The document discusses web application security focused on authentication, outlining threats, vulnerabilities, and strategies for strong authentication. It highlights issues such as weak passwords, the importance of proper password management, and risks associated with common authentication methods. Best practices are provided to enhance security against various attacks, emphasizing user education and robust management processes.












![Authentication
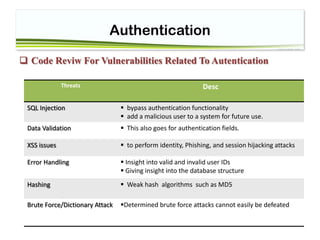
Weak Passwords and password functionality
Passwords should be complex in composition
checks should be done on the backend/server side of the application
Simply checking that a password is not NULL is not sufficient:
Tip : operator == casts between two different types if they are different, while the === operator
performs a 'typesafe comparison'.
$pass=$_GET[‘pass’]
If($pass===null)
// echo error
1 === 1: true
1 == 1: true
1 === "1": false // 1 is an integer, "1" is a string
1 == "1": true // "1" gets casted to an integer, which is](https://image.slidesharecdn.com/session4-authentication-180425045731/85/Session4-Authentication-13-320.jpg)
![Authentication
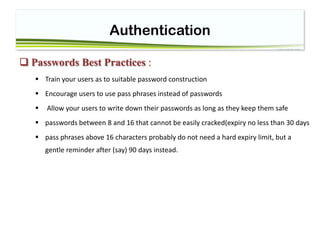
Good Passwords
Rules Reg ExP
at least: 1 Uppercase character (A-Z) ^[a-z]$
at least: 1 Lowercase character (a-z) ^[A-Z]$
at least: 1 digit (0-9) ^[0-9]$
at least one special character (!"£$%&...) [!"£$%^&*()]
a defined minimum length (8 chars) ^[a-z]{3,5}$
a defined maximum length (as with all external input) ^[a-z]{3,5}$
no contiguous characters (123abcd)
not more than 2 identical characters in a row (1111) ^(([a-z0-9])2?(?!2))+$](https://image.slidesharecdn.com/session4-authentication-180425045731/85/Session4-Authentication-14-320.jpg)