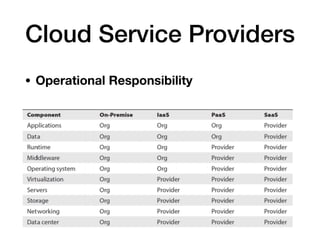
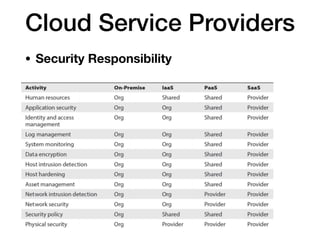
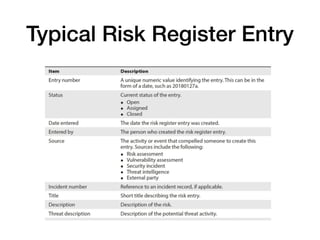
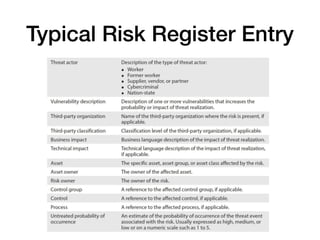
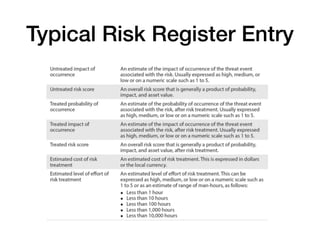
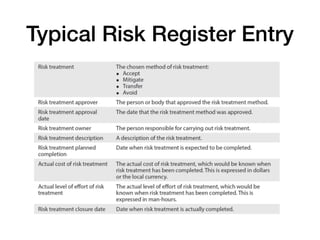
The document discusses cybersecurity responsibilities and information risk management, detailing topics such as operational risk management, recovery objectives, and third-party risk management. It outlines key concepts including recovery time objectives (RTO), recovery point objectives (RPO), and the importance of a risk register in managing business risks. Additionally, the document emphasizes the integration of risk management into various organizational processes, such as project management and incident response.