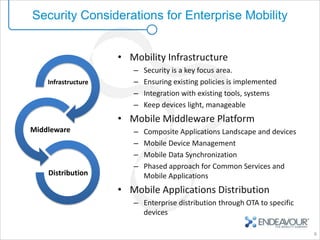
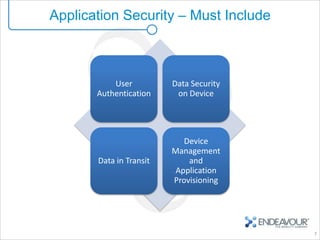
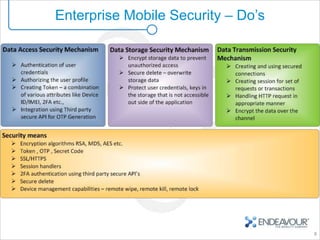
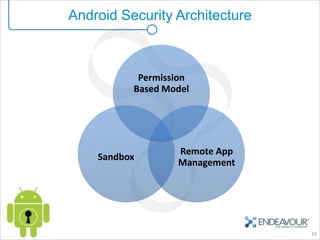
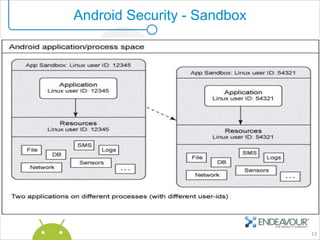
This document provides an overview of enterprise mobility and mobile security, with a focus on the Android platform. It discusses best practices for secure software development and the Android security architecture. The document outlines Android's permission-based security model and sandboxing approach. It also examines Android's attack surfaces and how enterprises can leverage features in newer Android versions like remote wiping, encryption, and device administration policies. The presentation concludes with an invitation for questions.