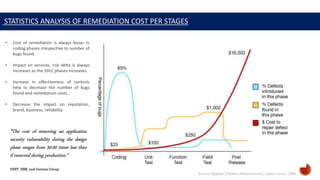
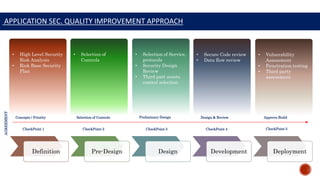
The document outlines the S-SDLC (Secure Software Development Life Cycle) frameworks, including waterfall, agile, and CI/CD approaches, with a focus on application security and risk management practices. It emphasizes the importance of addressing security vulnerabilities early in the development process to reduce remediation costs and increase effectiveness. Key statistics highlight the significant percentage of risks not covered by existing tools and the necessity for a structured approach to both secure coding and testing.