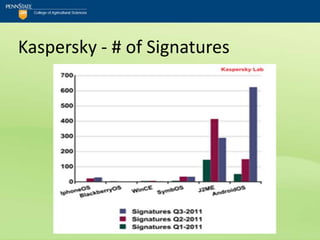
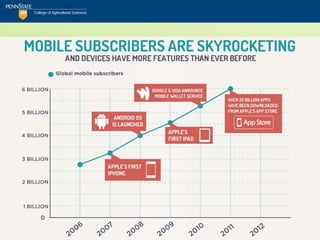
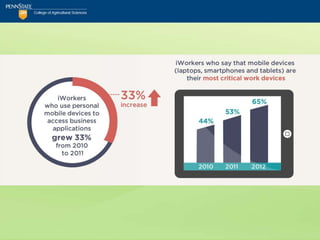
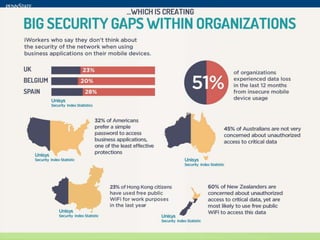
The document discusses the security challenges posed by mobile devices, emphasizing their intimate role in personal and professional lives while highlighting the risks associated with bring-your-own-device (BYOD) policies. It outlines various mobile operating systems' security features and vulnerabilities, particularly focusing on Android and its susceptibility to malware, compared to more secure options like Blackberry and iOS. The text includes security checklists and training recommendations for organizations to protect sensitive information in the face of increasing mobile device usage.









![Security Quotes
“Against the growing, unstoppable
backdrop of consumerisation and
BYOD [bring your own device], every
mobile device is a risk to business.”
Raimund Genes, Trend Micro CTO 2](https://image.slidesharecdn.com/netc2012mobilesecurityforsmartphonesandtablets-120531105639-phpapp01/85/NETC-2012_Mobile-Security-for-Smartphones-and-Tablets-pptx-13-320.jpg)

![Security Quotes
“I'm sure you've seen this scenario.
Halfway through [a] flight, a user
switches from super-critical pieces of
corporate work to checking out the app
they downloaded while waiting in the
airport terminal.”
Cameron Camp, ESET 4](https://image.slidesharecdn.com/netc2012mobilesecurityforsmartphonesandtablets-120531105639-phpapp01/85/NETC-2012_Mobile-Security-for-Smartphones-and-Tablets-pptx-15-320.jpg)

























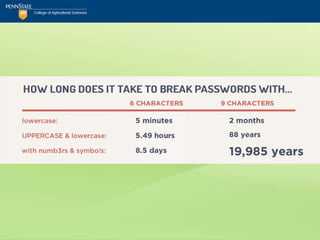
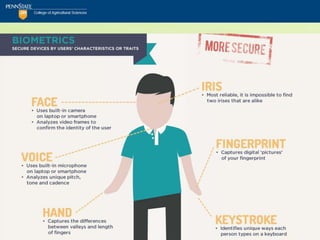

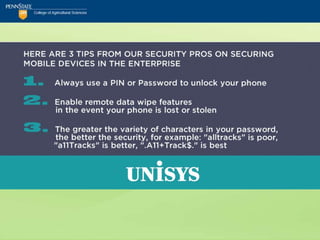




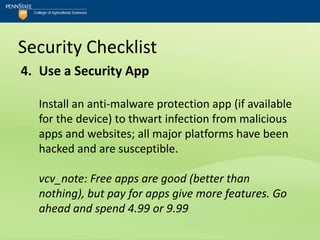
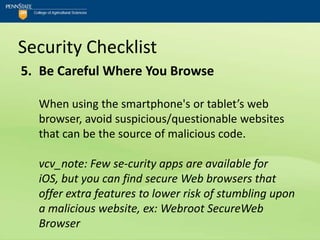




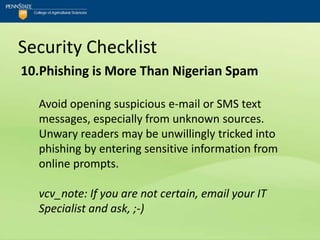

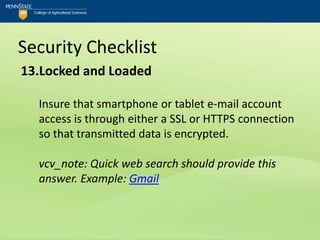
![Security Checklist
12.PIN Use “Good”; PIN Default “Bad”
Utilize a PIN to access voice-mail and avoid using
the carrier's default PIN setting.
vcv_note: Beyond the default...
Top ten iPhone passcodes:
[1234, 0000, 2580, 1111, 5555, 5683, 0852, 2222, 1
212, 1998] 11](https://image.slidesharecdn.com/netc2012mobilesecurityforsmartphonesandtablets-120531105639-phpapp01/85/NETC-2012_Mobile-Security-for-Smartphones-and-Tablets-pptx-64-320.jpg)