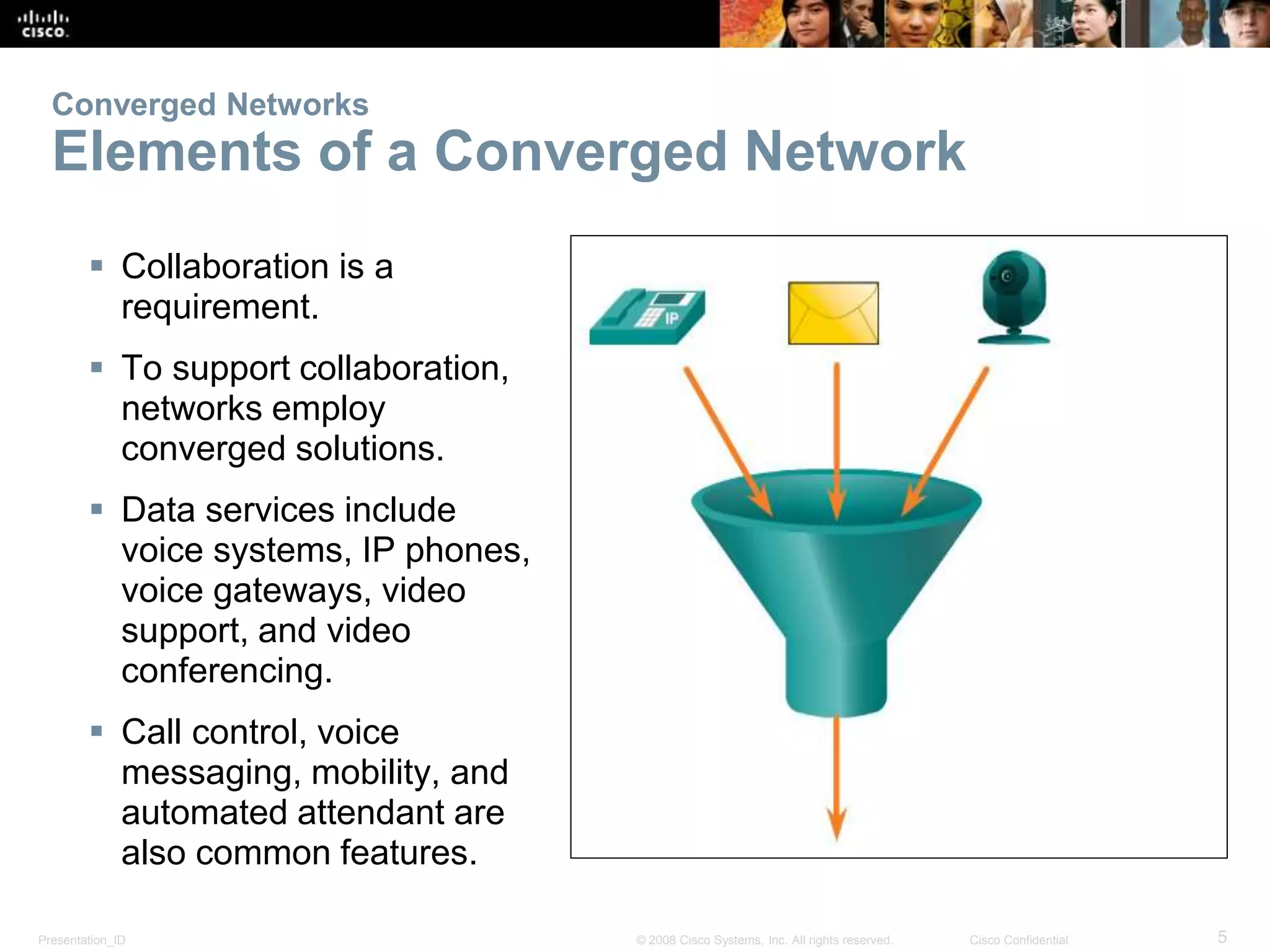
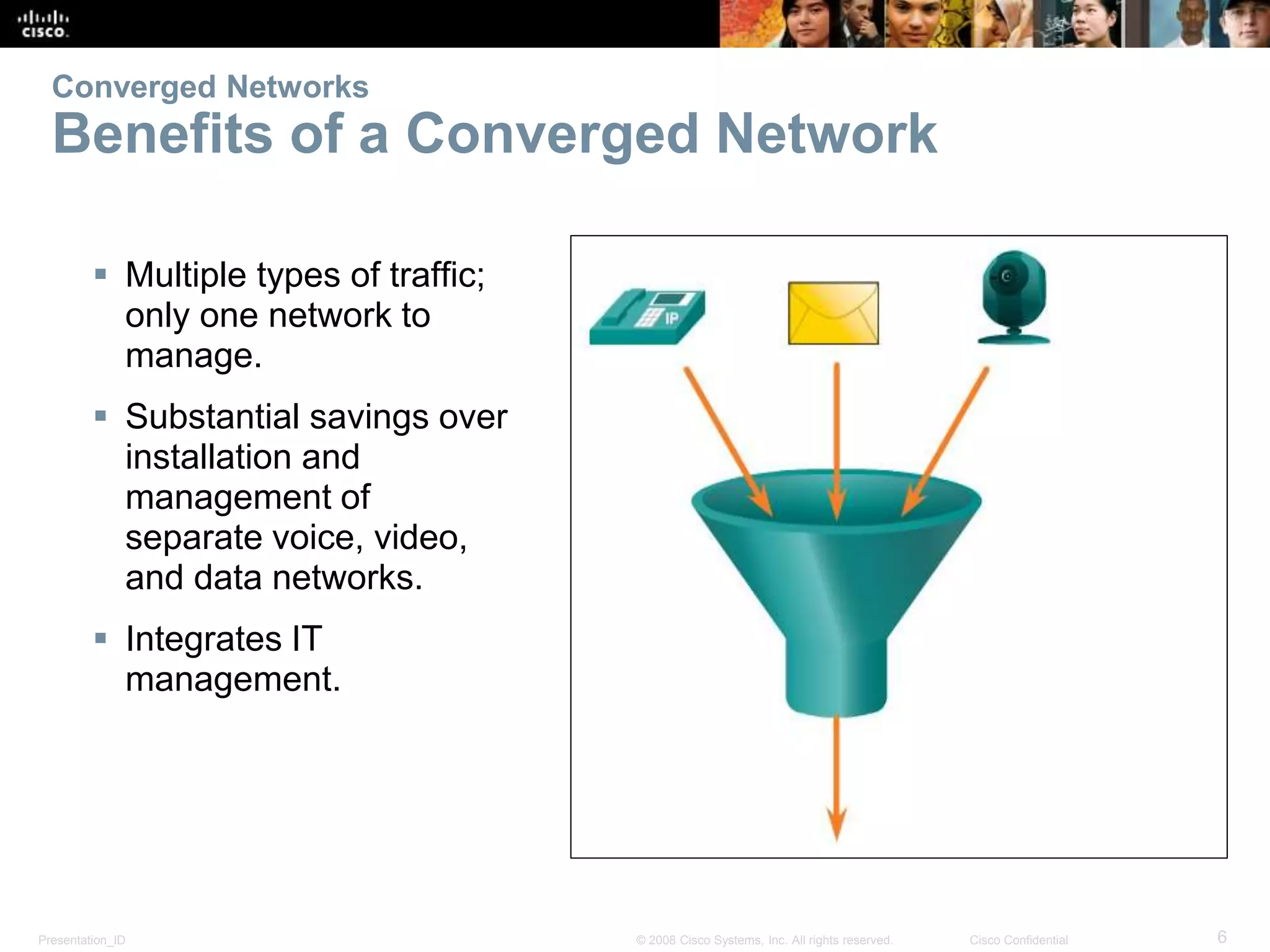
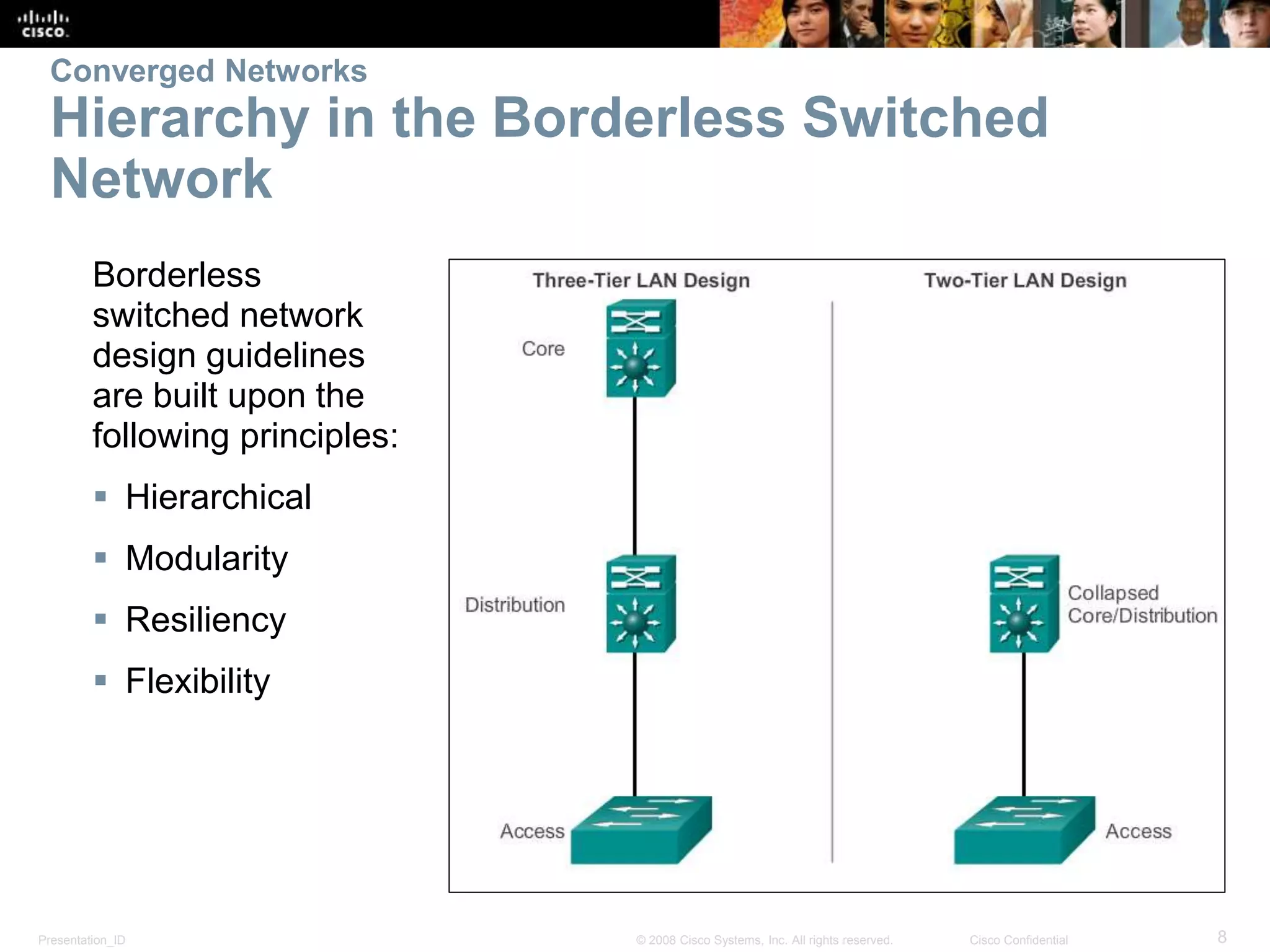
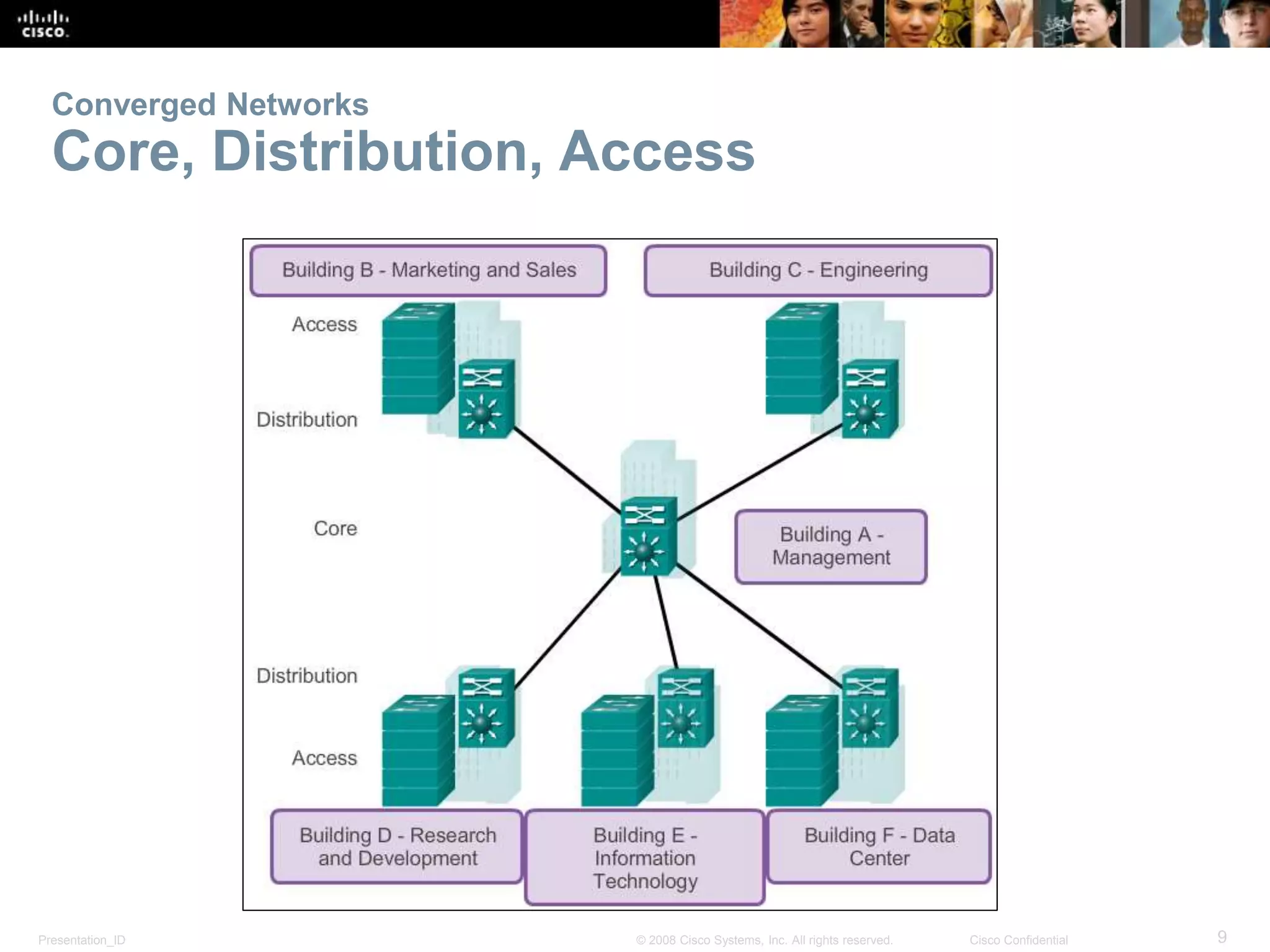
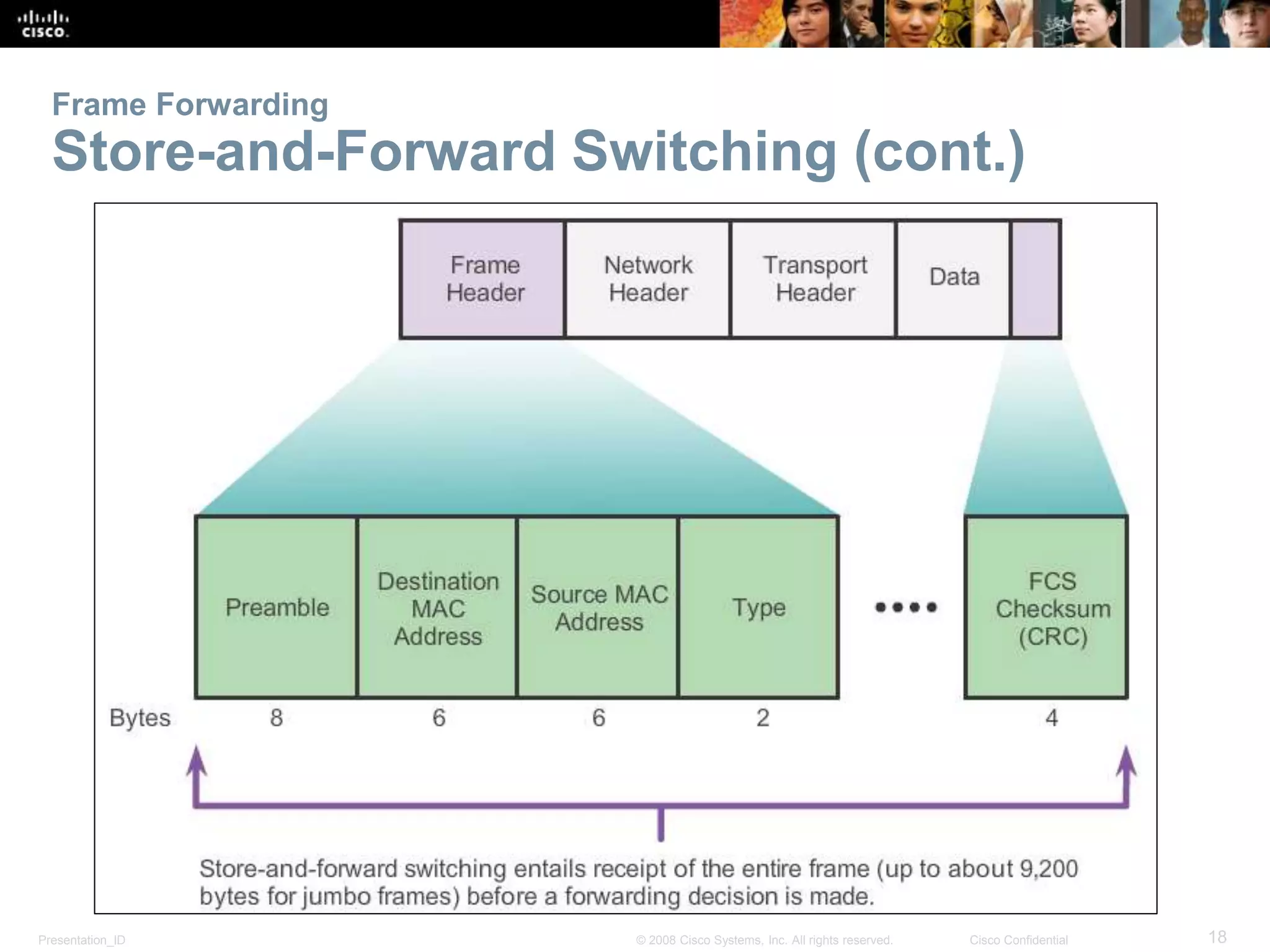
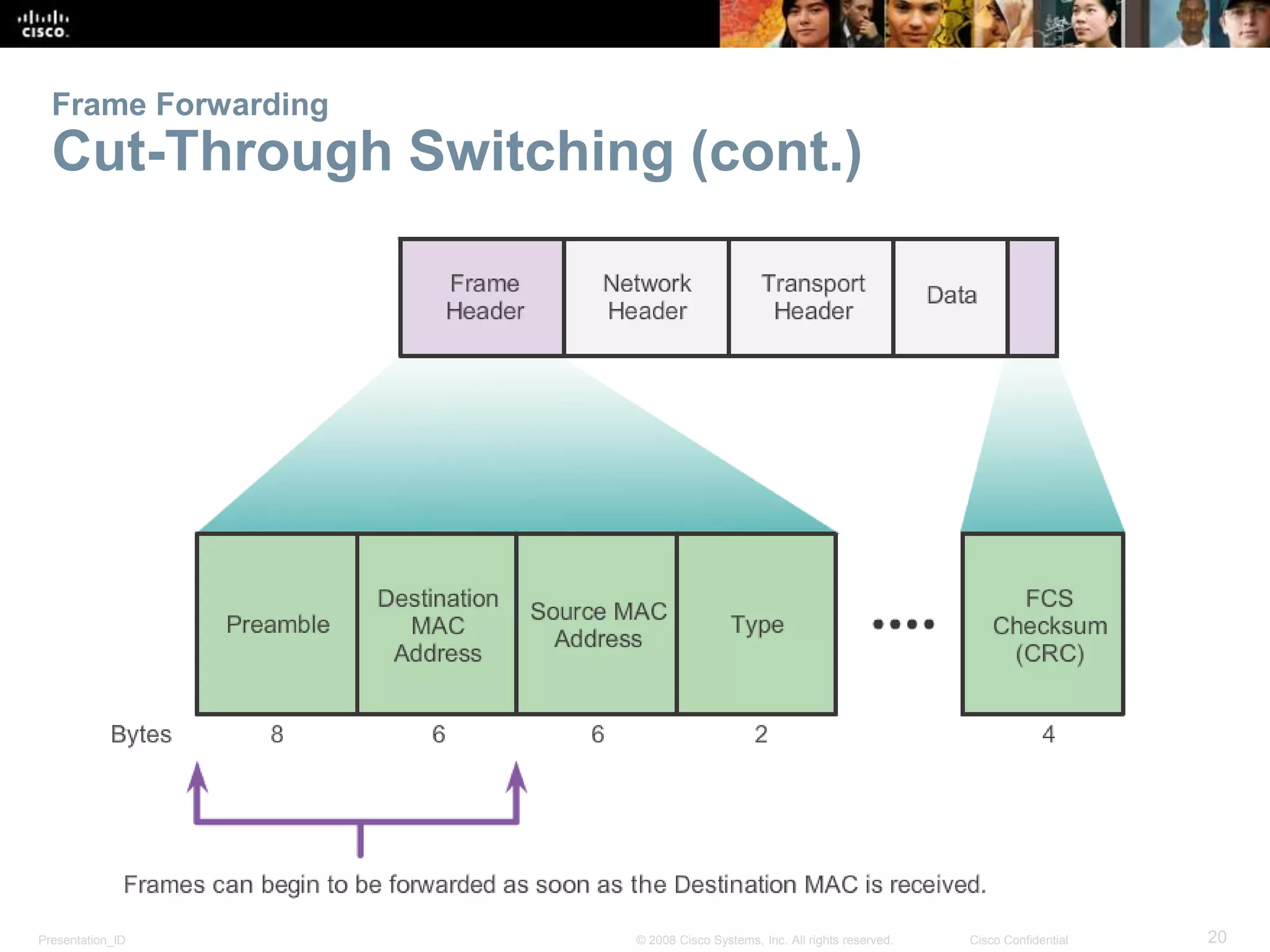
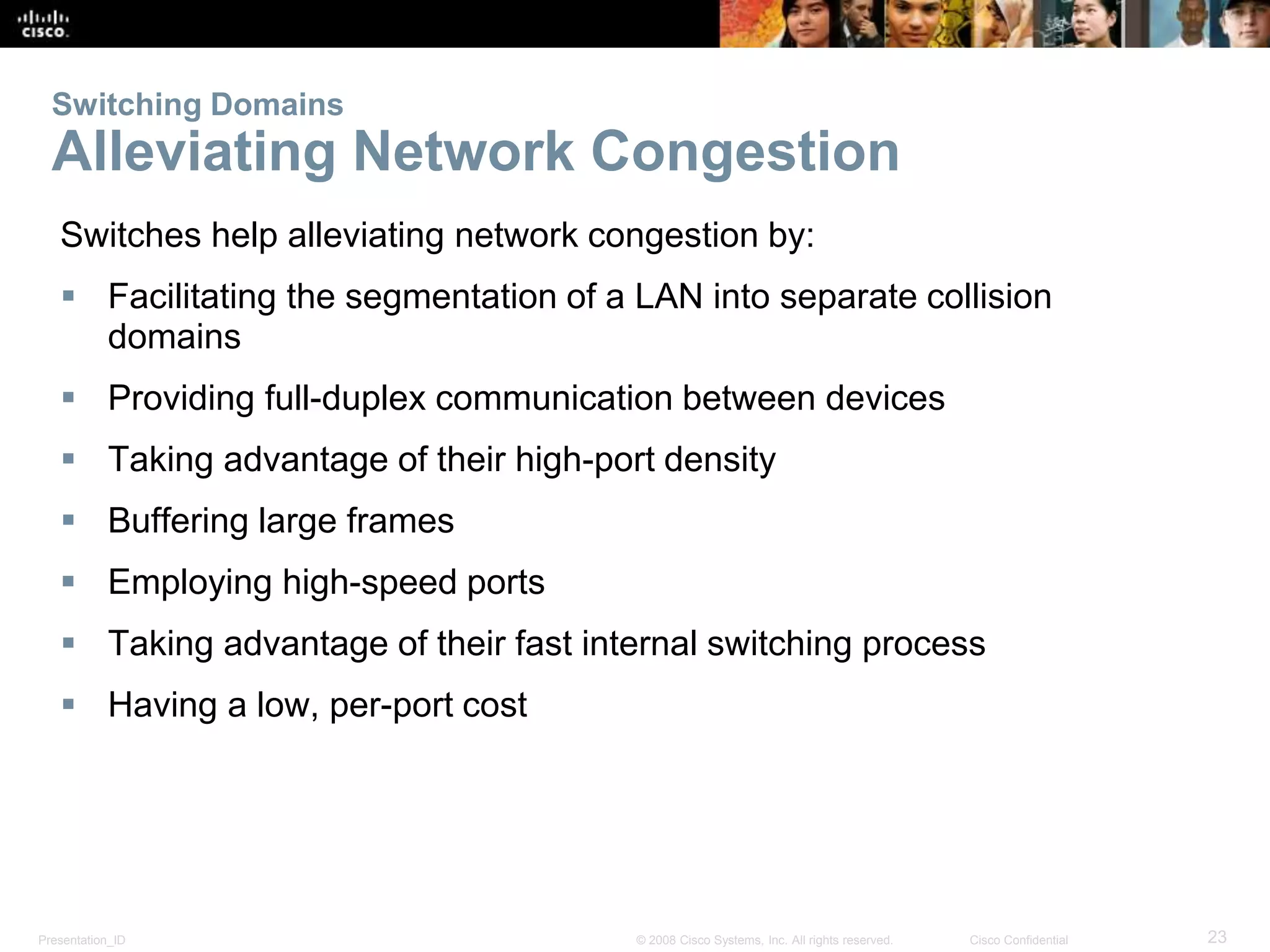
This document covers the fundamentals of switched networks, emphasizing the convergence of data, voice, and video for enhanced network efficiency. It details the importance of switches in managing traffic, collision, and broadcast domains while highlighting the Cisco borderless network architecture. The chapter concludes with an overview of different switching methods and the benefits of a hierarchical design model for optimized network performance.