CYBER SECURITY CAREER GUIDE CHEAT SHEET
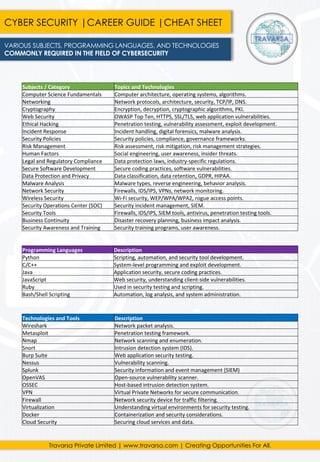
- 1. Subjects / Category Topics and Technologies Computer Science Fundamentals Computer architecture, operating systems, algorithms. Networking Network protocols, architecture, security, TCP/IP, DNS. Cryptography Encryption, decryption, cryptographic algorithms, PKI. Web Security OWASP Top Ten, HTTPS, SSL/TLS, web application vulnerabilities. Ethical Hacking Penetration testing, vulnerability assessment, exploit development. Incident Response Incident handling, digital forensics, malware analysis. Security Policies Security policies, compliance, governance frameworks. Risk Management Risk assessment, risk mitigation, risk management strategies. Human Factors Social engineering, user awareness, insider threats. Legal and Regulatory Compliance Data protection laws, industry-specific regulations. Secure Software Development Secure coding practices, software vulnerabilities. Data Protection and Privacy Data classification, data retention, GDPR, HIPAA. Malware Analysis Malware types, reverse engineering, behavior analysis. Network Security Firewalls, IDS/IPS, VPNs, network monitoring. Wireless Security Wi-Fi security, WEP/WPA/WPA2, rogue access points. Security Operations Center (SOC) Security incident management, SIEM. Security Tools Firewalls, IDS/IPS, SIEM tools, antivirus, penetration testing tools. Business Continuity Disaster recovery planning, business impact analysis. Security Awareness and Training Security training programs, user awareness. Programming Languages Description Python Scripting, automation, and security tool development. C/C++ System-level programming and exploit development. Java Application security, secure coding practices. JavaScript Web security, understanding client-side vulnerabilities. Ruby Used in security testing and scripting. Bash/Shell Scripting Automation, log analysis, and system administration. Technologies and Tools Description Wireshark Network packet analysis. Metasploit Penetration testing framework. Nmap Network scanning and enumeration. Snort Intrusion detection system (IDS). Burp Suite Web application security testing. Nessus Vulnerability scanning. Splunk Security information and event management (SIEM) OpenVAS Open-source vulnerability scanner. OSSEC Host-based intrusion detection system. VPN Virtual Private Networks for secure communication. Firewall Network security device for traffic filtering. Virtualization Understanding virtual environments for security testing. Docker Containerization and security considerations. Cloud Security Securing cloud services and data. CYBER SECURITY |CAREER GUIDE |CHEAT SHEET VARIOUS SUBJECTS, PROGRAMMING LANGUAGES, AND TECHNOLOGIES COMMONLY REQUIRED IN THE FIELD OF CYBERSECURITY Travarsa Private Limited | www.travarsa.com | Creating Opportunities For All.
- 2. CYBER SECURITY |CAREER GUIDE |CHEAT SHEET LIST OF ESSENTIAL TOOLS FOR CYBER SECURITY DOMAIN Travarsa Private Limited | www.travarsa.com | Creating Opportunities For All. Tool Name Description Wireshark Network protocol analyzer for packet capturing and analysis. Metasploit Penetration testing framework for finding and exploiting vulnerabilities. Nmap Network scanning tool for discovering open ports and services. Snort Intrusion detection and prevention system (IDS/IPS). Maltego Tool for open-source intelligence and forensics. Nessus Vulnerability scanner for identifying weaknesses in systems. Splunk Security information and event management (SIEM) tool. Burp Suite Application security testing tool for web applications. Suricata Open-source IDS/IPS engine for network security monitoring. Aircrack-ng Suite of tools for assessing Wi-Fi network security. GnuPG (GPG) Free encryption software for securing data and communication. Cuckoo Sandbox Malware analysis system for examining suspicious files and behavior. OpenVAS Open-source vulnerability scanner and management tool. Security Onion Linux distribution for network security monitoring and intrusion detection. Acunetix Web application security scanner. OSSEC Open-source host-based intrusion detection system. Kali Linux Linux distribution for penetration testing and ethical hacking. AIDE Host-based intrusion detection system. WiFite Tool for automated wireless network attacks. YARA Tool for writing and identifying malware signatures. Tcpdump Command-line packet analyzer. OpenVAS Open-source vulnerability scanner. CIS-CAT System security assessment tool. Sysinternals Suite Collection of Windows system utilities for security and administration. Hashcat Password recovery and cracking tool. Cain and Abel Password recovery tool for Windows. John the Ripper Password cracking tool. Ghidra Open-source software reverse engineering tool. MISP Threat intelligence platform. Bro (Zeek) Open-source network security monitor.
- 3. CYBER SECURITY |CAREER GUIDE |CHEAT SHEET LIST OF CERTIFICATIONS AND JOB DESCRIPTIONS UNDER CYBER SECURITY Travarsa Private Limited | www.travarsa.com | Creating Opportunities For All. Certification Name Description Certified Information Systems Security Professional A globally certification for information security professionals. Certified Ethical Hacker (CEH) Focuses on ethical hacking and penetration testing skills. Certified Information Security Manager (CISM) Emphasizes information risk management and governance. Certified Information Systems Auditor (CISA) Focuses on auditing, control, and assurance skills. Certified Cloud Security Professional (CCSP) Specializes in cloud security principles and practices. Certified Information Systems Security Officer Covers information security management and leadership. Offensive Security Certified Professional (OSCP) A hands-on certification for penetration testers. Certified Information Security Manager (CISM) Concentrates on cybersecurity management and strategy. Certified Information Security Manager (CISM) Concentrates on cybersecurity management and strategy. Certified Information Security Manager (CISM) Concentrates on cybersecurity management and strategy. Certified Information Security Manager (CISM) Concentrates on cybersecurity management and strategy. Job Title Description Cybersecurity Analyst Analyzes and protects computer systems and networks from threats. Information Security Manager Manages an organization's information security program and policies. Chief Information Security Officer (CISO) Responsible for an organization's overall cybersecurity strategy. Ethical Hacker Identifies vulnerabilities through ethical hacking. Security Consultant Provides expert strategies and consulting on security measures. Security Architect Designs secure systems and network infrastructures. Incident Responder Investigates and responds to cybersecurity incidents and breaches. Cybersecurity Auditor Evaluates and assesses security controls and compliance. Security Engineer Engineers & implements security solutions to protect systems & data. Security Administrator Manages security policies, user accounts, and access controls. Vulnerability Assessor Identifies and assesses vulnerabilities in systems and applications. Security Operations Center (SOC) Analyst Monitors and analyzes security alerts and incidents in a SOC. Security Compliance Analyst Ensures compliance with security regulations and industry standards. Security Awareness and Training Specialist Educates employees on security best practices. Forensic Analyst Investigates cybercrimes & collects digital evidence for legal purposes. Malware Analyst Analyzes & reverse-engineers malicious software to check behavior. Security Researcher Conducts research on emerging threats and vulnerabilities. Security Policy Analyst Develops and enforces security policies and procedures. Threat Intelligence Analyst Gathers and analyzes intelligence to identify potential security threats. Security Risk Analyst Assesses and manages security risks within an organization. Security Operations Manager Manages the day-to-day operations of a security team or SOC. Identity and Access Management (IAM) Manages user identities and access permissions. Security Awareness Program Manager Oversees security awareness training programs. Network Security Engineer Specializes in securing network infrastructure and communications. Cloud Security Engineer Focuses on securing cloud-based environments and services. Application Security Engineer Ensures the security of software applications. IoT (Internet of Things) Security Specialist Focuses on securing IoT devices and networks. Wireless Security Analyst Secures wireless networks and devices. Mobile Security Analyst Specializes in securing mobile devices and applications. Blockchain Security Specialist Ensures the security of blockchain technologies and cryptocurrencies.
- 4. CYBER SECURITY |CAREER GUIDE |CHEAT SHEET STEPS TO GET STARTED WITH CYBER SECURITY Travarsa Private Limited | www.travarsa.com | Creating Opportunities For All. Step Action Description 1 Choose Your Path Decide on a specific area of cybersecurity (e.g., network security, ethical hacking). 2 Build Foundations Acquire fundamental knowledge in computer science, networking, and operating systems. 3 Learn Cryptography Study encryption, decryption, cryptographic algorithms, and protocols. 4 Explore Web Security Understand web application security, including common vulnerabilities. 5 Master Ethical Hacking Gain skills in penetration testing, vulnerability assessment, and ethical hacking techniques. 6 Develop Incident Response Learn how to respond to security incidents and perform digital forensics. 7 Understand Policies Familiarize yourself with security policies, regulations, and governance frameworks. 8 Manage Risk Explore risk assessment and management strategies in cybersecurity. 9 Focus on Human Factors Recognize and mitigate social engineering attacks and human-related vulnerabilities. 10 Comply with Regulations Understand legal and regulatory compliance in cybersecurity. 11 Secure Software Development Incorporate security practices into the software development lifecycle. 12 Protect Data and Privacy Ensure the confidentiality and privacy of sensitive data. 13 Analyze Malware Learn to analyze and understand malicious software (malware). 14 Secure Networks Implement security measures for network infrastructure. 15 Safeguard Wireless Networks Secure wireless networks and connected devices. 16 Operate a SOC Manage and monitor security incidents in a Security Operations Center (SOC). 17 Use Security Tools Familiarize yourself with various security tools and technologies. 18 Plan for Continuity Develop business continuity and disaster recovery strategies. 19 Educate on Security Create security awareness and training programs for employees and stakeholders. 20 Specialize and Stay Updated Choose a specialization within cybersecurity and stay up-to-date with the latest trends. Website: www.travarsa.com General Queries : +91 94 777 88119 +91 94 777 88118 General Queries : contact@travarsa.com Internship : internship@travarsa.com