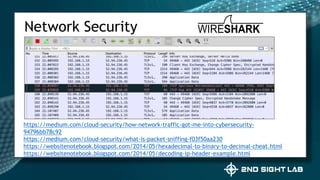
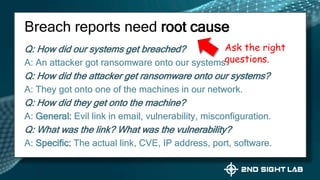
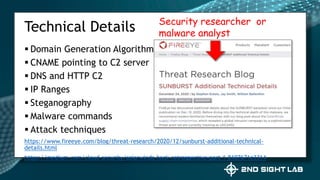
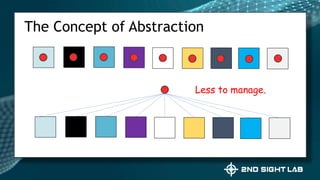
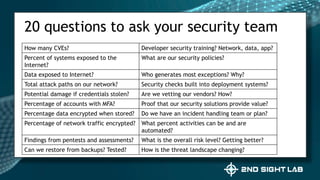
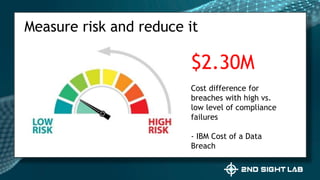
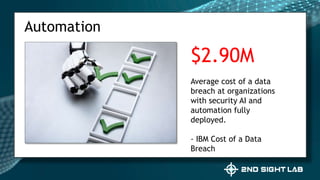
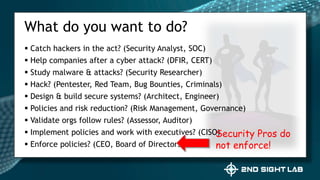
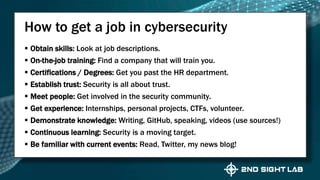
This document provides an overview of Teri Radichel's background and experience in cybersecurity. It details her progression from software engineer to cloud architect and into cybersecurity roles. It lists her certifications, entrepreneurial ventures, speaking engagements, and publications. The document then discusses different career paths in cybersecurity including security operations, intrusion response, and working as a hacker or for the government/military. It provides examples of security assessments and reviews common frameworks, best practices, and regulations. Finally, it discusses getting a job in cybersecurity through skills acquisition, networking, and continuous learning.