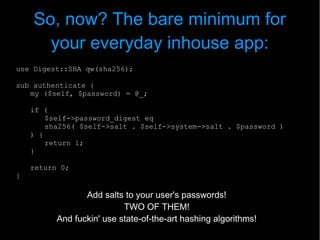
The document discusses best practices for handling user credentials in web applications, emphasizing the dangers of poor storage and transmission methods for passwords. It advocates for using strong hashing algorithms, salting, key derivation functions, and secure transmission protocols like SSL/TLS to protect user data. Additionally, it recommends educating users about password strength and proper handling of web services to mitigate security risks.