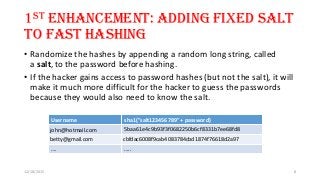
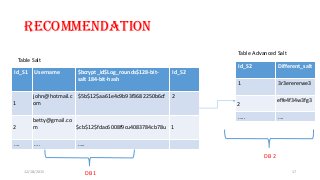
The document provides recommendations for securely storing user passwords. It recommends using bcrypt or PBKDF2 hashing with per-user salting to hash passwords before storing in a database. Bcrypt and PBKDF2 are slower algorithms that help protect against brute force and rainbow table attacks. The document also recommends storing the salt in a separate column to prevent attackers from cracking multiple passwords at once if the database is breached.