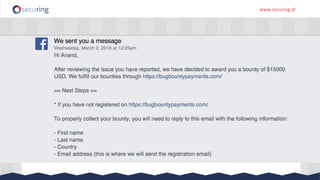
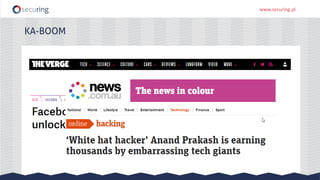
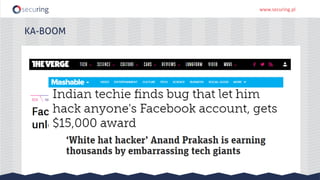
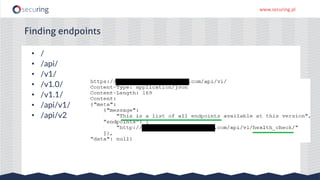
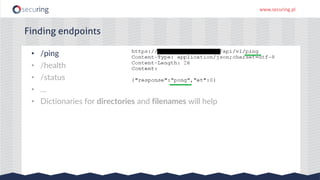
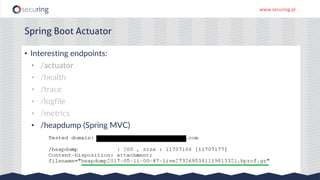
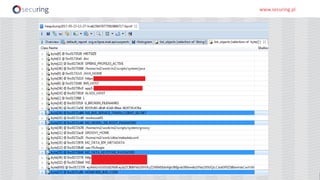
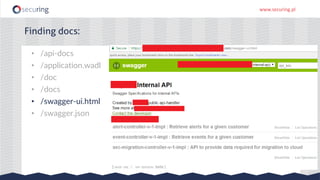
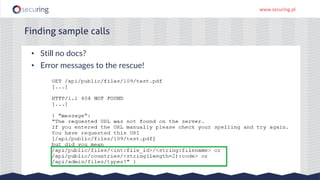
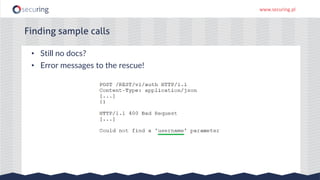
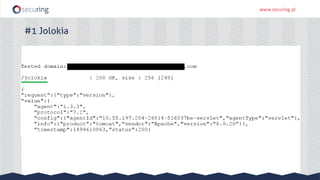
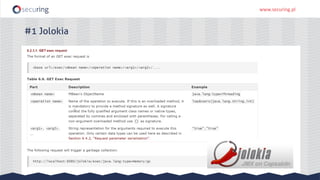
The document discusses the perspective of a REST API pentester, highlighting the importance of rate limiting in password recovery processes and various techniques for identifying endpoints, documentation, sample calls, and keys. It provides insights into the structure of REST APIs, common vulnerabilities, and tools available for security testing, including fuzzing and code analysis. Additionally, it touches on specific examples like Jolokia and the challenges faced when security measures are insufficient.