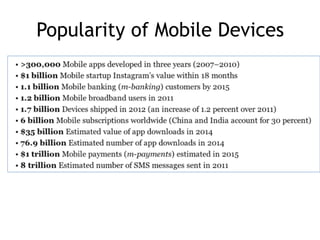
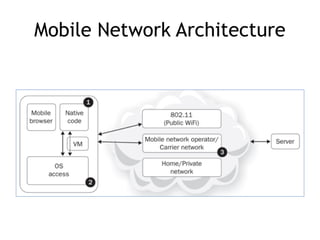
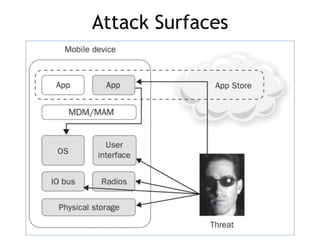
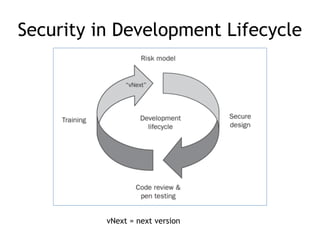
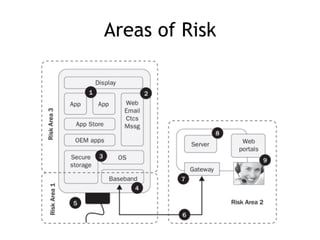
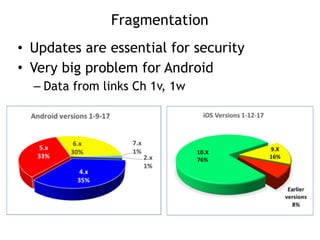
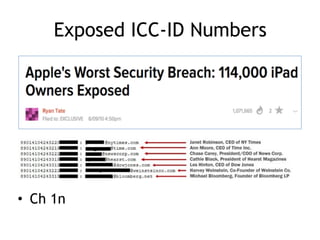
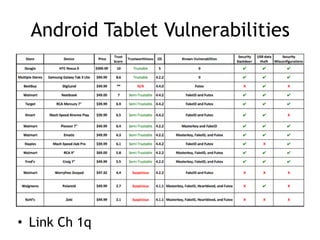
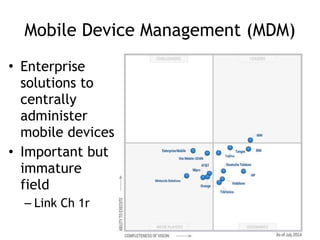
The document discusses the security risks associated with mobile devices, emphasizing vulnerabilities in native code, OS access, and network connections that can lead to various attack methods such as man-in-the-middle attacks. It highlights the importance of recognizing stakeholders, assets, and potential threats, detailing issues like app security, data leakage, and the impact of rooting/jailbreaking. Moreover, it outlines key countermeasures for developers to enhance mobile security, including proper architecture, input validation, and remote data wipe capabilities.