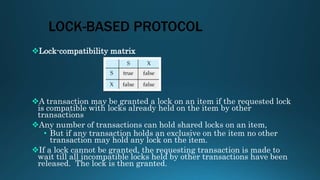
This document discusses various concurrency control protocols used to manage concurrent access to databases. It describes lock-based protocols that use locking mechanisms to control access. It also covers timestamp-based protocols that order transactions based on timestamps to ensure serializability. Finally, it discusses validation-based or optimistic protocols that validate transactions have not violated consistency before committing writes.