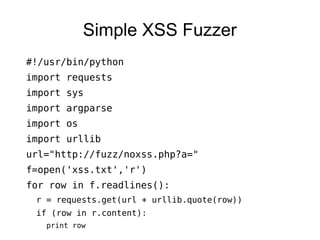
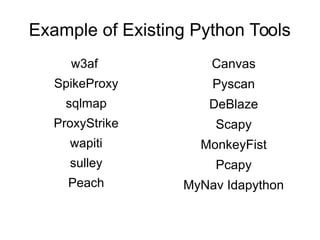
This document discusses using Python for web penetration testing. It begins with an introduction of the speaker. The objectives are to focus only on Python and introduce its functionality for penetration testers. Example existing Python tools are listed like w3af, sqlmap, and Scapy. Notable Python modules that are discussed include Requests for making HTTP requests, BeautifulSoup for parsing HTML, and Argparse for creating command line programs. Demonstrations include regular expression matching, XSS fuzzing, and extracting files from exposed .svn folders. References are provided for learning Python through online courses and books.










![Regular Expression Pattern Match
#!/usr/bin/python
import requests
import re
regex_array = {
'wordpress' : '<link rel="stylesheet" [^>]+wp-content',
'Drupal' : '<(?:link|style)[^>]+sites/(?:default|all)/(?:themes|modules)/'}
r=requests.get('http://www.anantshri.com')
for k, v in regex_array.iteritems():
m=re.search(v,r.content)
if (m):
print k, " : Detected " , " as the content has : ", m.group(0)](https://image.slidesharecdn.com/snakebites-150404211416-conversion-gate01/85/Snake-bites-Python-for-Pentesters-15-320.jpg)