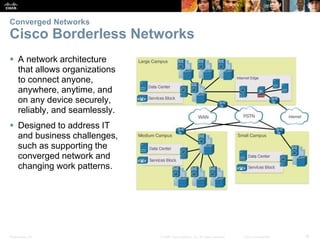
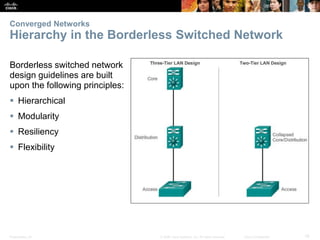
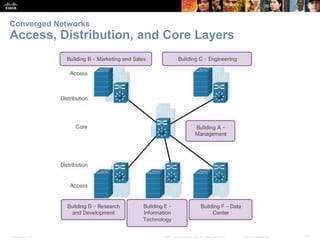
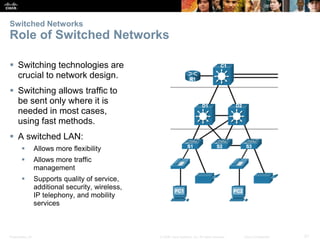
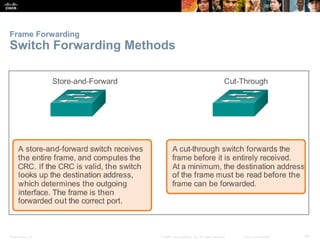
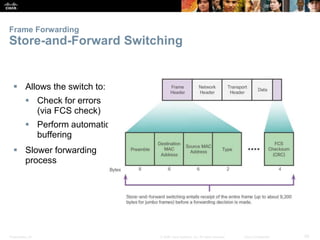
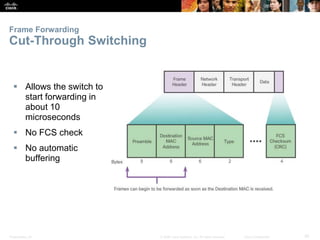
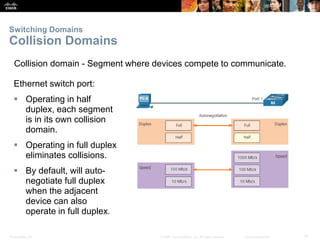
The document is a chapter from a Cisco networking textbook that covers switched networks. It discusses how converged networks support voice, video, and data on a single network. The chapter describes the hierarchical design of access, distribution, and core layers. It also explains how switches dynamically learn MAC addresses to populate their tables and forward frames via cut-through or store-and-forward switching. Collision and broadcast domains are defined, and how switches can alleviate network congestion.