- The document provides an overview of reconnaissance techniques for penetration testing and bug bounty hunting.
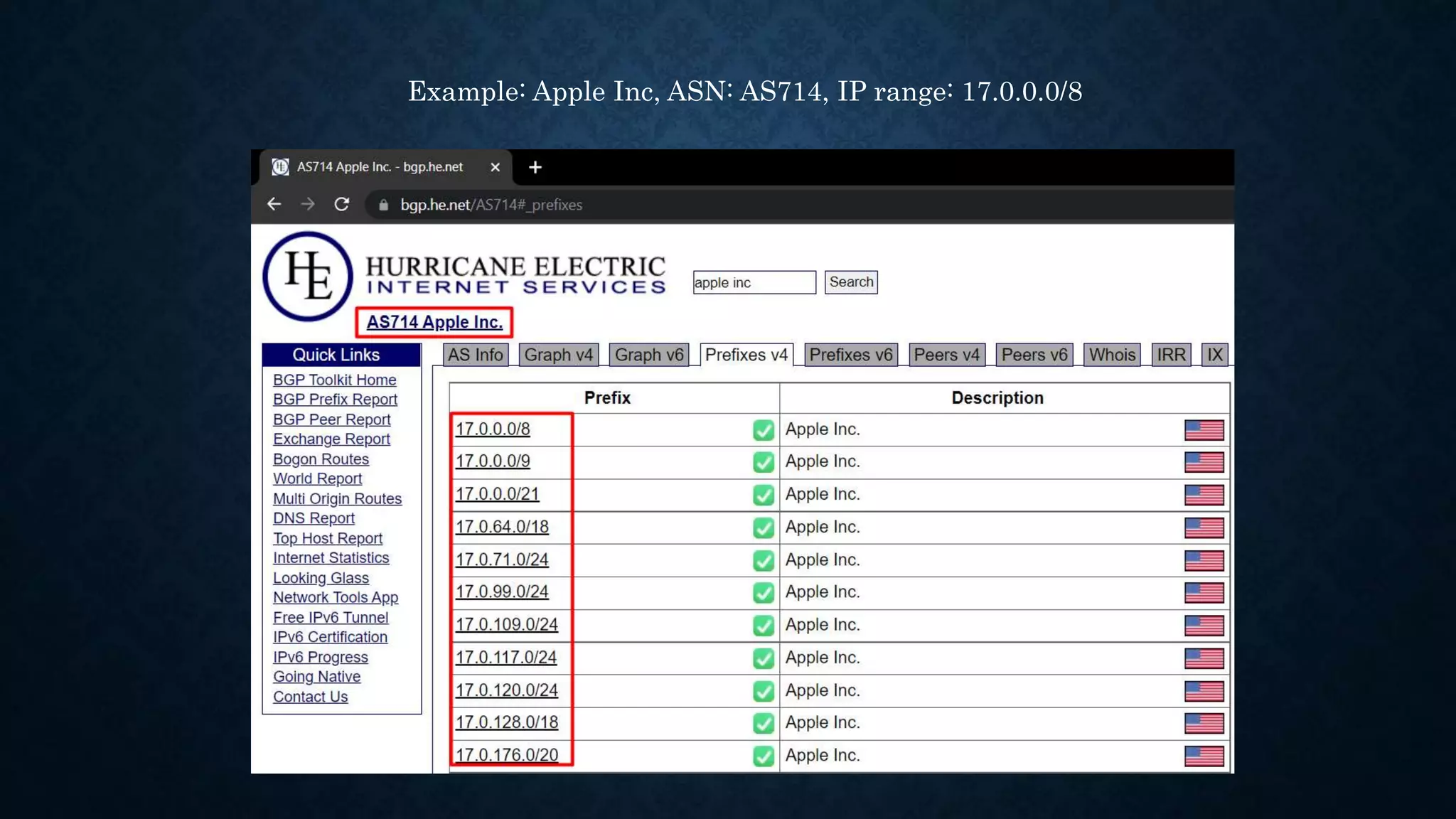
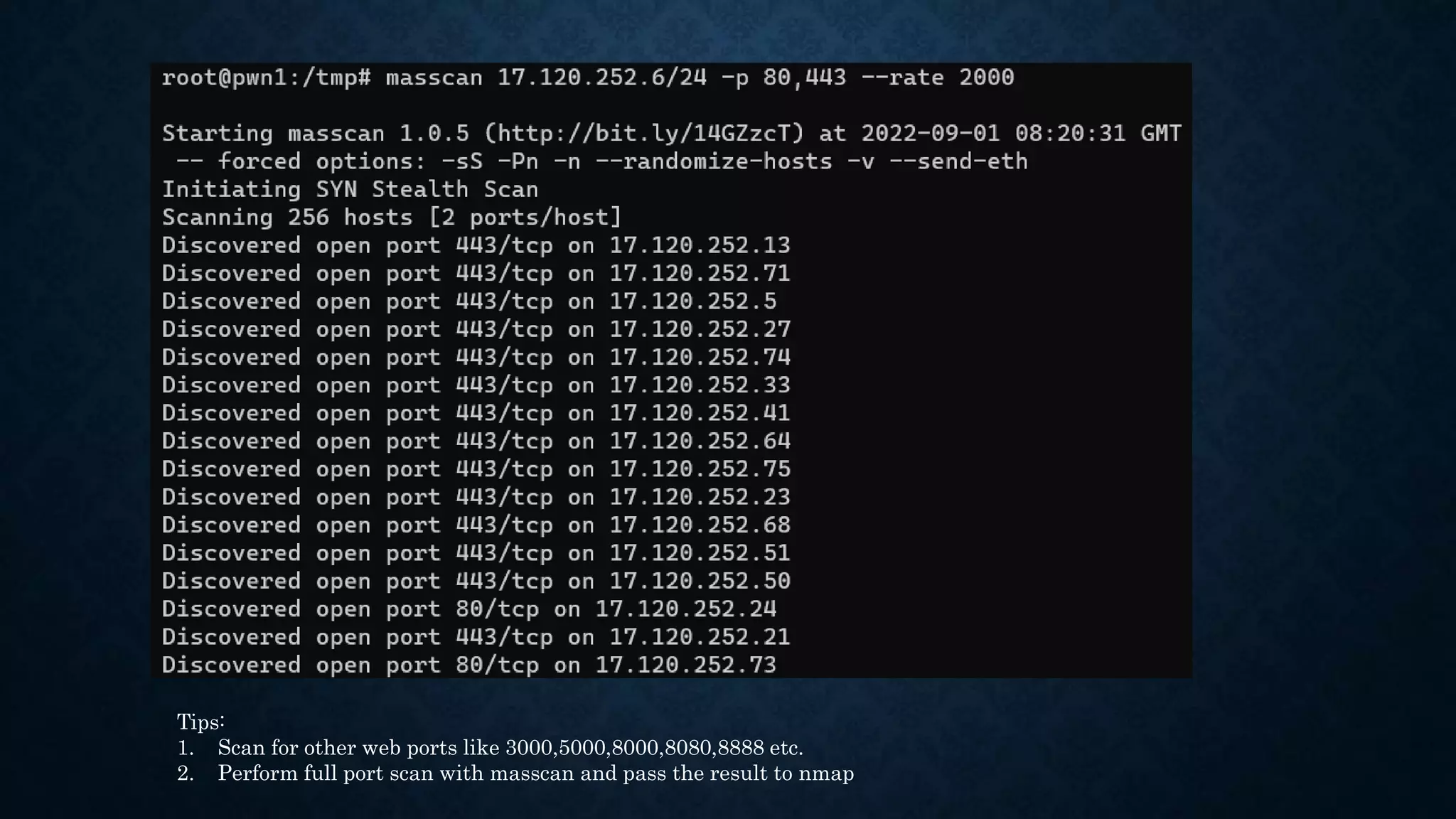
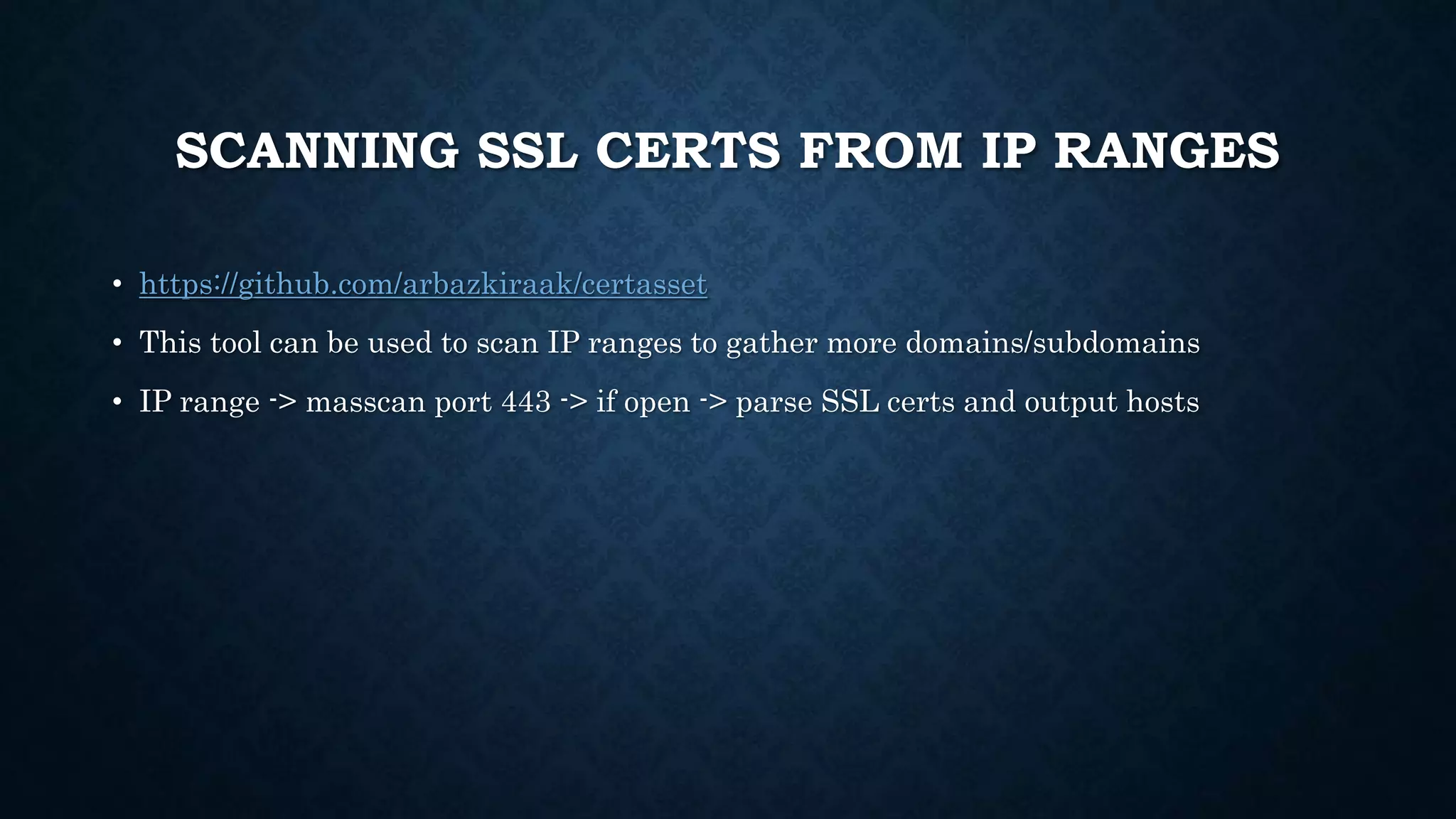
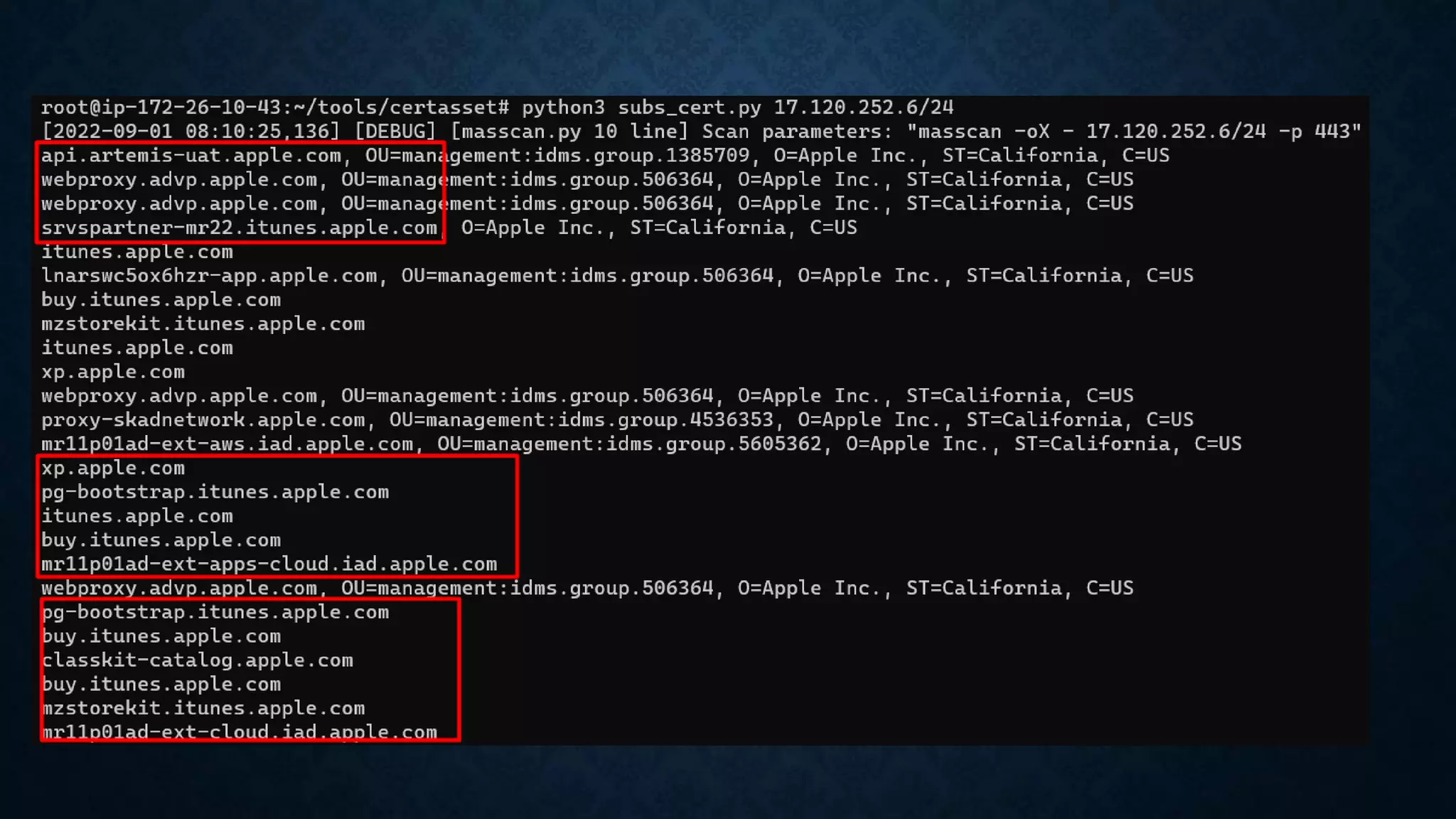
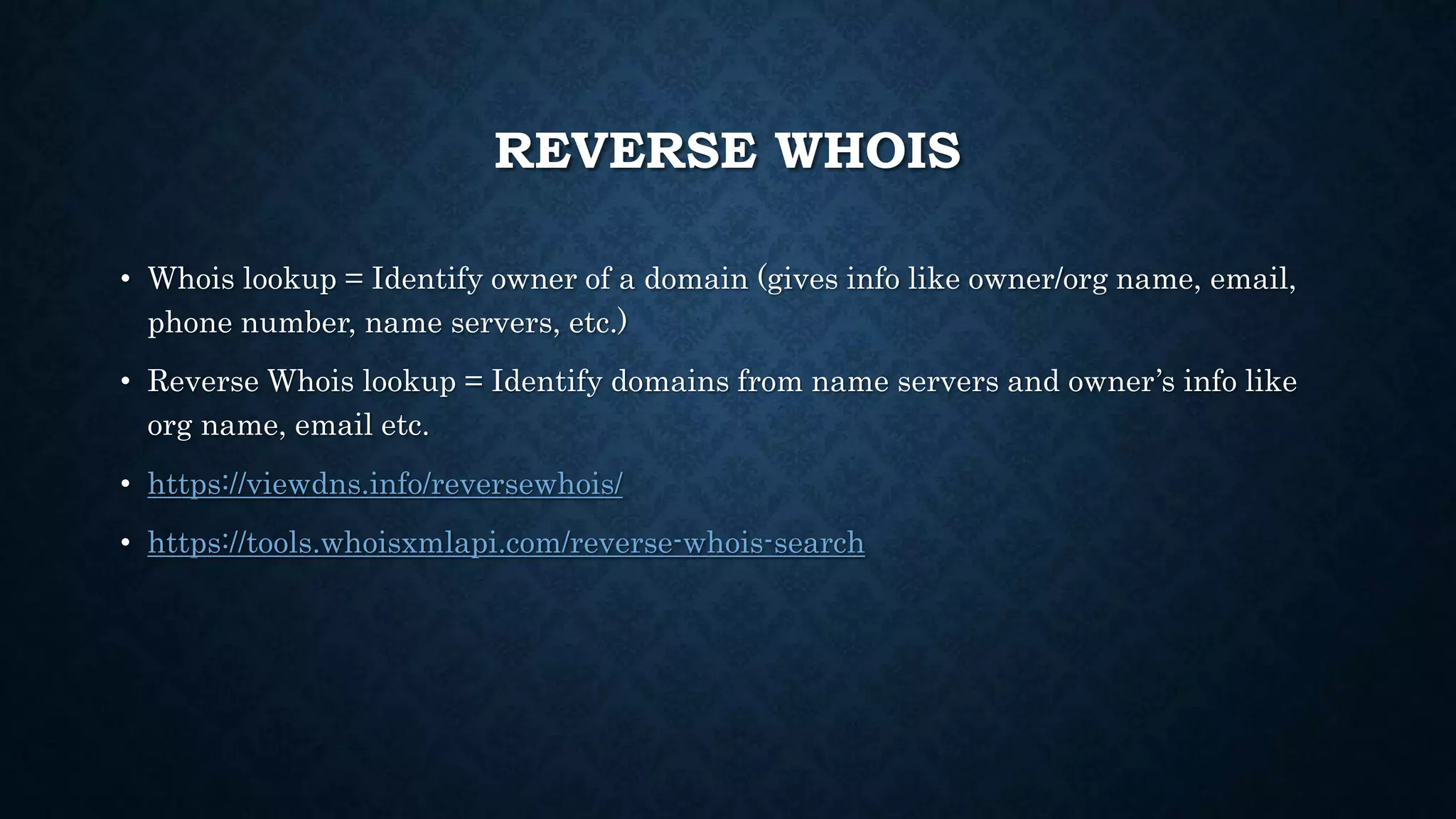
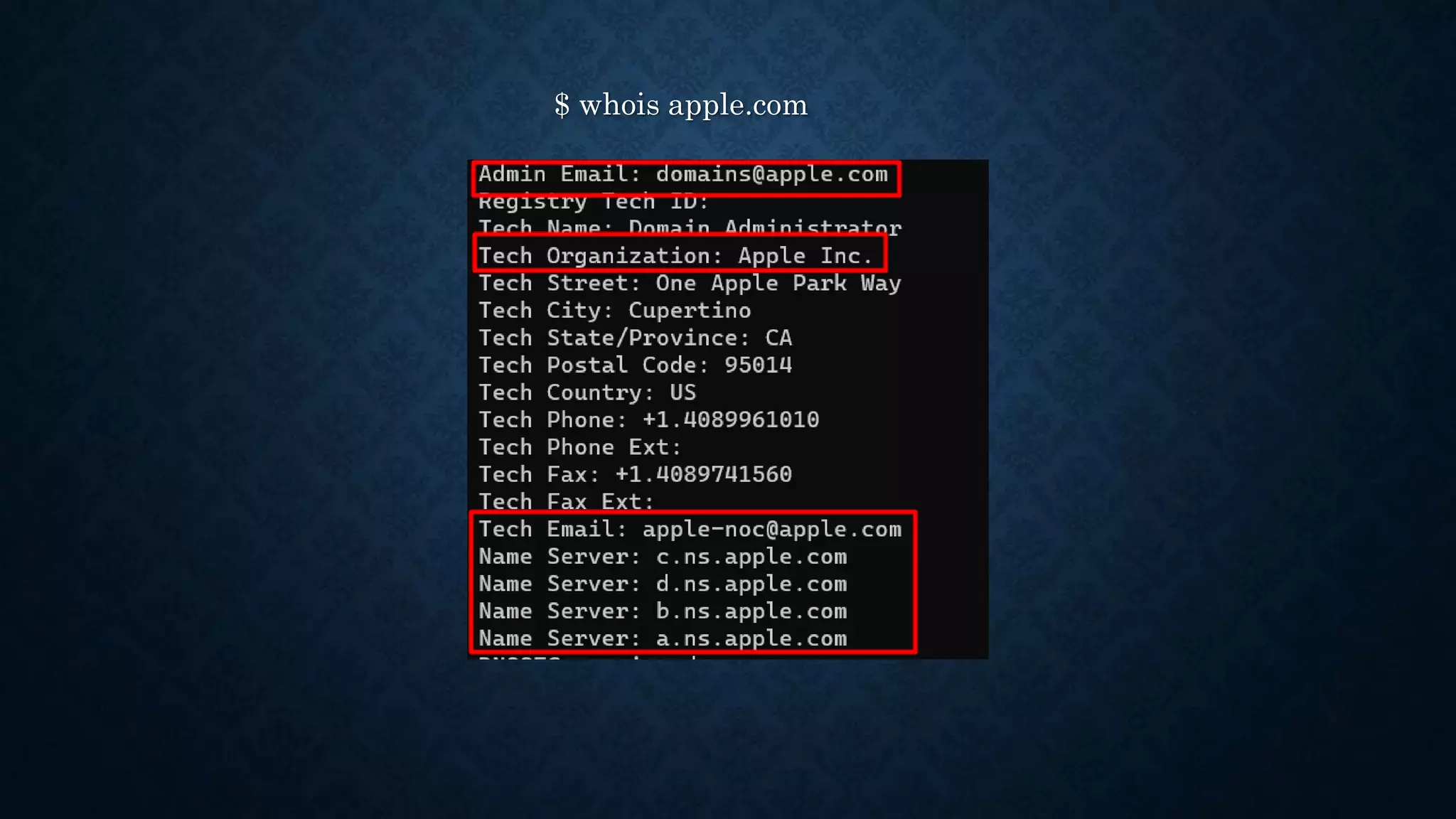
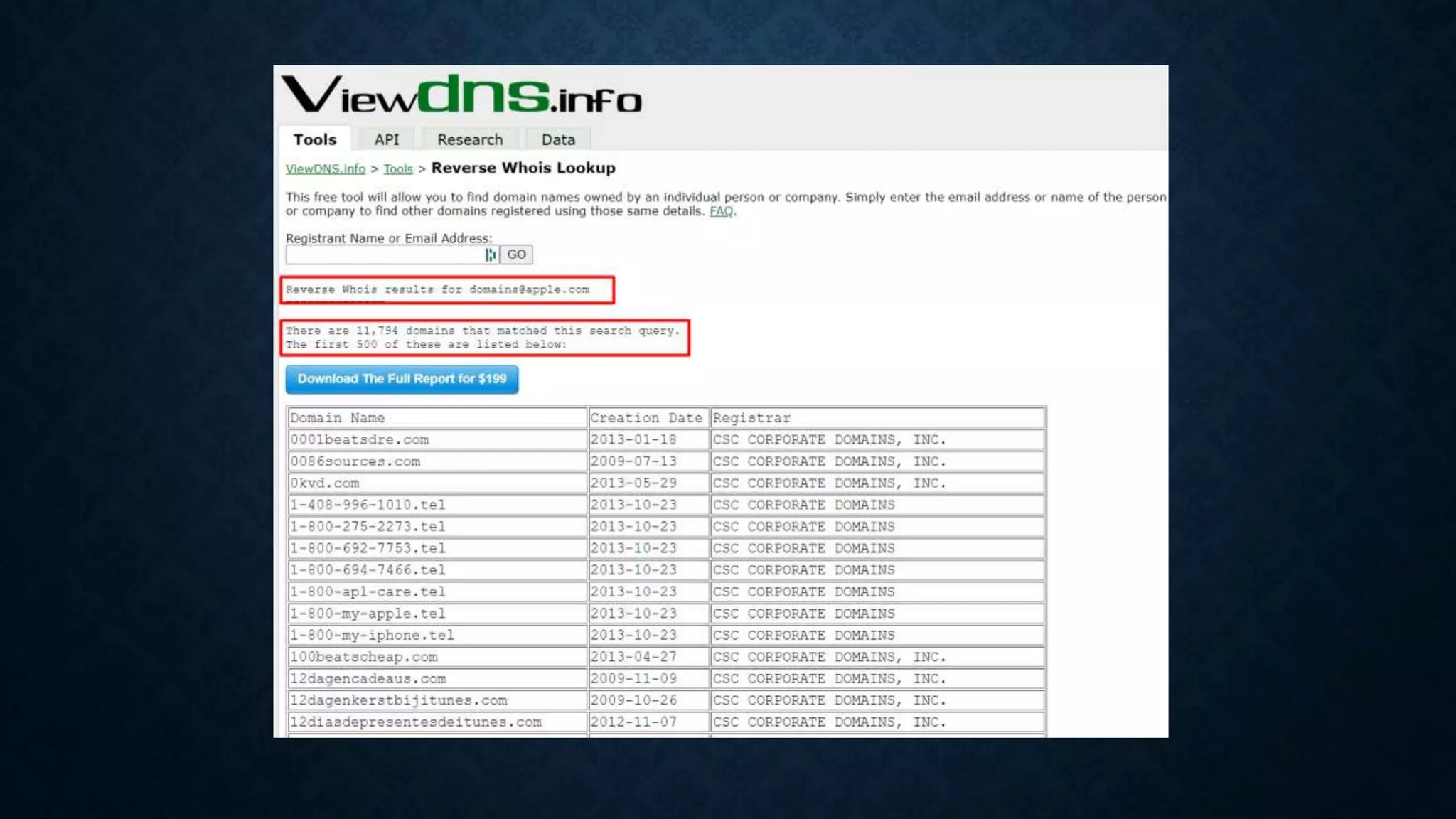
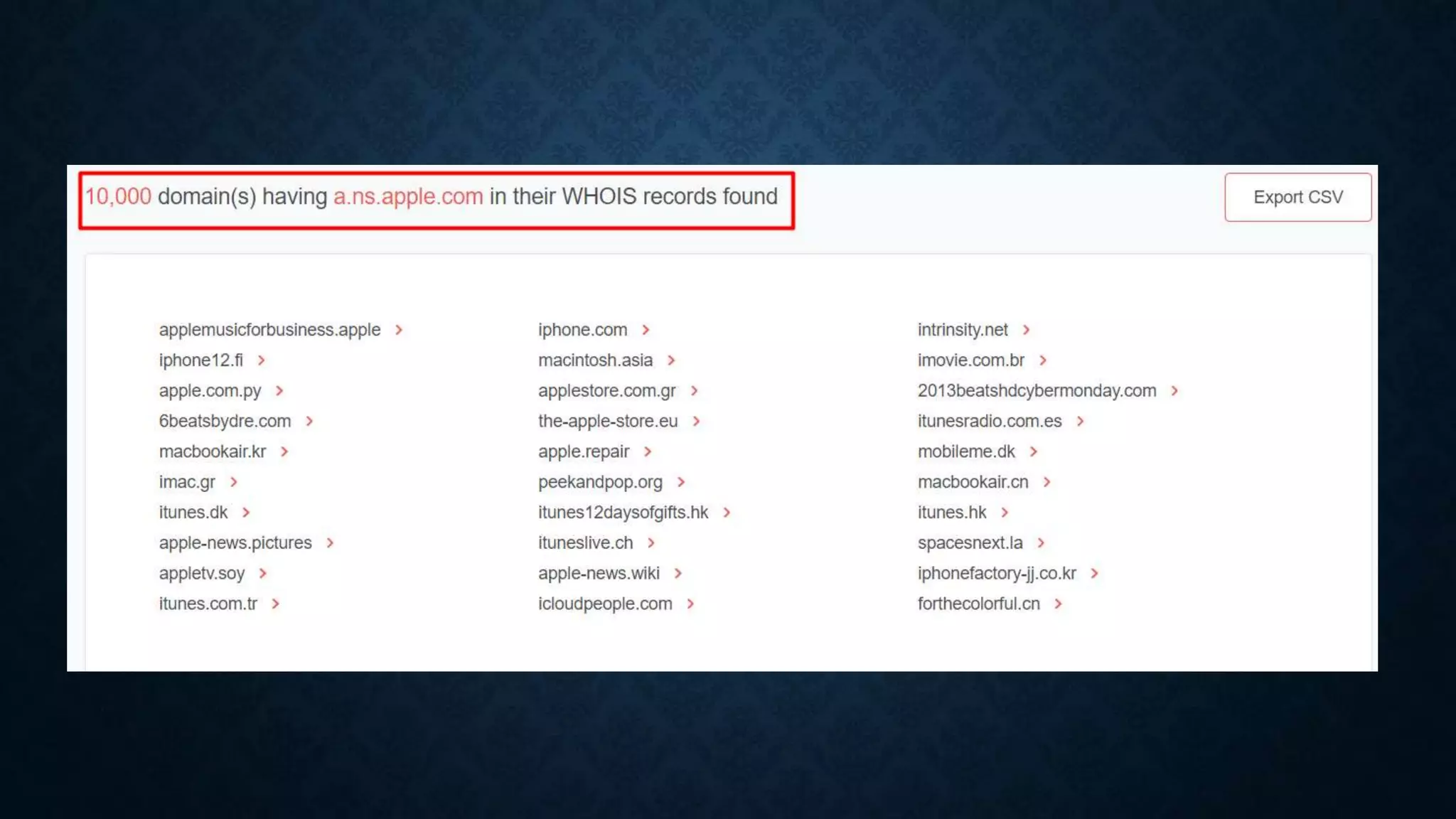
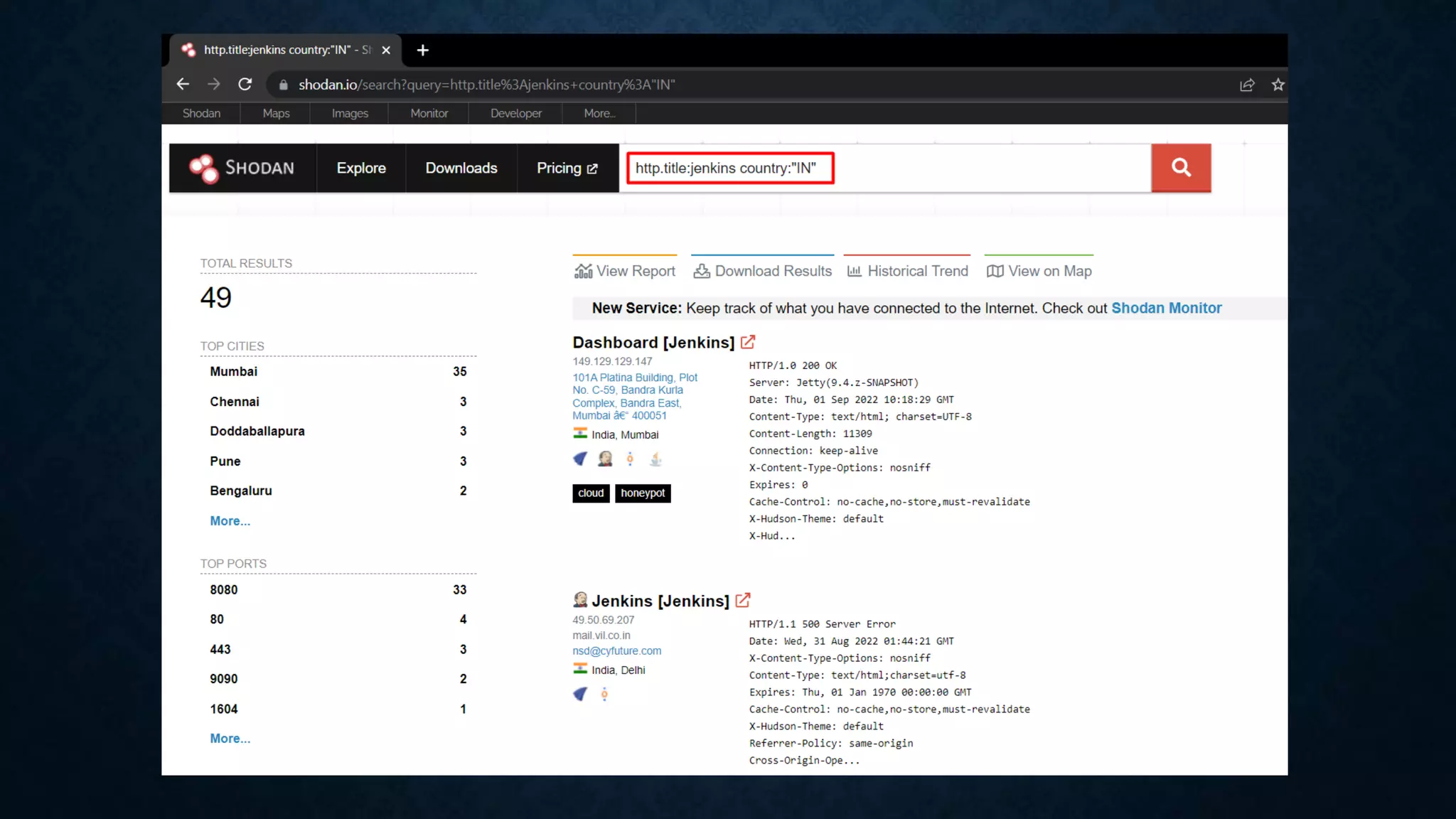
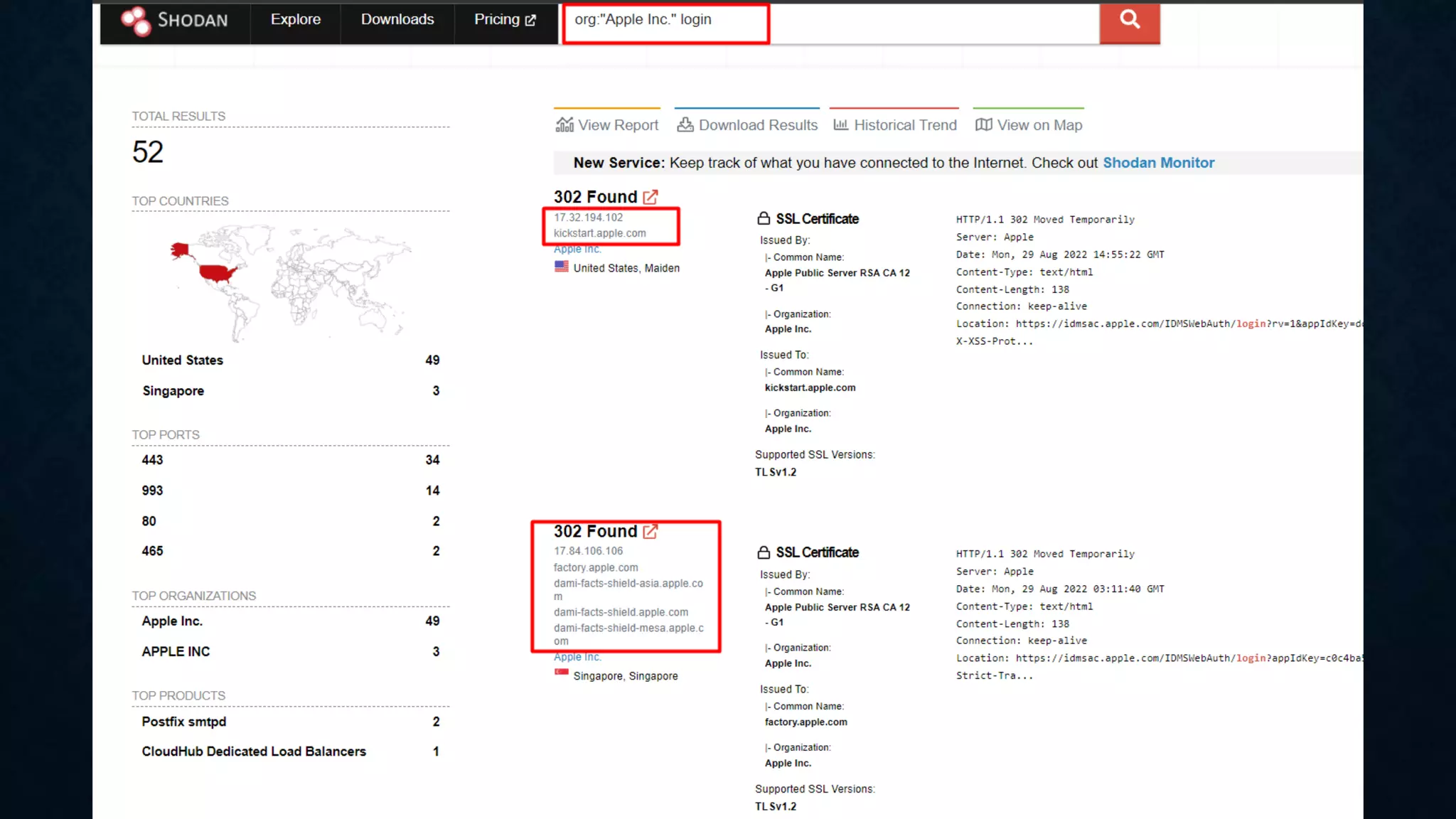
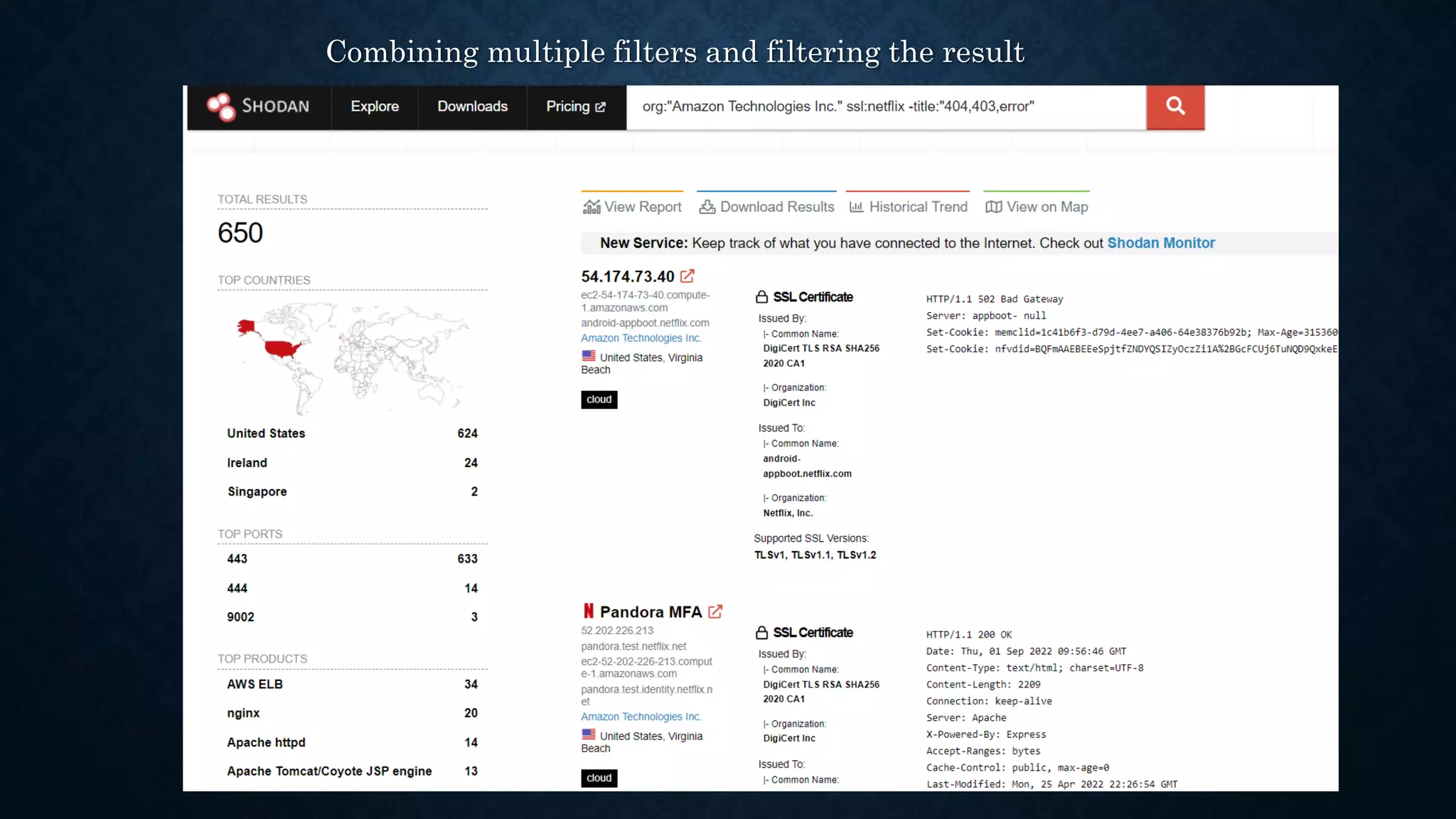
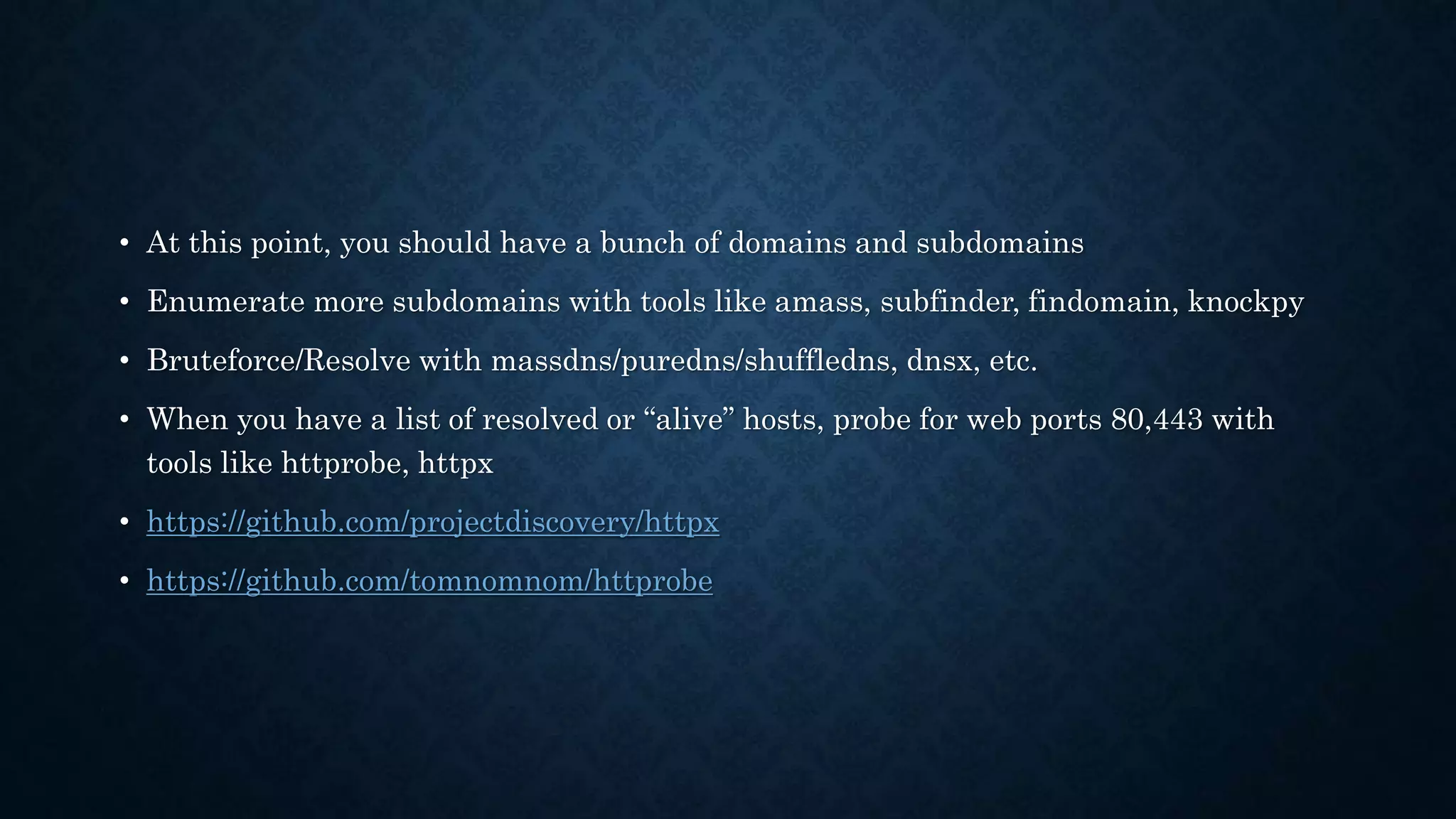
- It discusses infrastructure reconnaissance like scanning IP ranges to find domains, reverse whois lookups, and using Shodan to search for targets.
- Content discovery techniques are presented like probing web ports and using wordlists to find pages and endpoints.
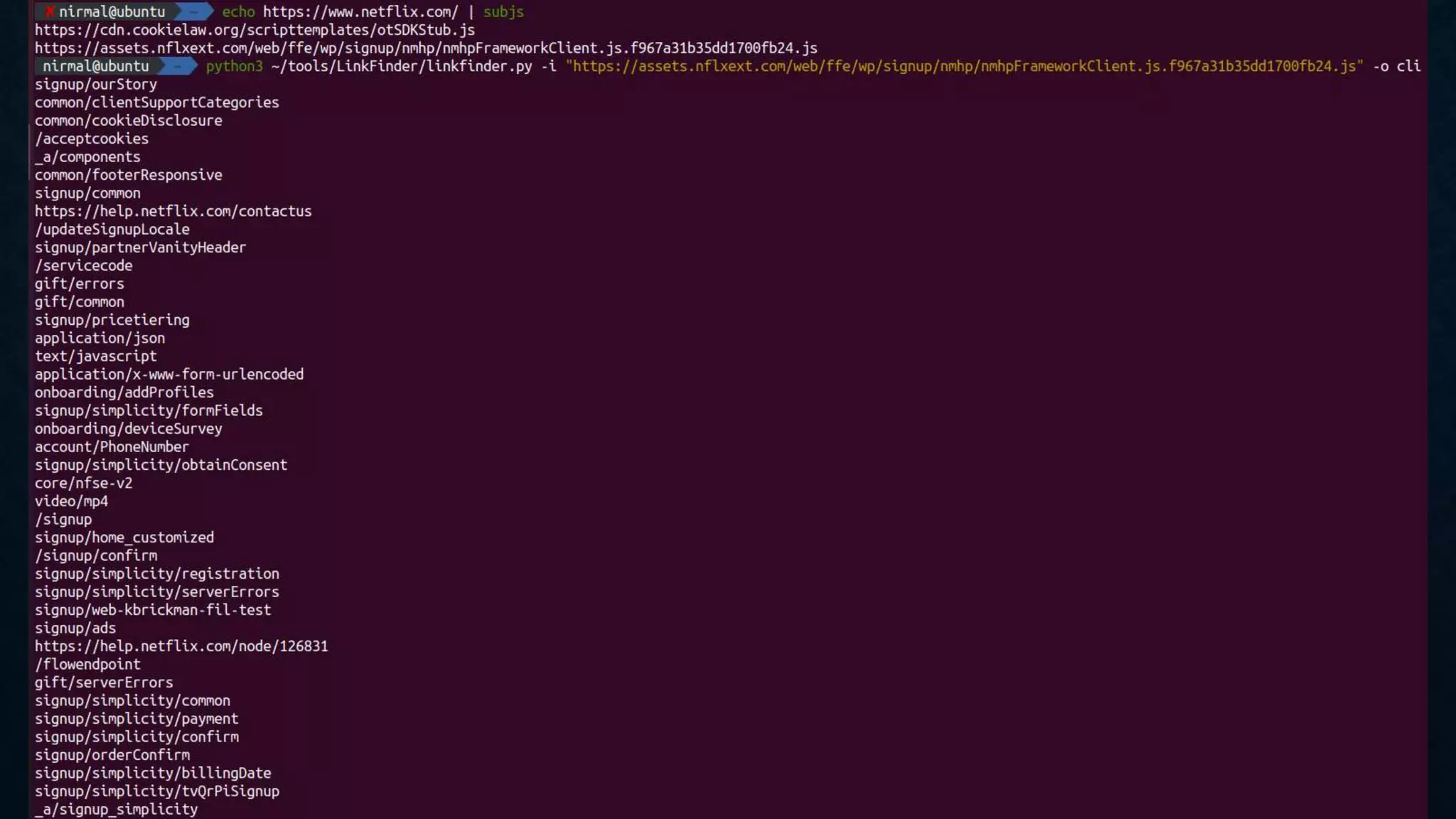
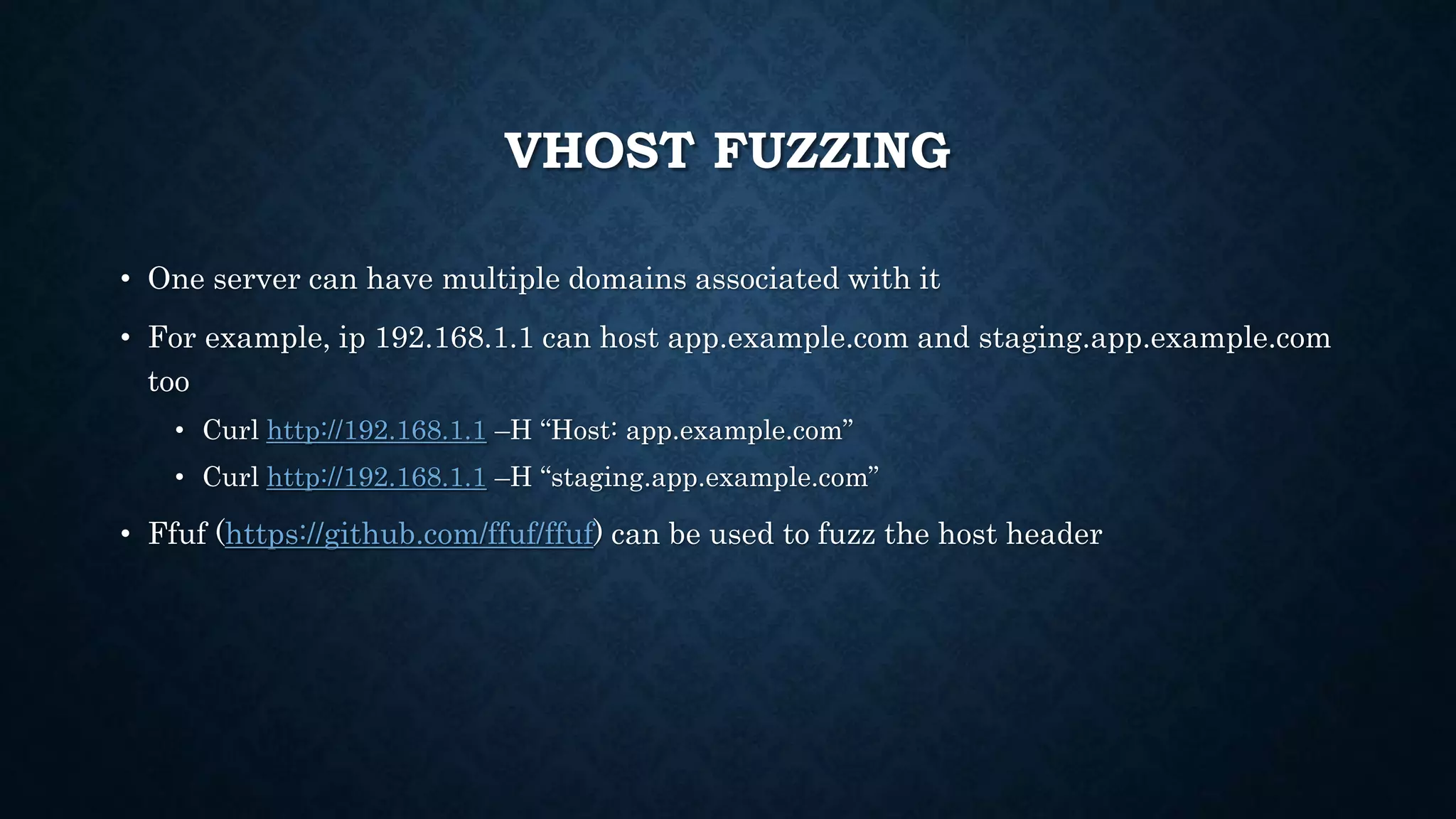
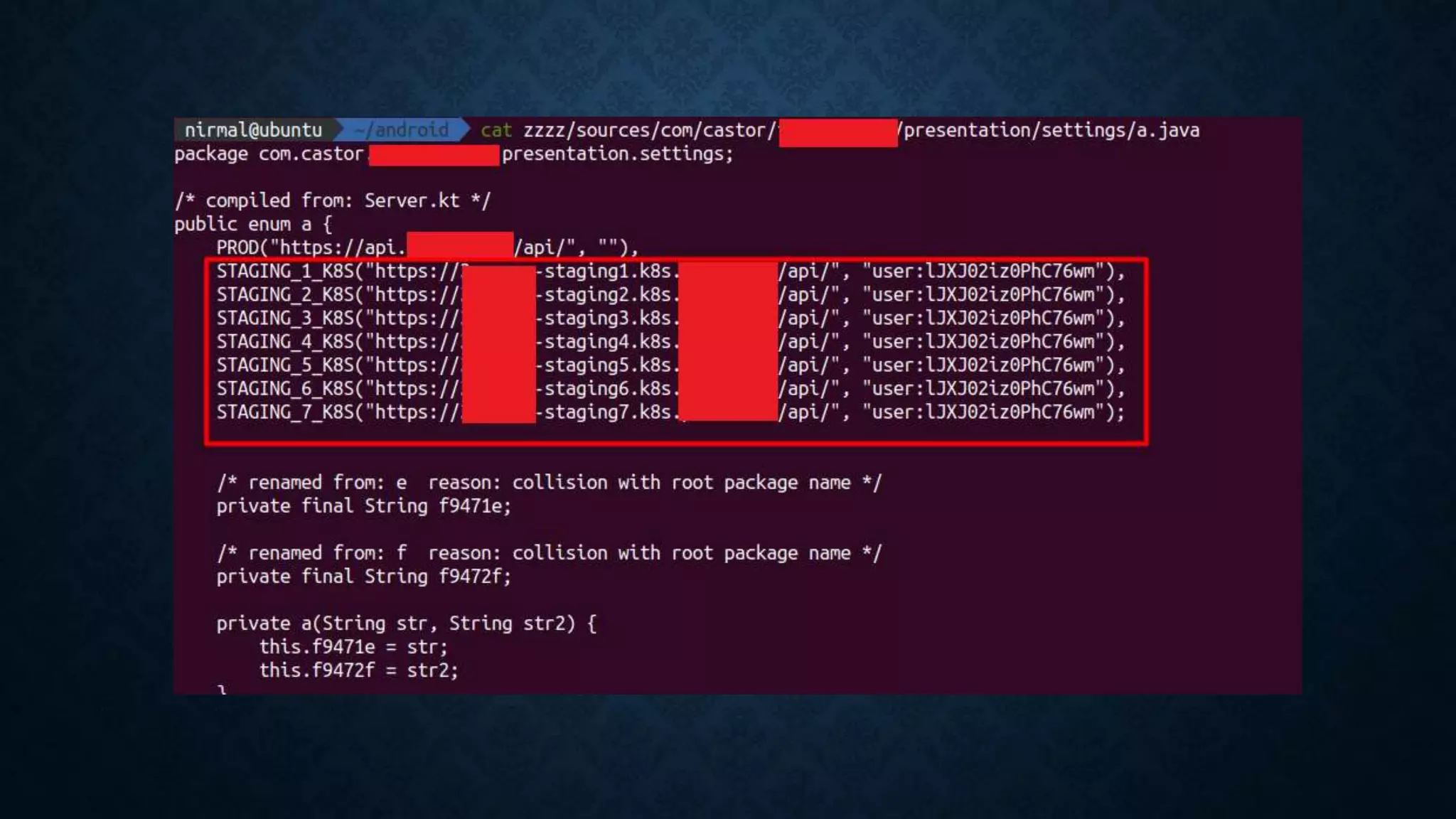
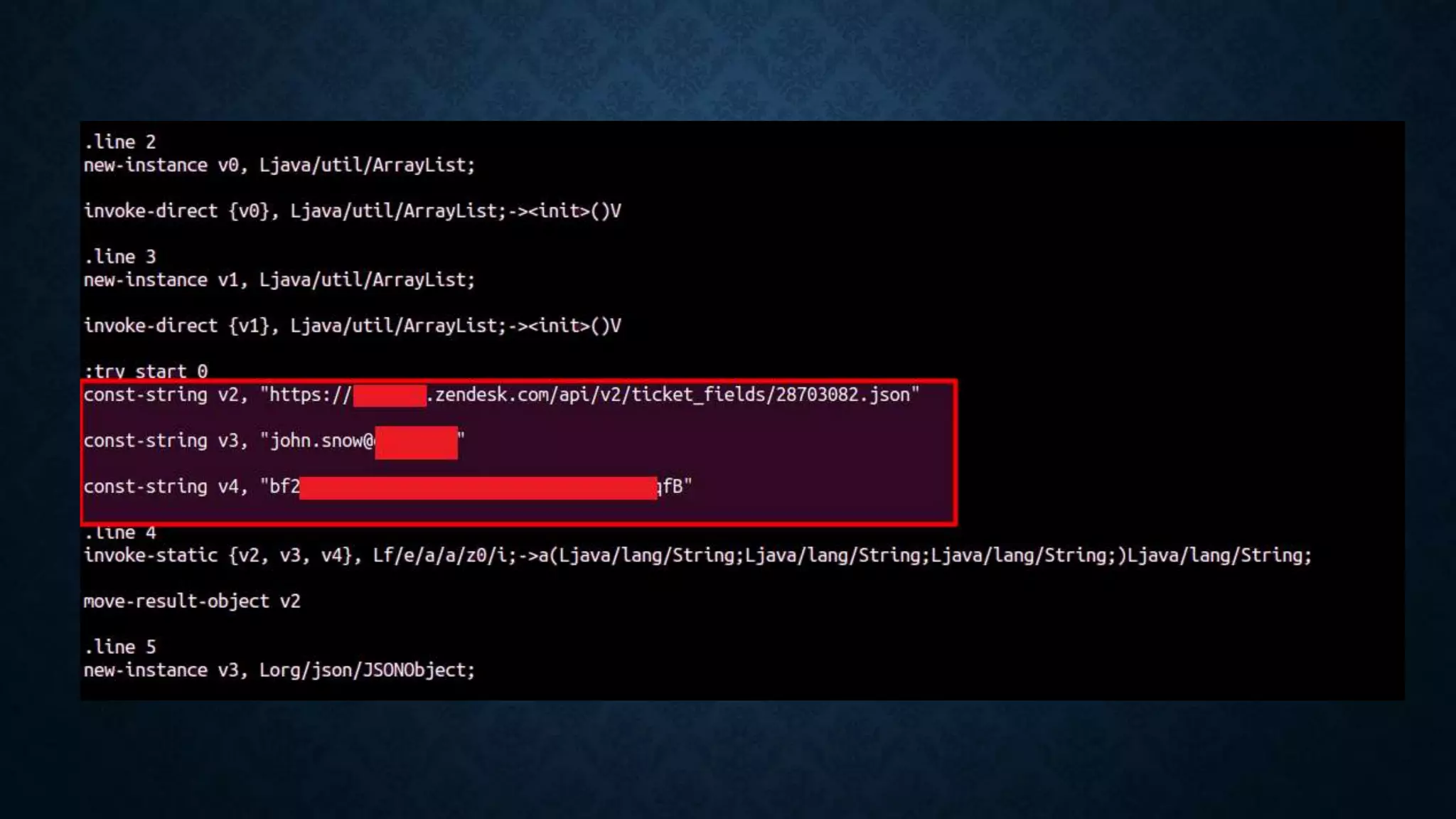
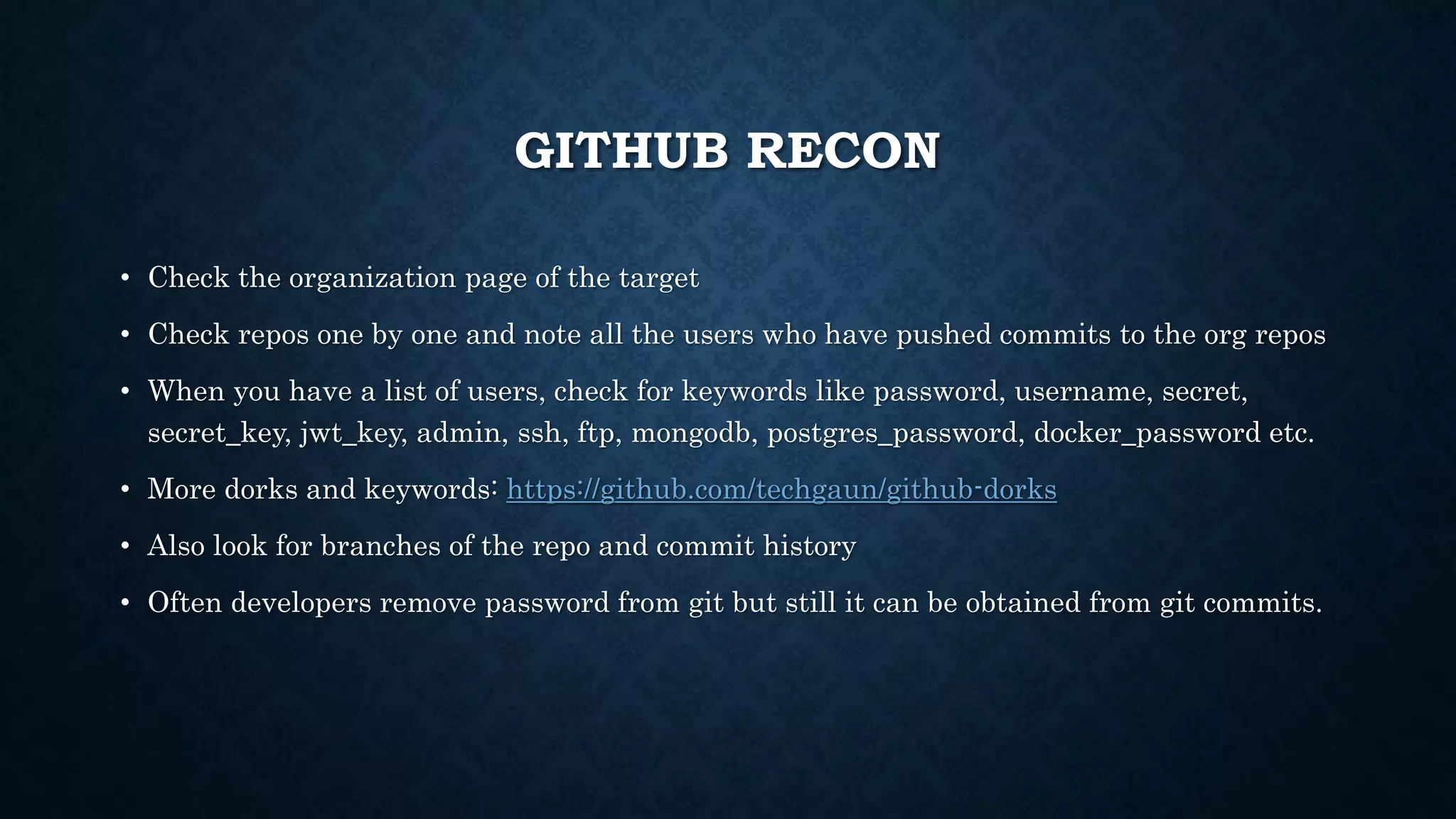
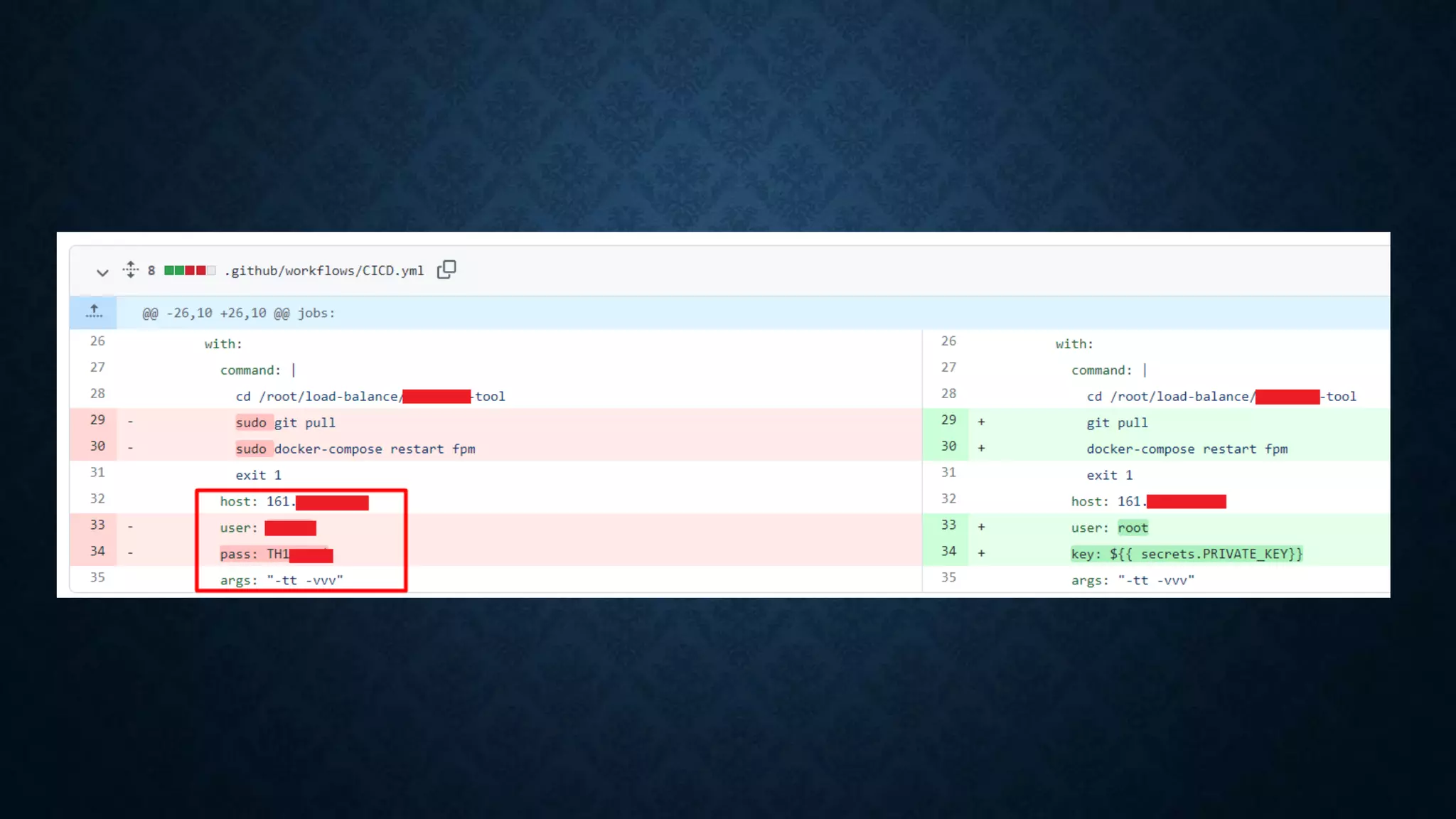
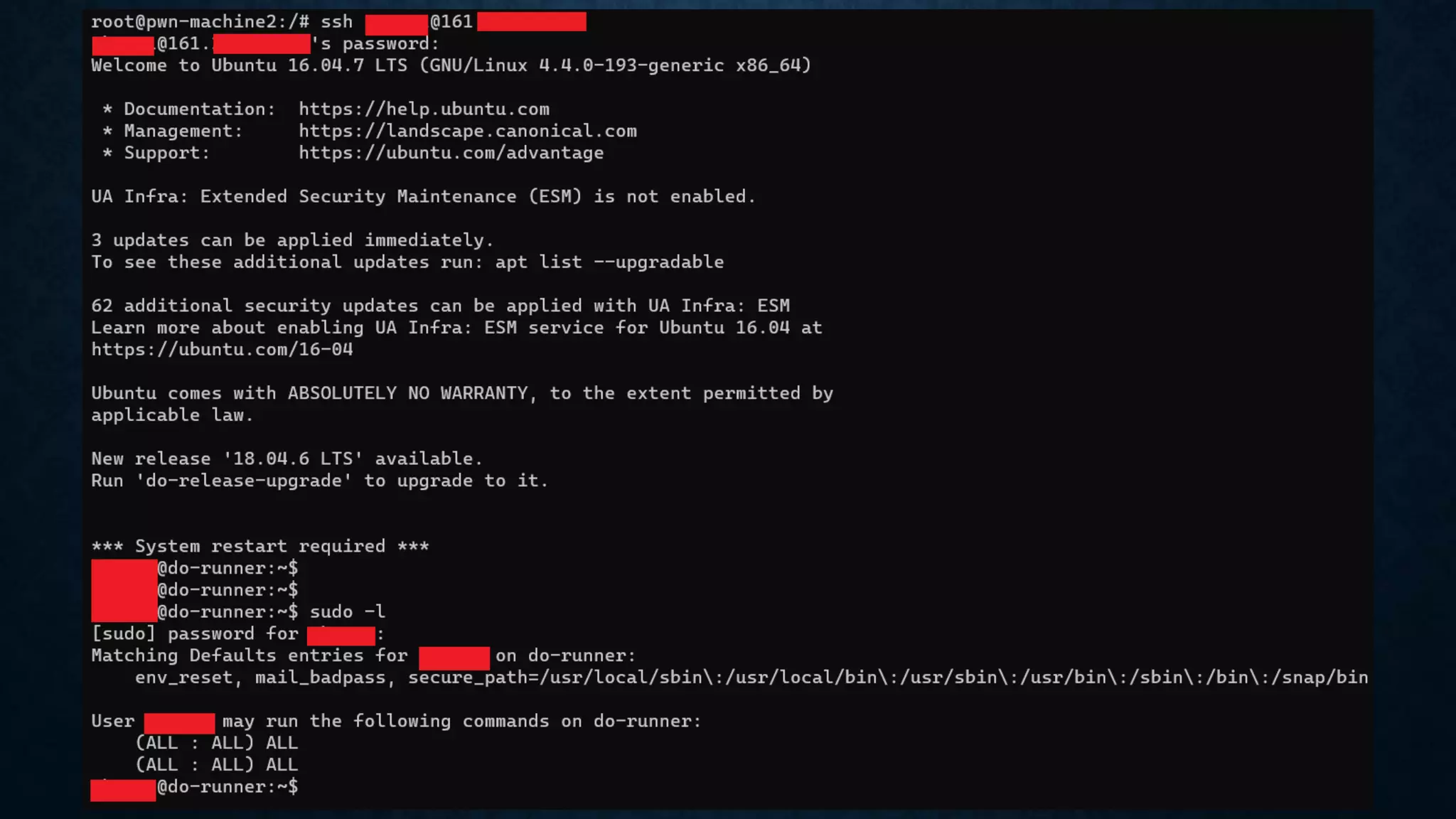
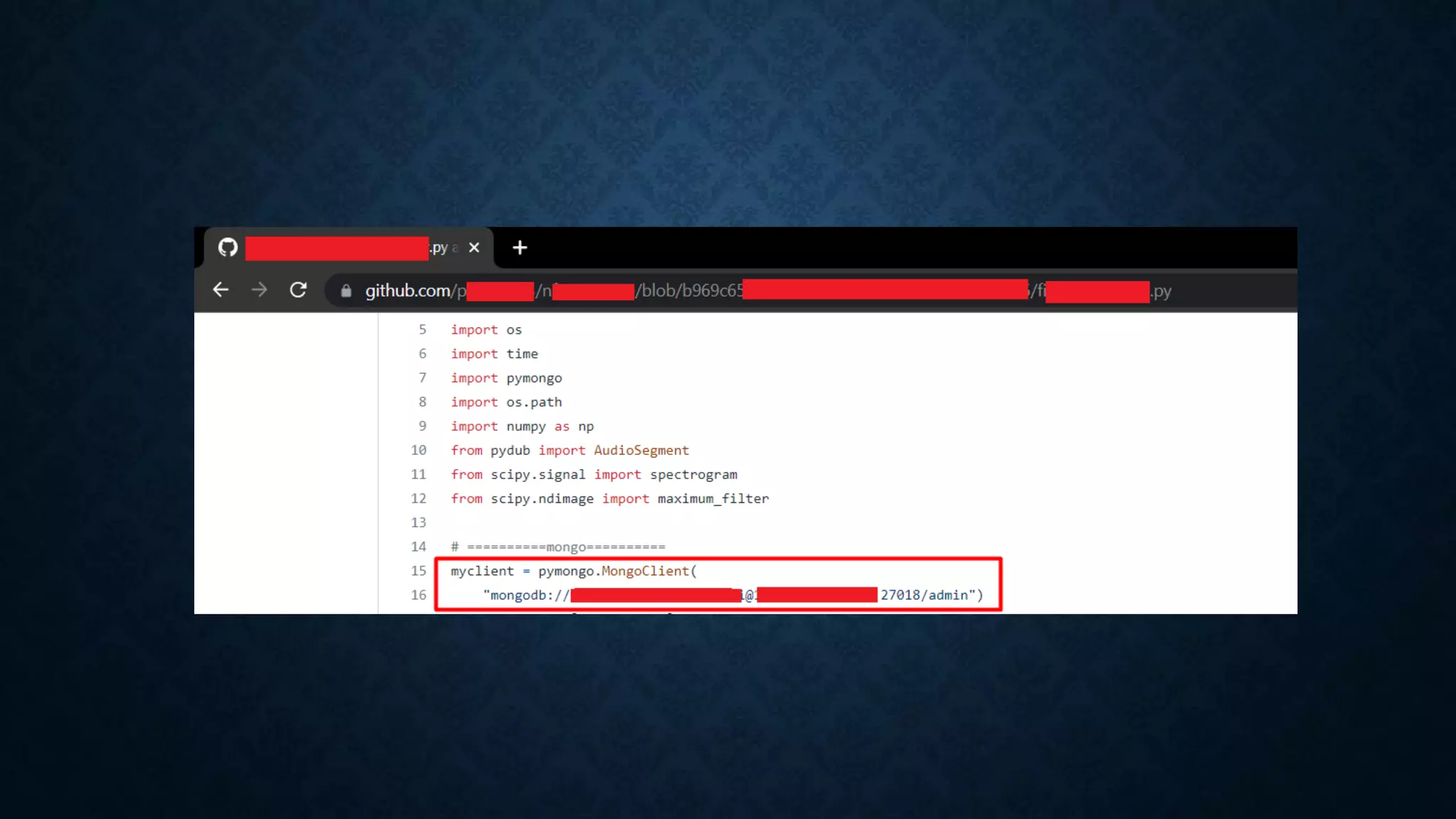
- Additional techniques include hunting for secrets in JavaScript files, Android apps, and code sharing websites. Vhost fuzzing and recon of code repositories are also covered.