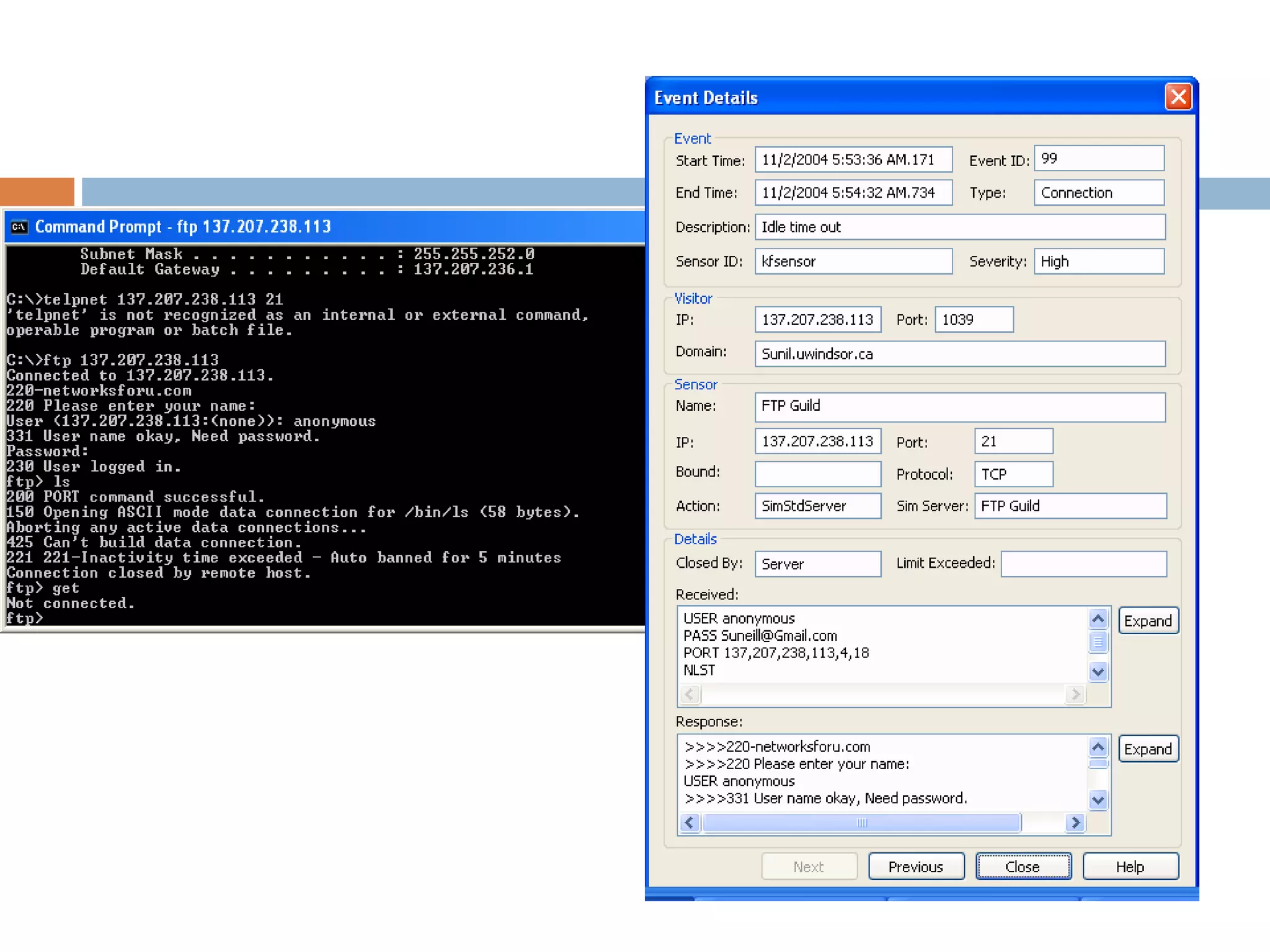
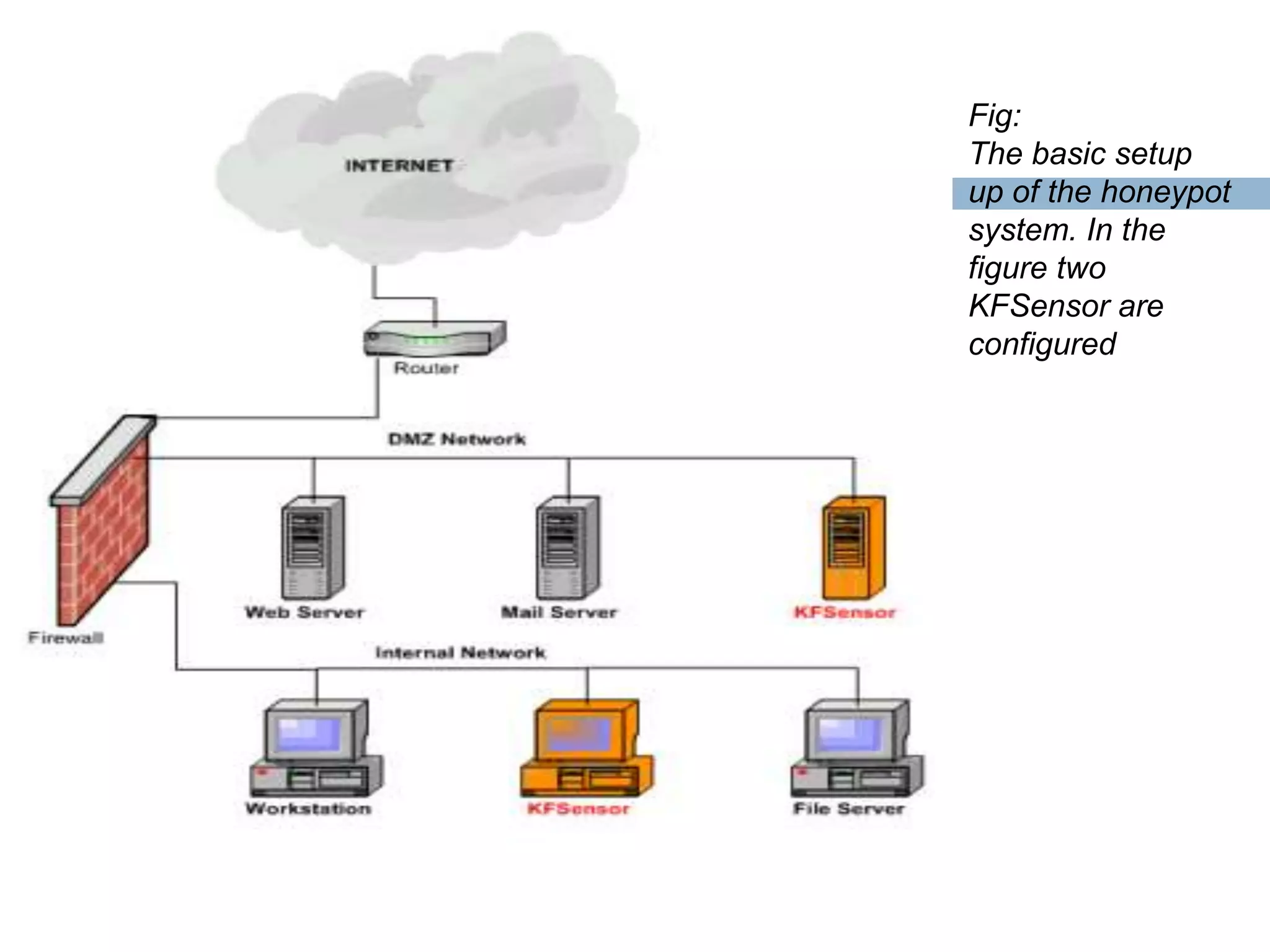
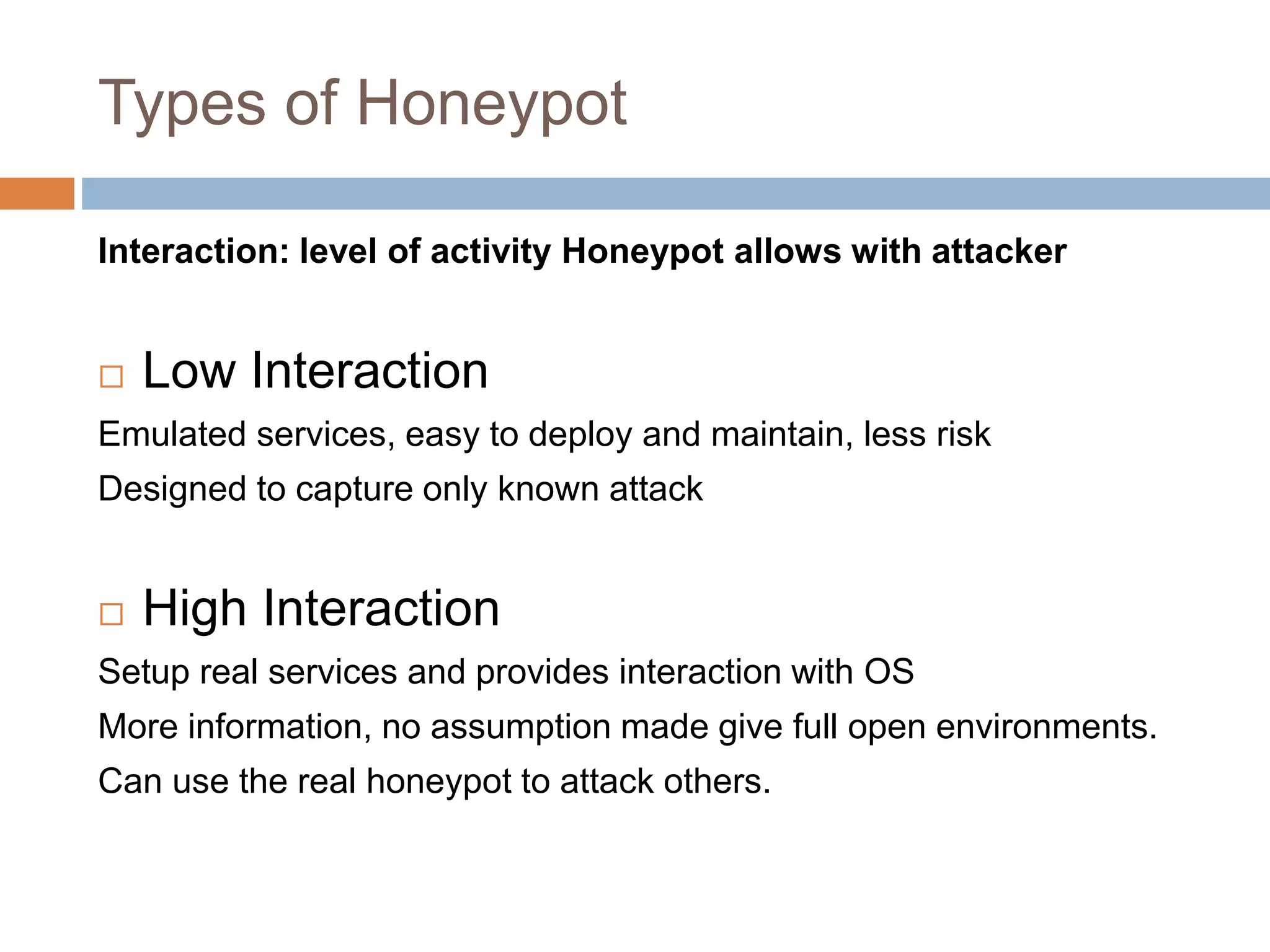
This document discusses KFSensor, a honeypot and intrusion detection system. It provides an overview of honeypot technology, the components and features of KFSensor, and how it was tested. KFSensor is a commercial low interaction honeypot solution that simulates vulnerable Windows services to detect and study hackers. It has a GUI management console for configuration and monitoring attacks in graphical formats.





![Installations
Download the application from the website
To install login as ADMINISTRATOR
C:kfsensorlogs – XML files
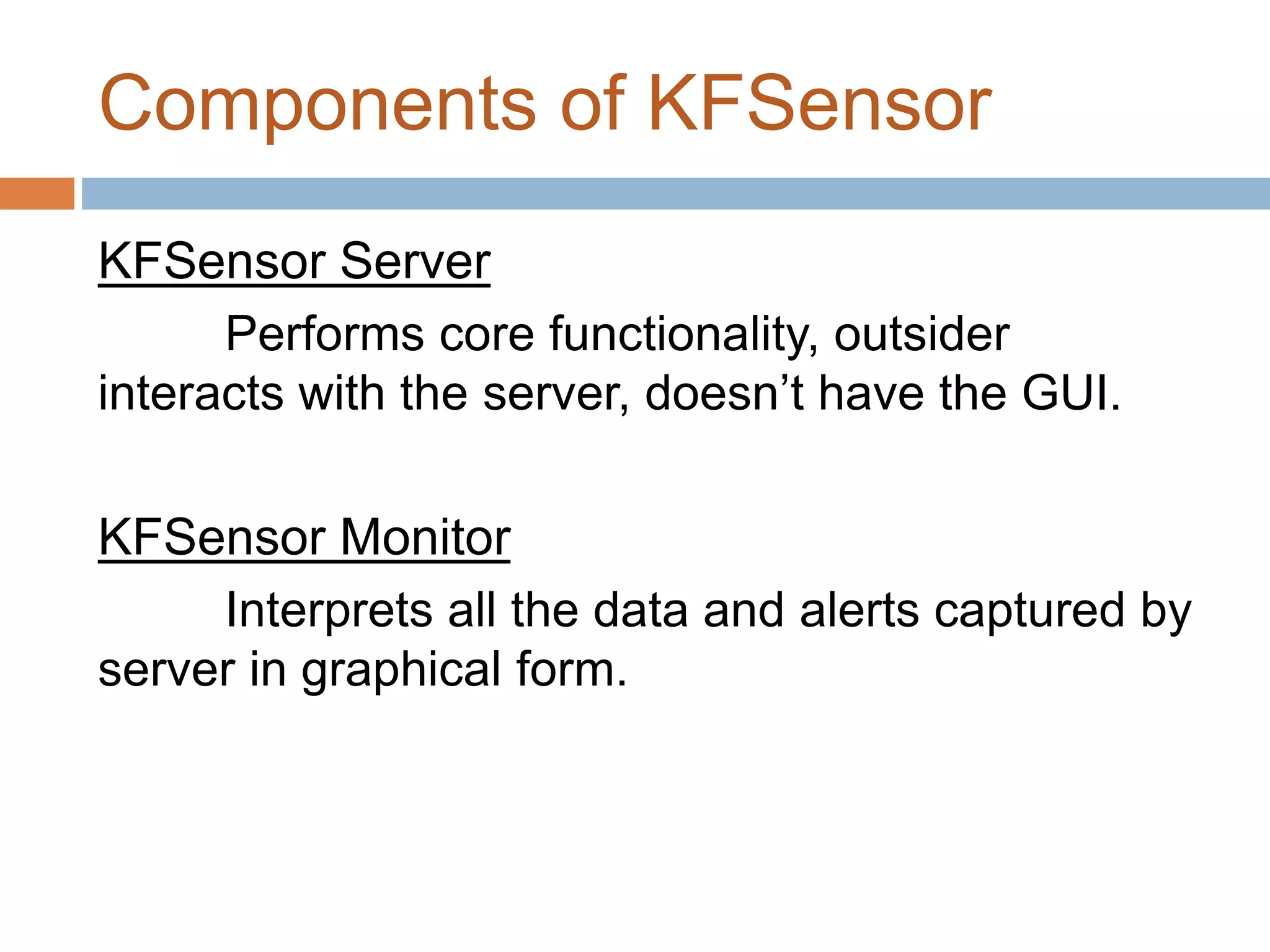
Running the KFSensor server – as daemon –
windows service. [kfsnserve.exe]
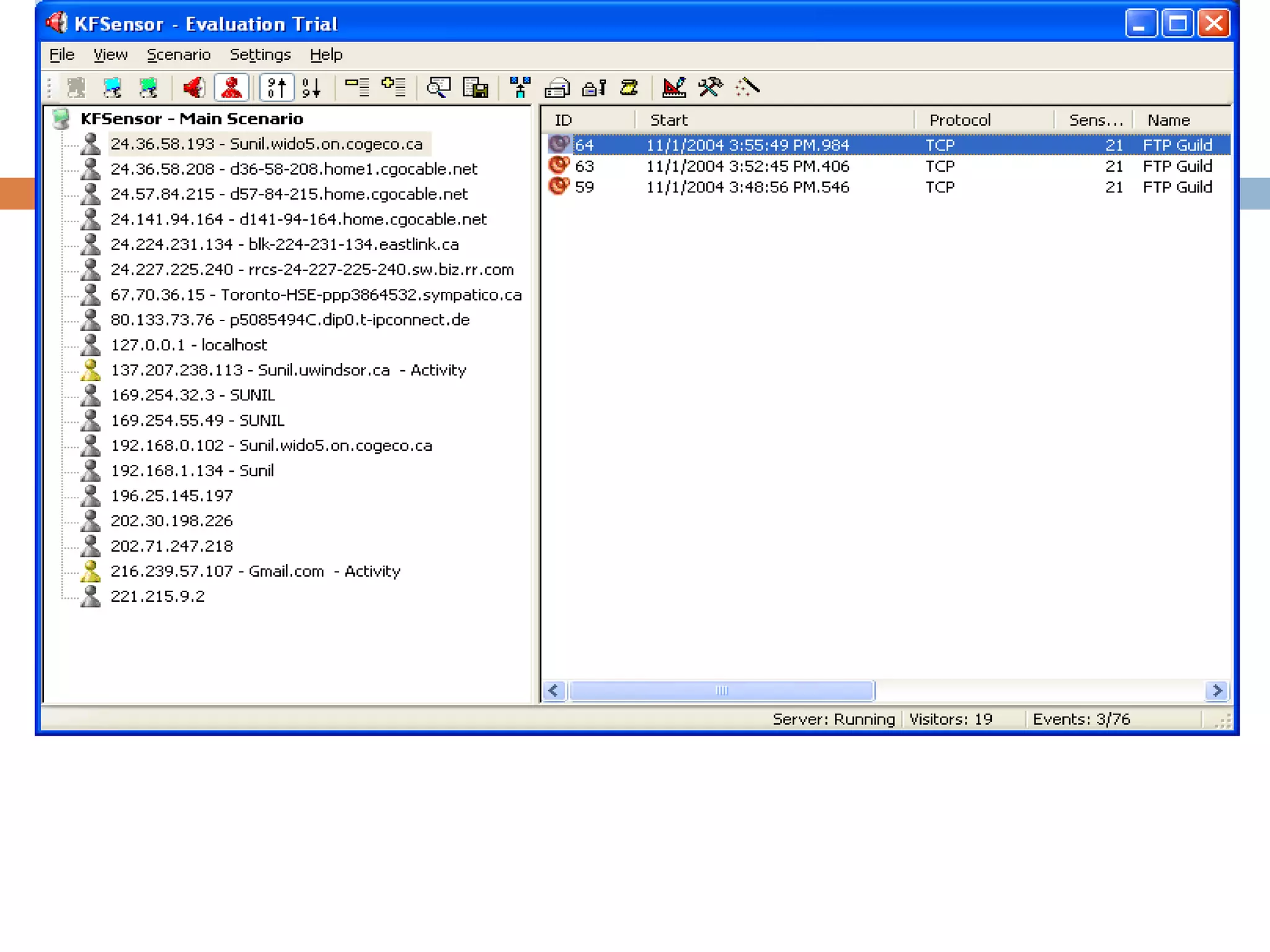
Open up the KFSensor monitor - GUI](https://image.slidesharecdn.com/kfsensor1-180415154329/75/Kf-sensor1-9-2048.jpg)
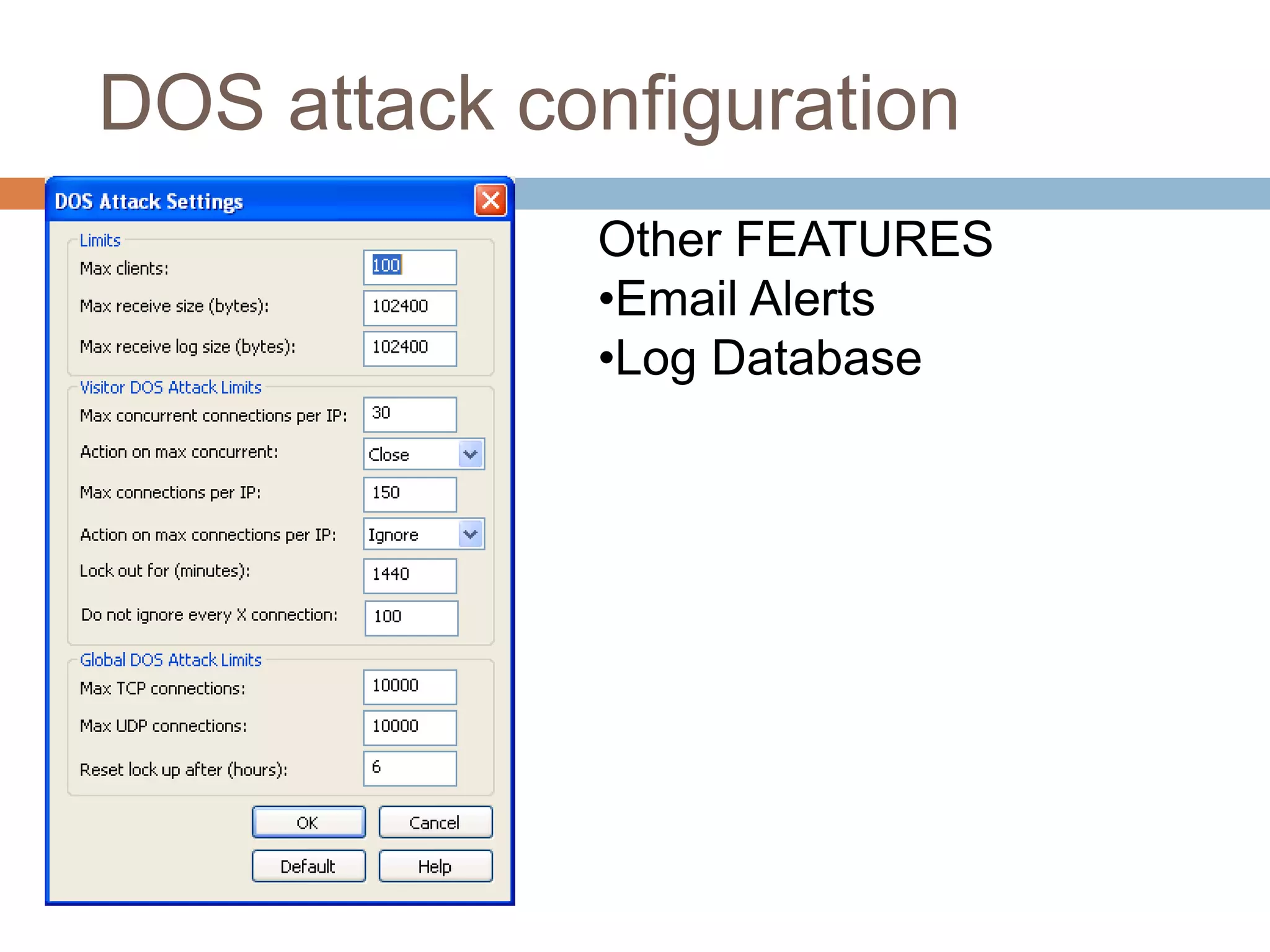
![Features
File Menu
Export [HTML, XML, TSV or CSV ], Service
View Menu
Ports View, Visitors View
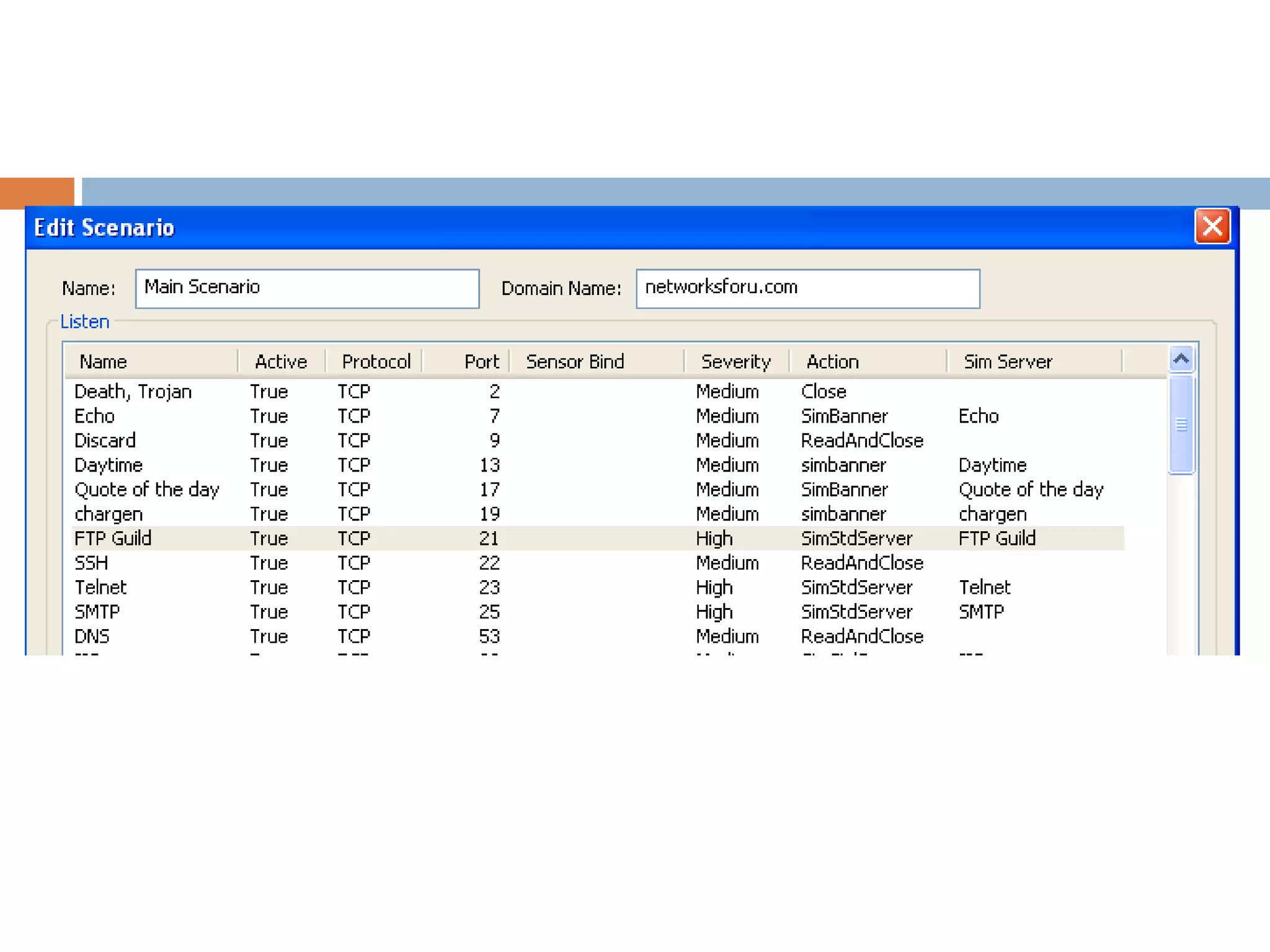
Editing Scenarios
Editing Listens, Edit Rules, Sim Server](https://image.slidesharecdn.com/kfsensor1-180415154329/75/Kf-sensor1-12-2048.jpg)