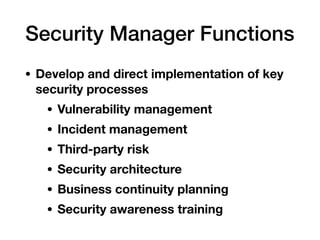
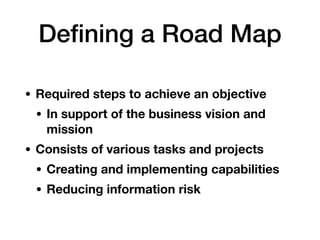
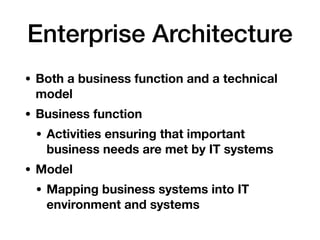
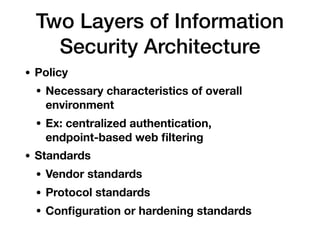
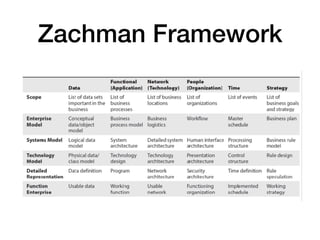
This document outlines the essential components of cybersecurity responsibilities, focusing on the development and management of information security programs. It discusses strategic alignment, risk management, resource management, and performance measurement necessary for effective information security governance. The document also covers various security management frameworks, roles within an organization such as the CISO, and the importance of collaboration among stakeholders to ensure a successful security strategy.