This document provides an overview of firewall concepts including:
- Learning objectives around firewall types, functions, and deployment of policies.
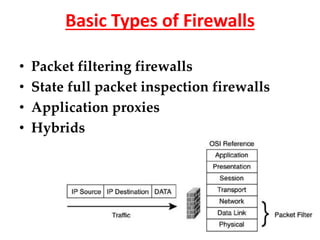
- The basic types of firewalls: packet filtering, stateful packet inspection, application proxies, and hybrids.
- Details on packet filtering firewalls including pros, cons, and how they examine packets.
- Pros and cons of application proxies.
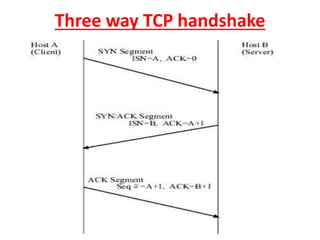
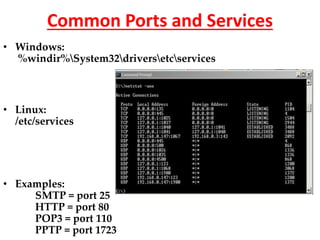
- Background on OSI and TCP/IP models, the three-way TCP handshake, common ports/services, and the STRIDE threat model.
- How to respond to threats and build a firewall port matrix.
- An introduction to iptables and examples of basic packet filtering rules.
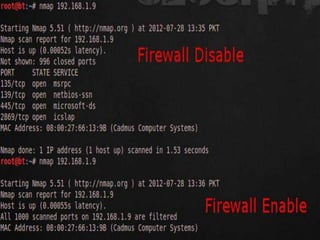
- An overview of the network scanning