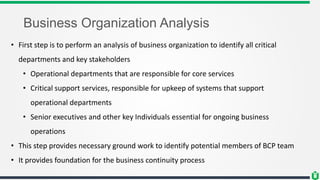
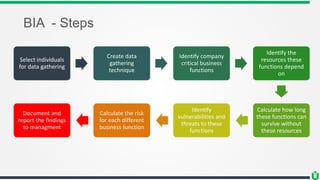
This document discusses business continuity planning (BCP). It outlines the key steps in developing an effective BCP, including: project scope and planning, business impact assessment, continuity planning, and approval/implementation. The project scope and planning phase involves analyzing the business organization, selecting a BCP team, assessing resource needs, and analyzing legal requirements. The business impact assessment identifies critical business functions, resources they depend on, risks/vulnerabilities, and calculates downtime tolerances. Continuity planning develops strategies to address identified risks and minimize their impact. The overall goal is to maintain business operations during a disaster through preparedness and recovery planning.