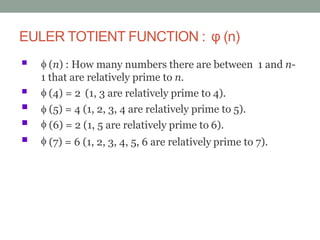
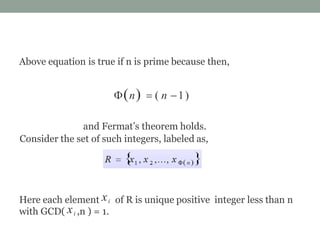
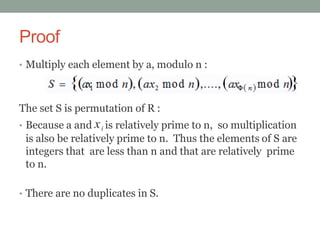
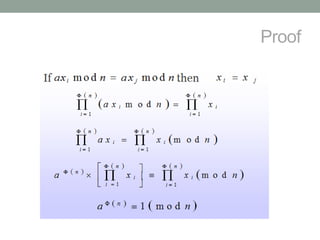
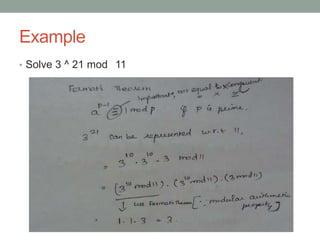
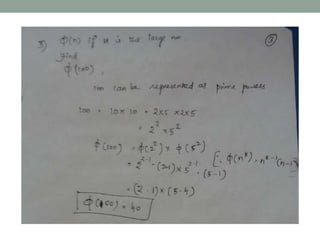
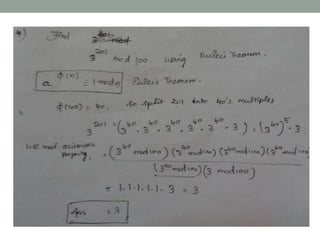
This document discusses Fermat's theorem and Euler's theorem, which are related theorems about integers modulo prime numbers. It provides proofs of both theorems and explains their applications. It also defines Euler's totient function φ(n) and provides examples to demonstrate how it can be used to calculate φ(n) for composite numbers.



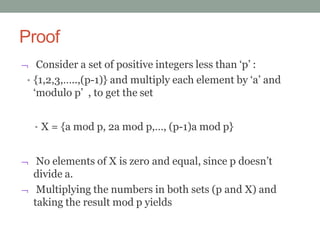
![Proof (Contd.,)
• Multiplying the numbers in both sets (p and X) and taking
the result mod p yields
• a * 2a *…* (p-1)a [1 * 2 * 3 *…* (p-1)] (mod p)
• a p 1
( p 1 ) ! ( p 1) ! ( mod p)
• Thus on equating (p-1)! term from both the sides, since it
is relatively prime to p, result becomes,
An alternative form of Fermat’s Theorem is given as
1 ( m o d p)
a p
a ( m o d p )
a p 1](https://image.slidesharecdn.com/fermatandeulertheorem-201006042553/85/Fermat-and-euler-theorem-5-320.jpg)