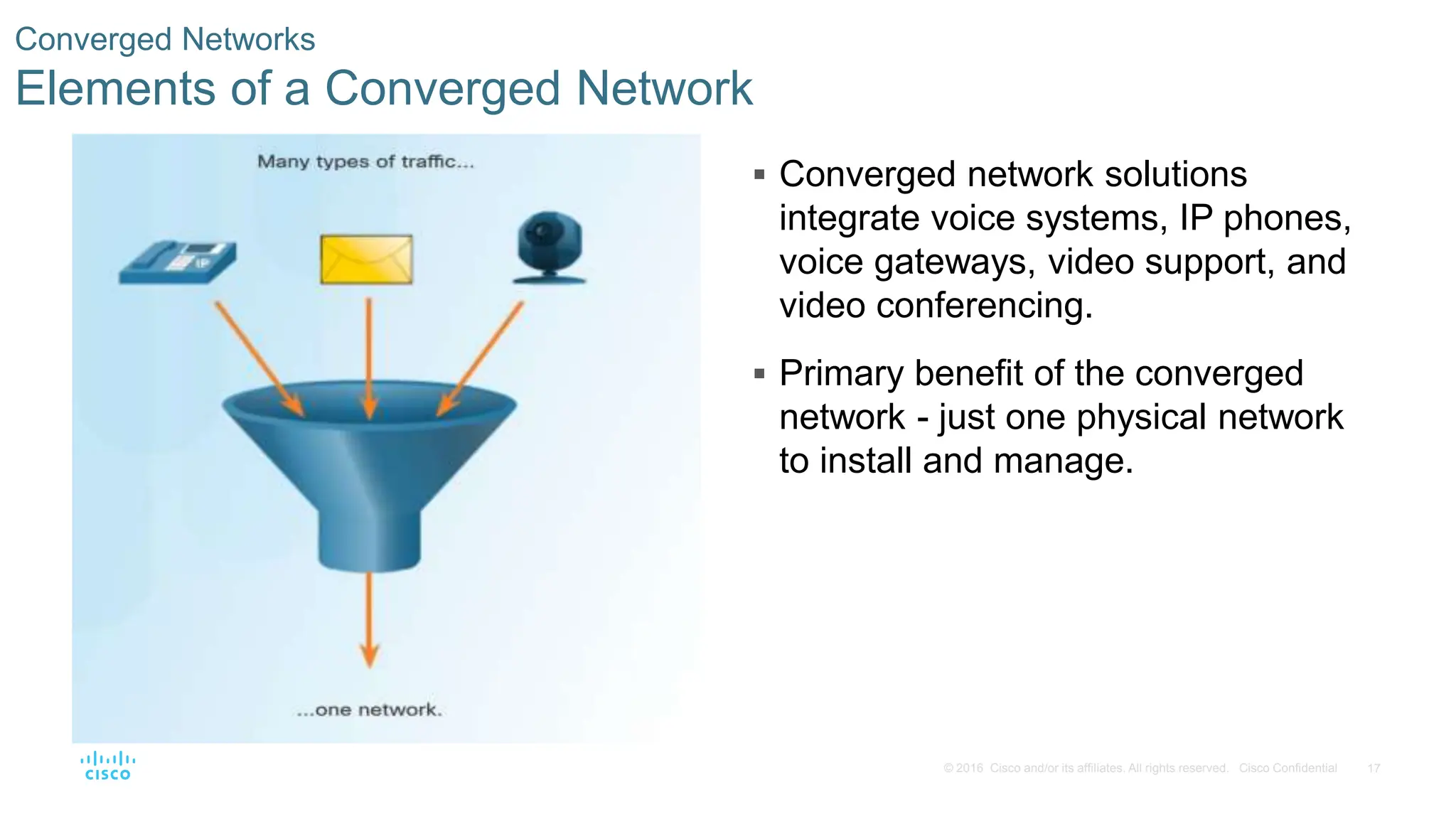
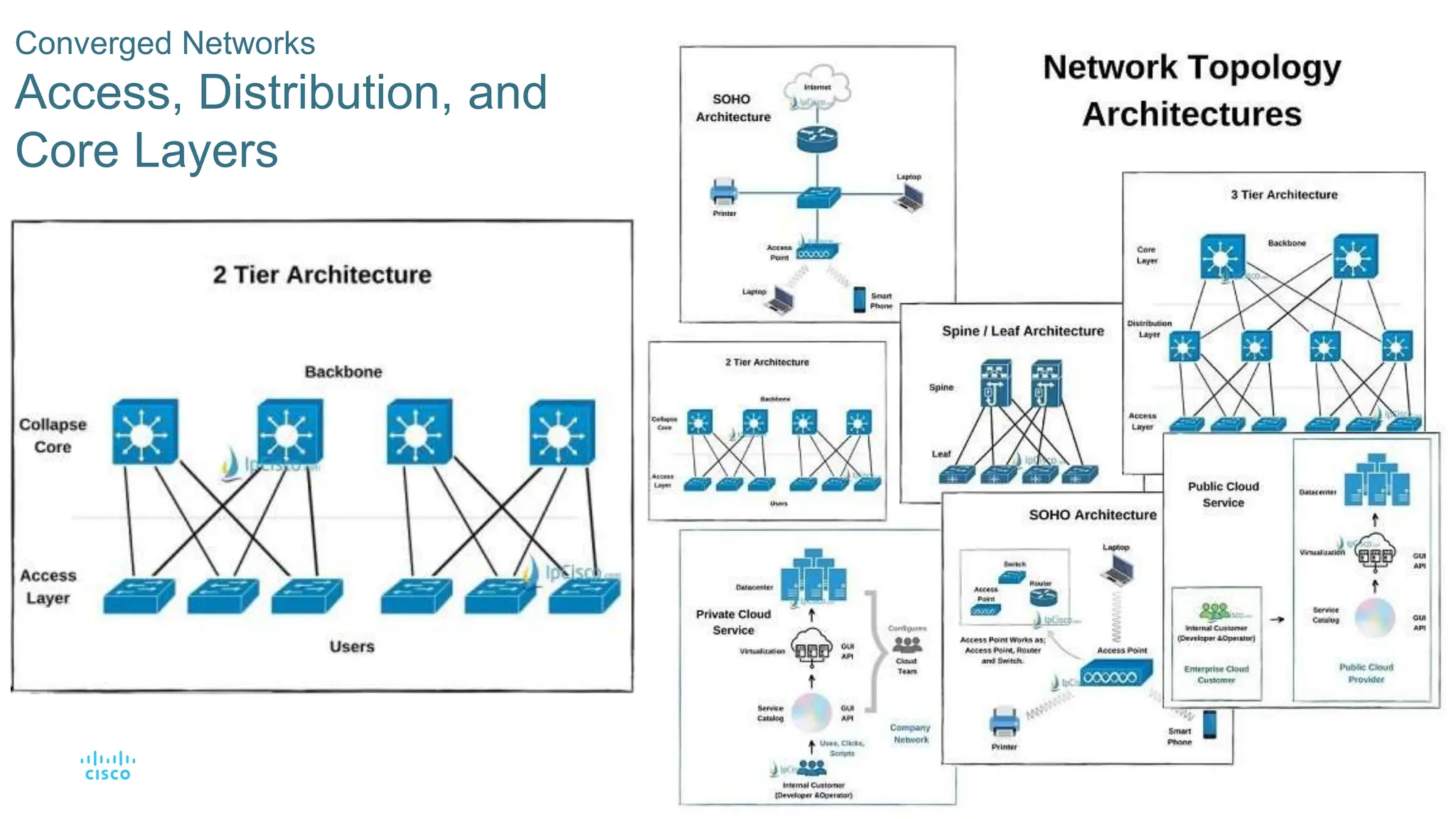
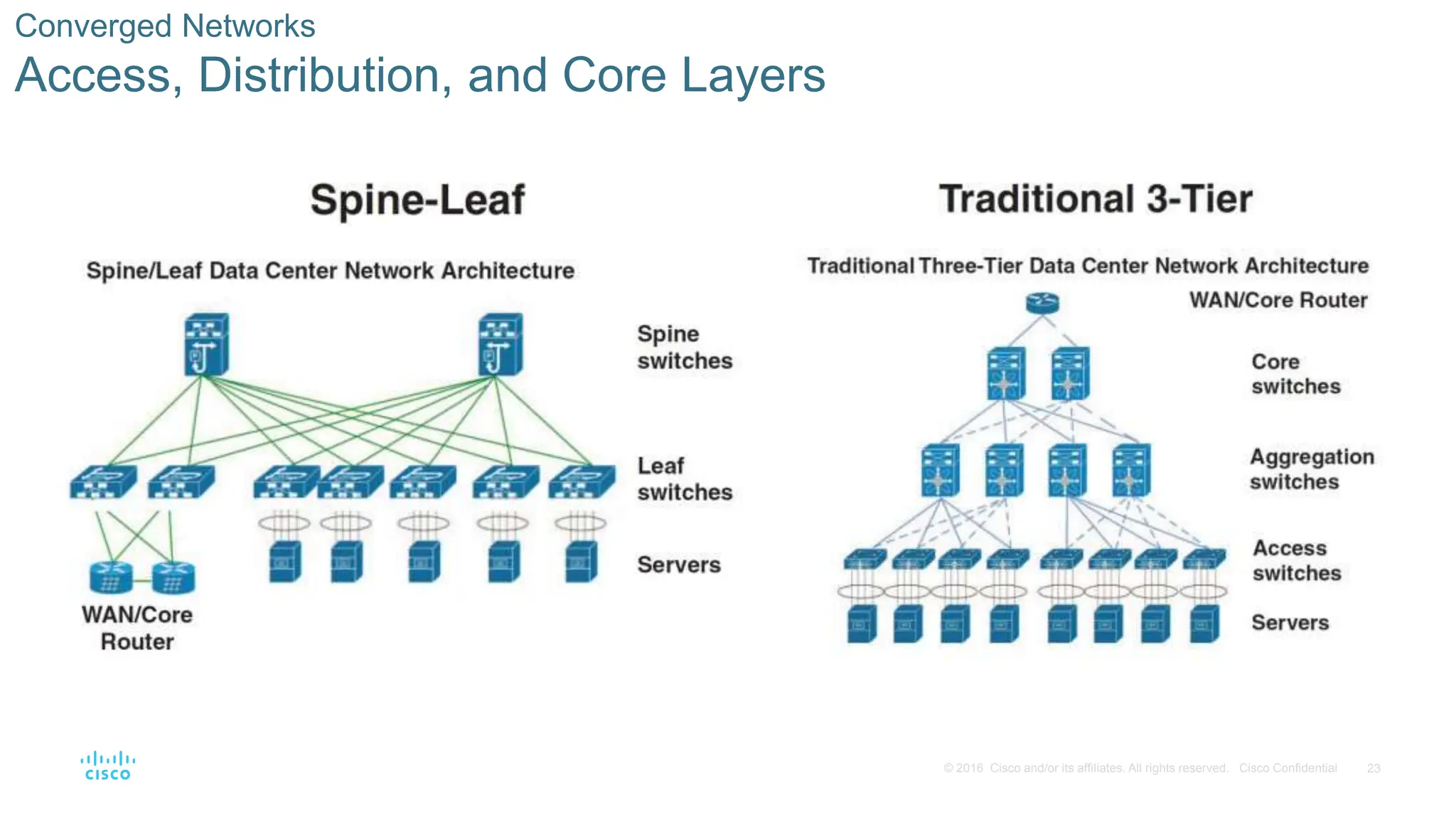
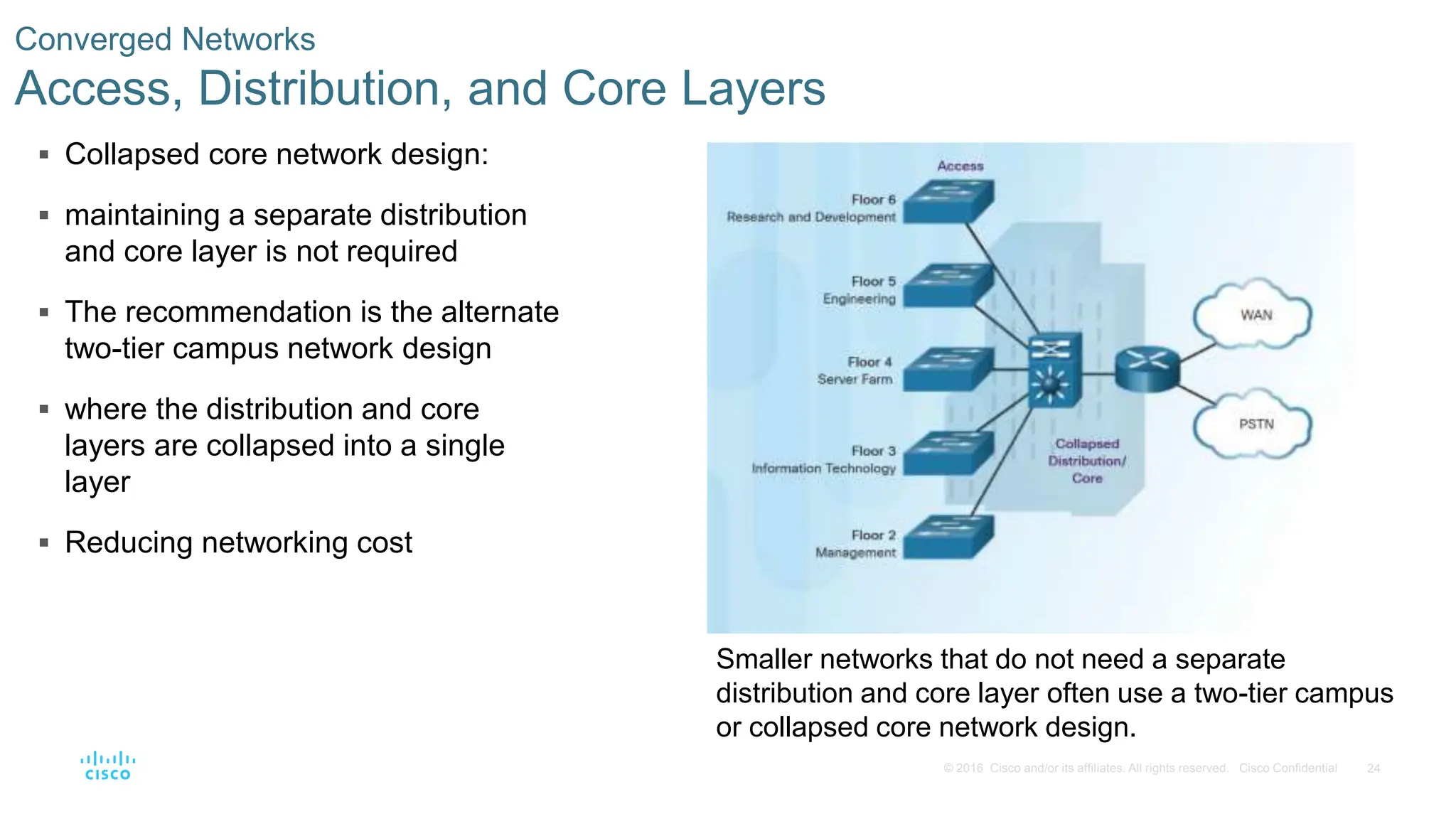
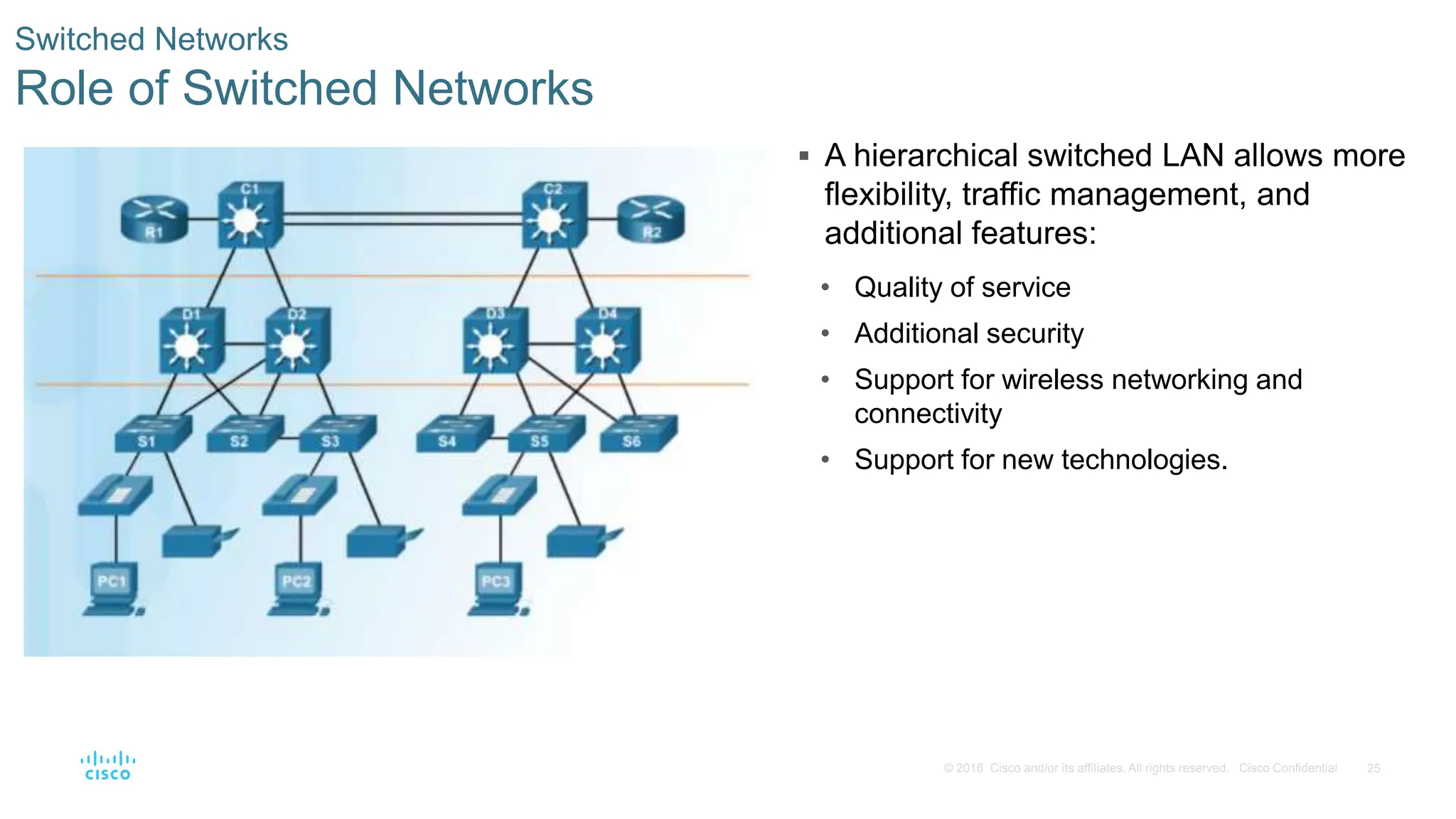
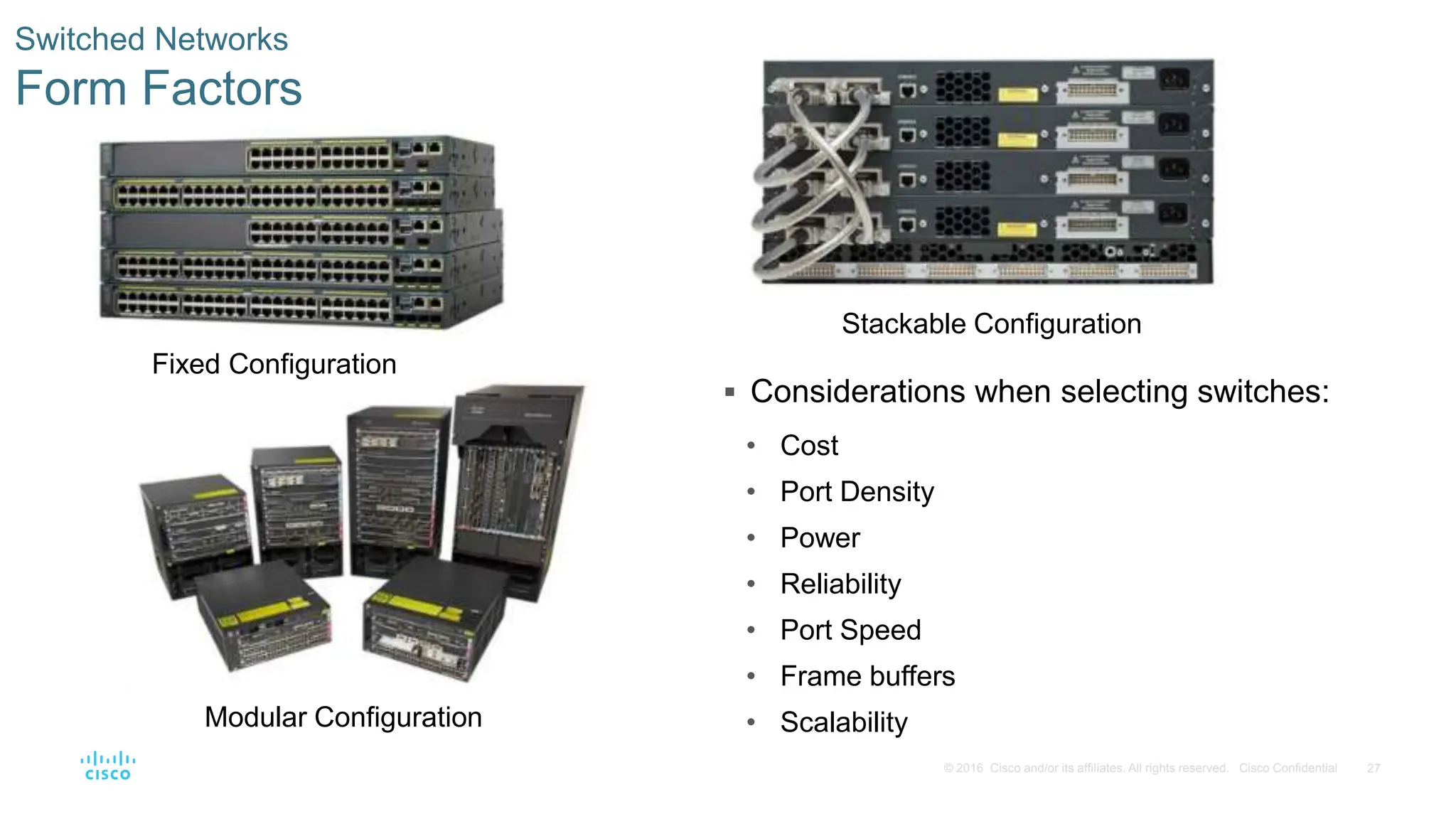
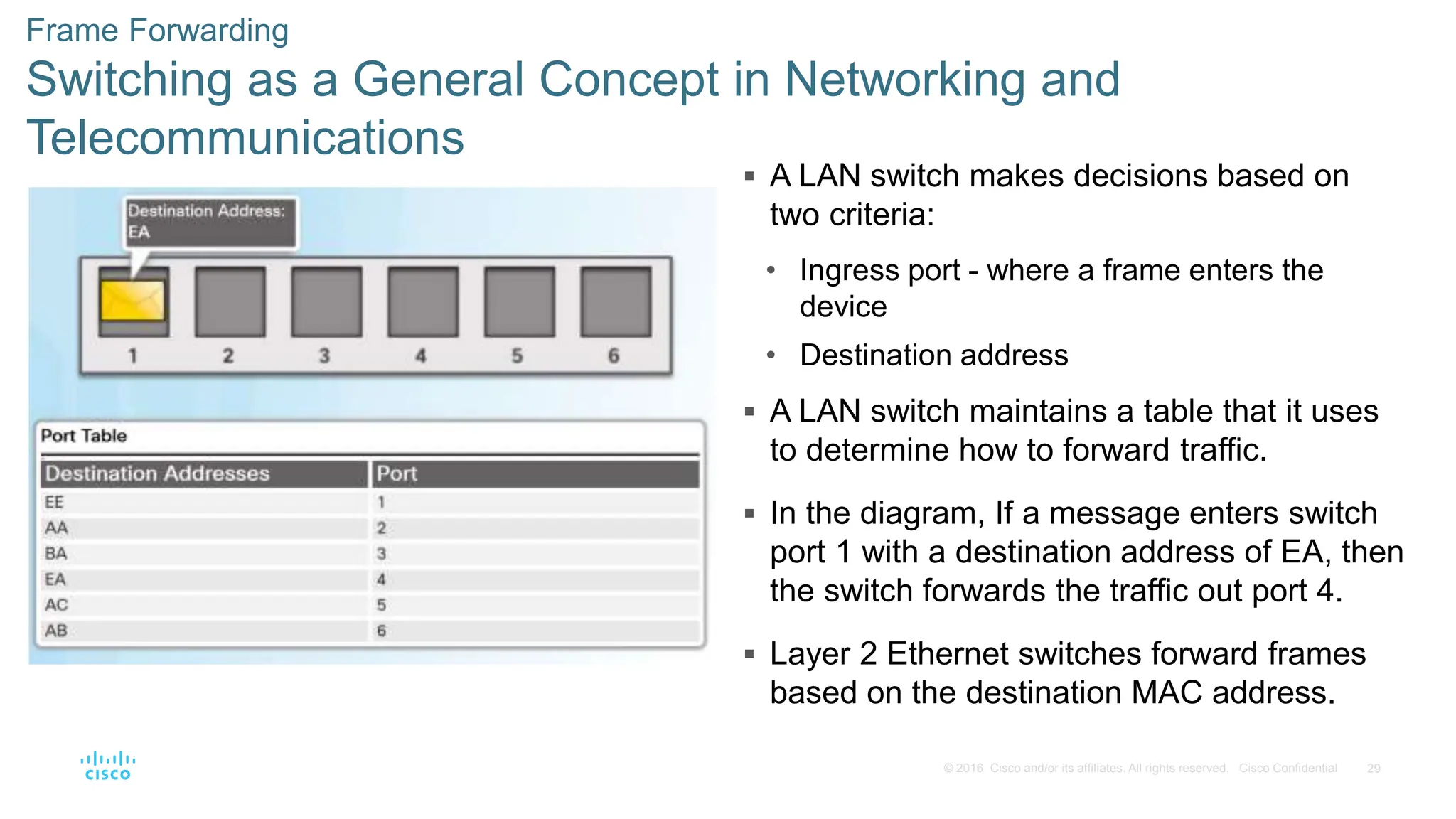
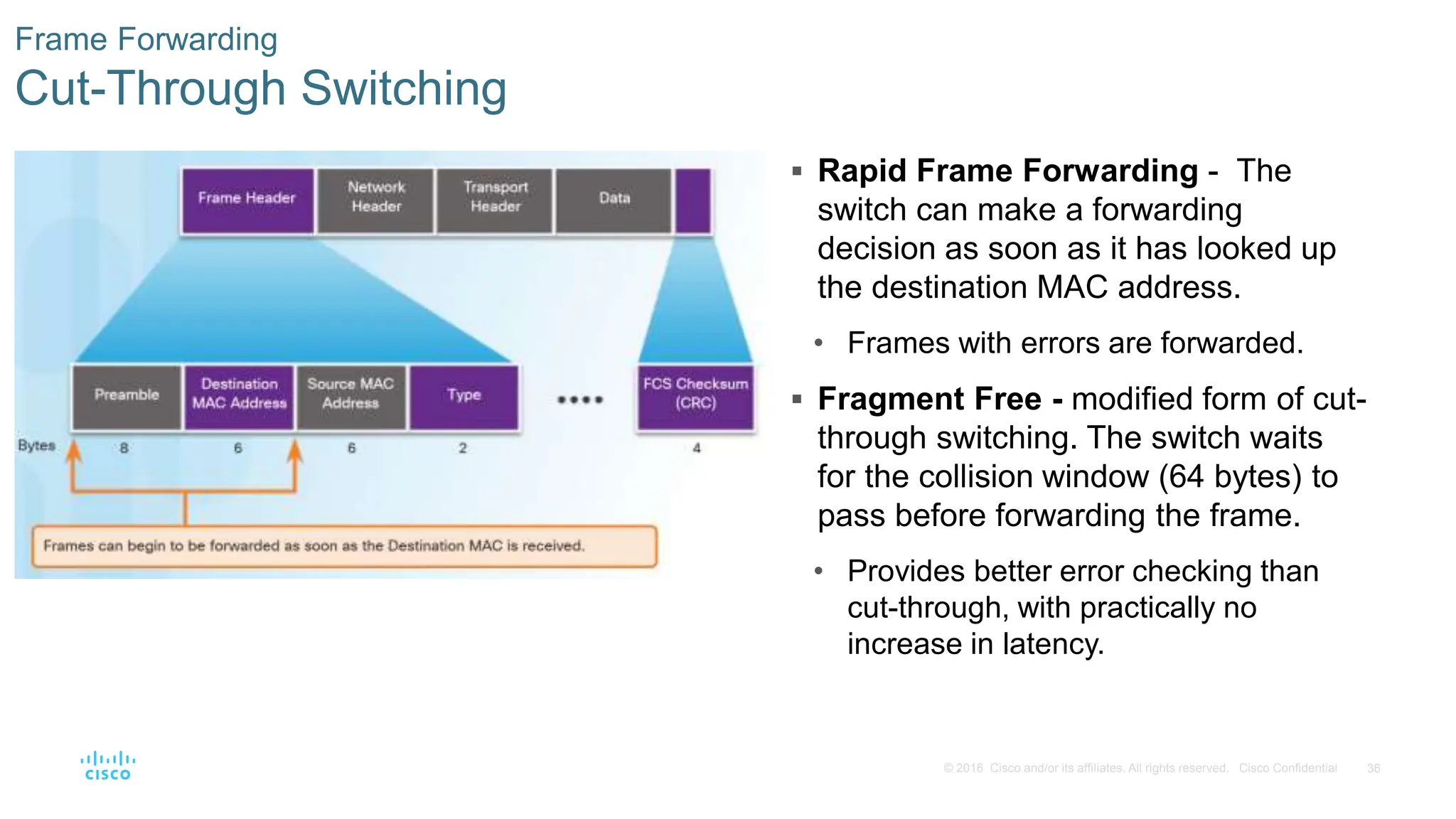
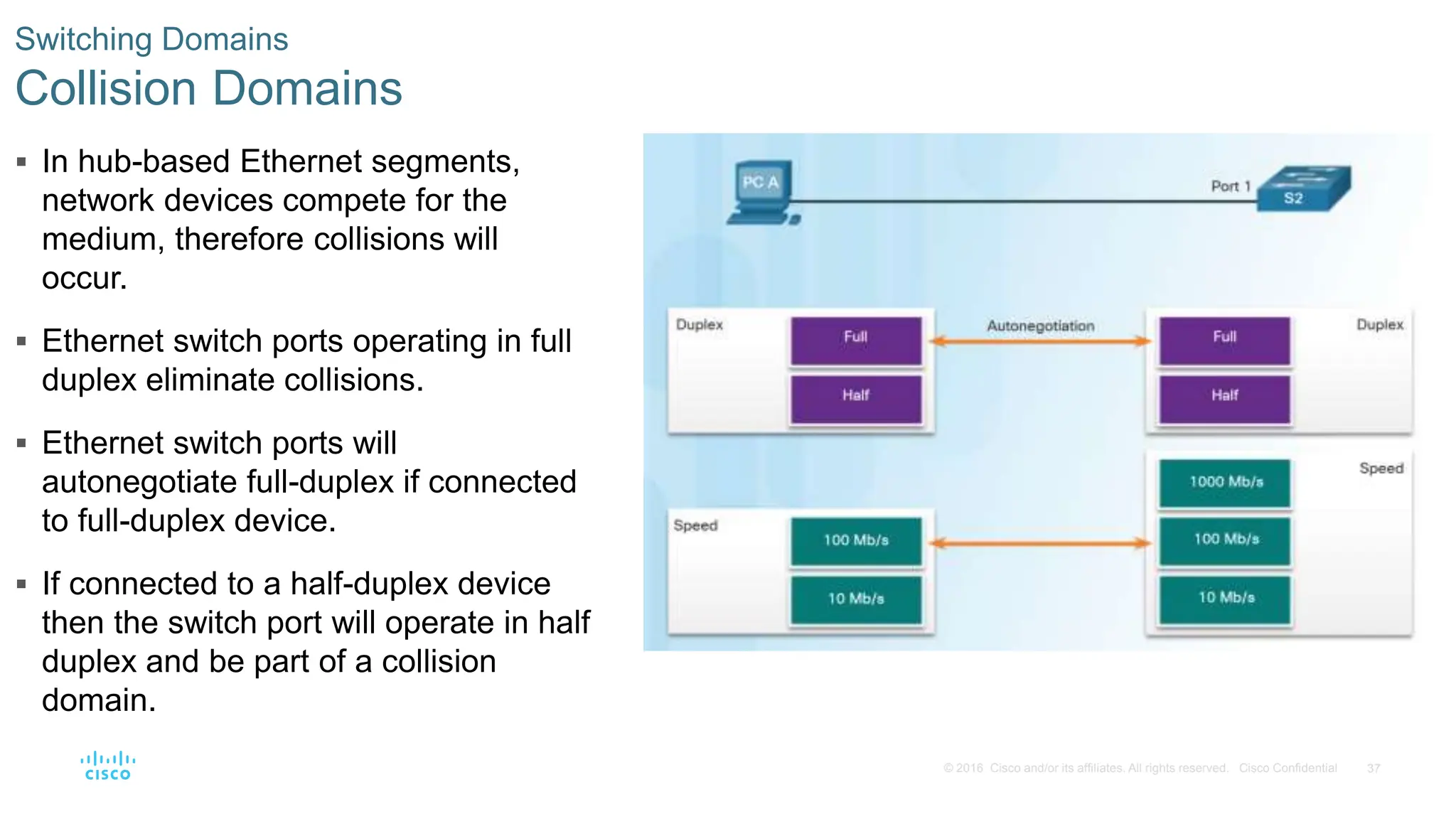
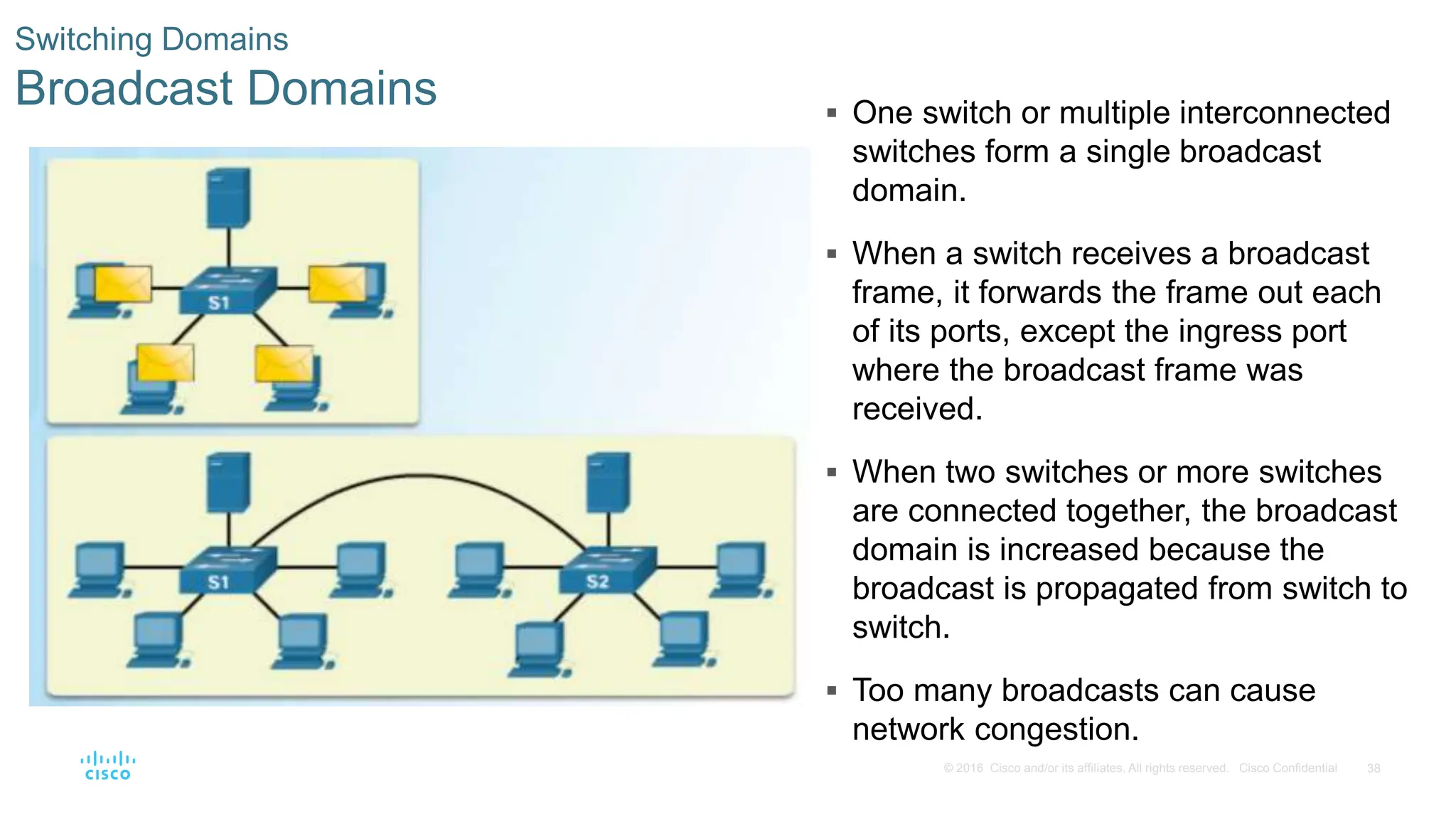
This document provides an overview of switched networks and frame forwarding in switches. It discusses how switches build MAC address tables to forward frames based on destination MAC addresses. Switches dynamically learn source MAC addresses and associated ports from incoming frames and populate their tables. The document also covers converged networks that integrate voice, video, and data on a single network, as well as hierarchical network designs with access, distribution and core layers.