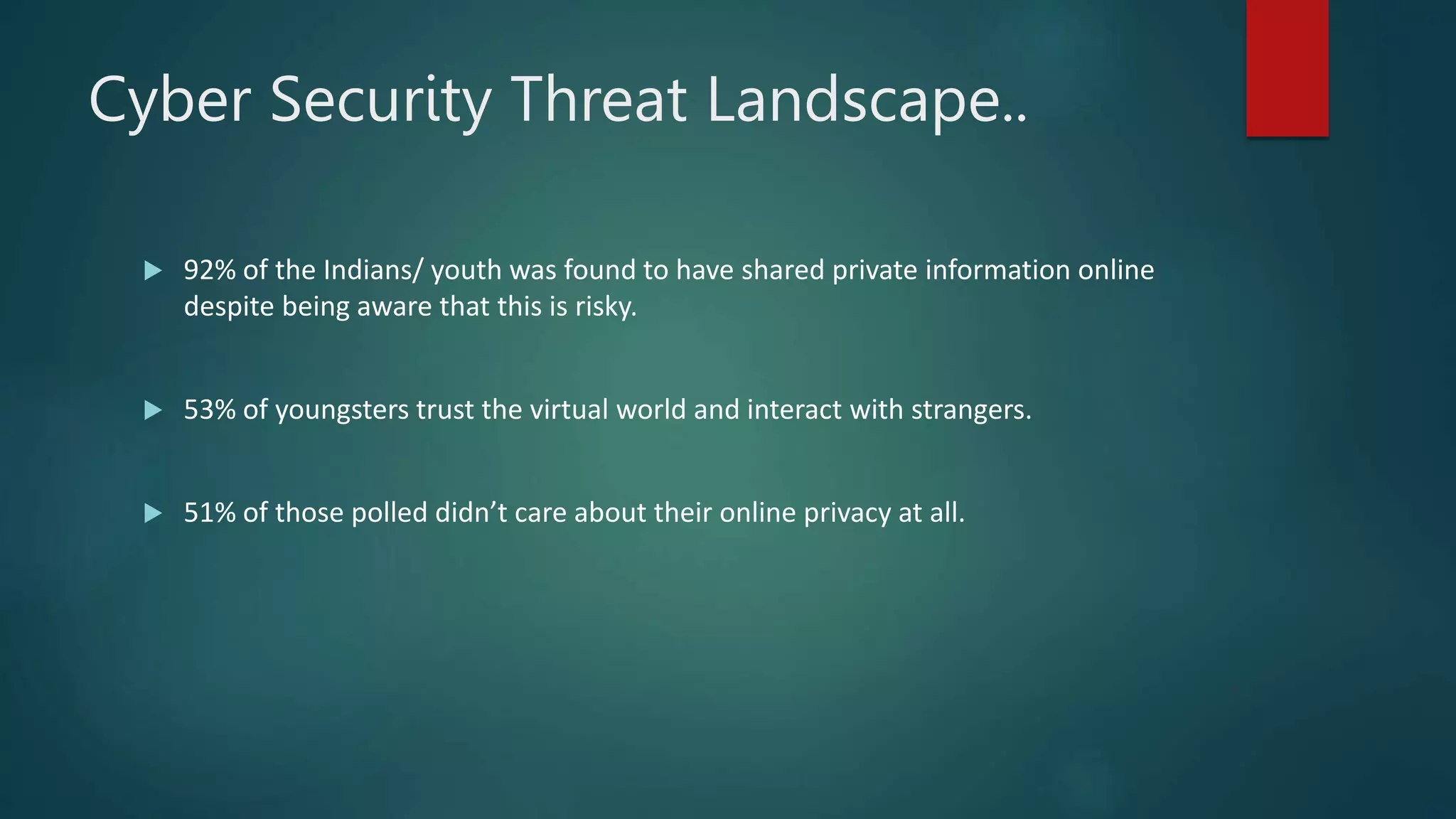
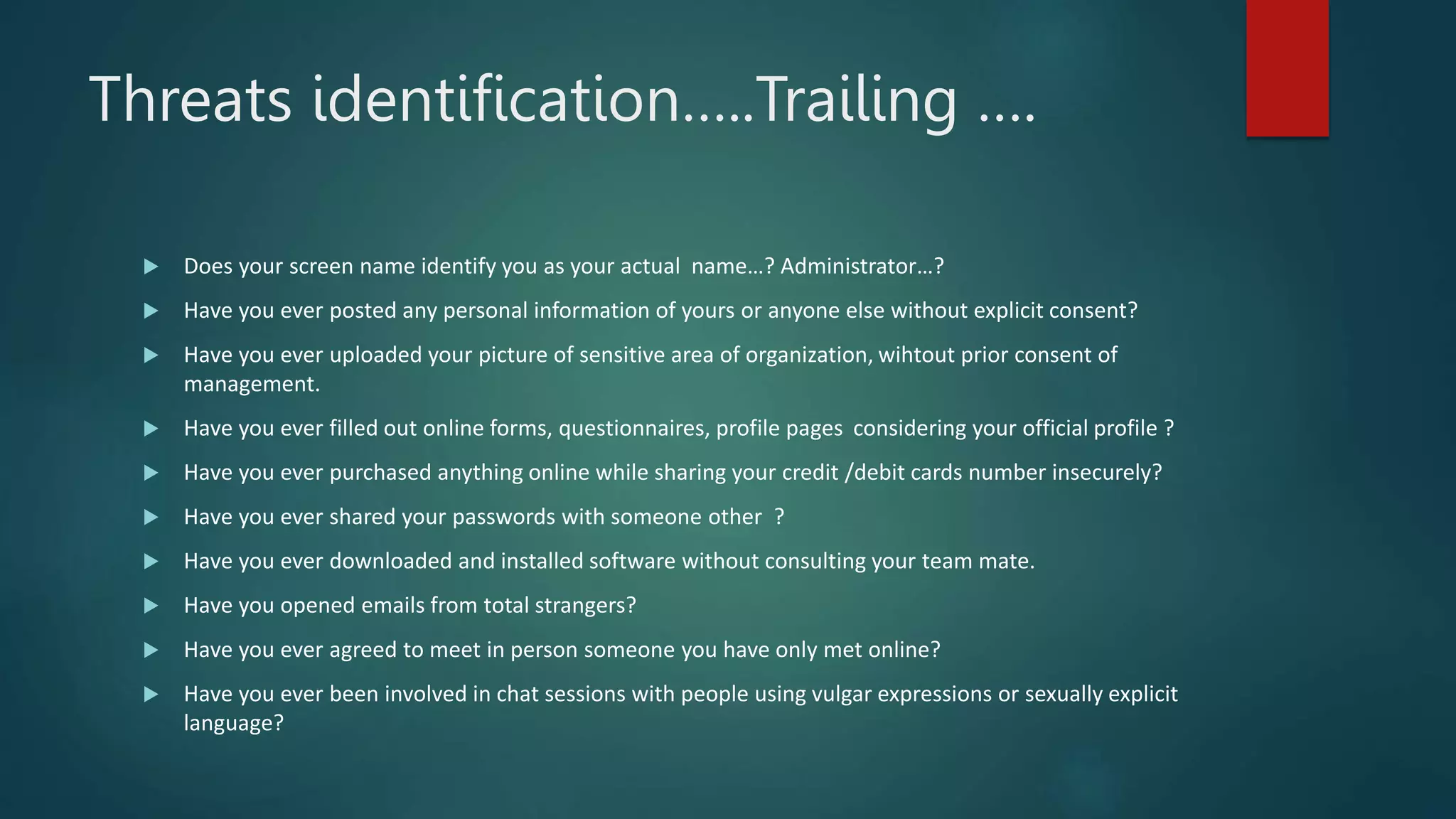
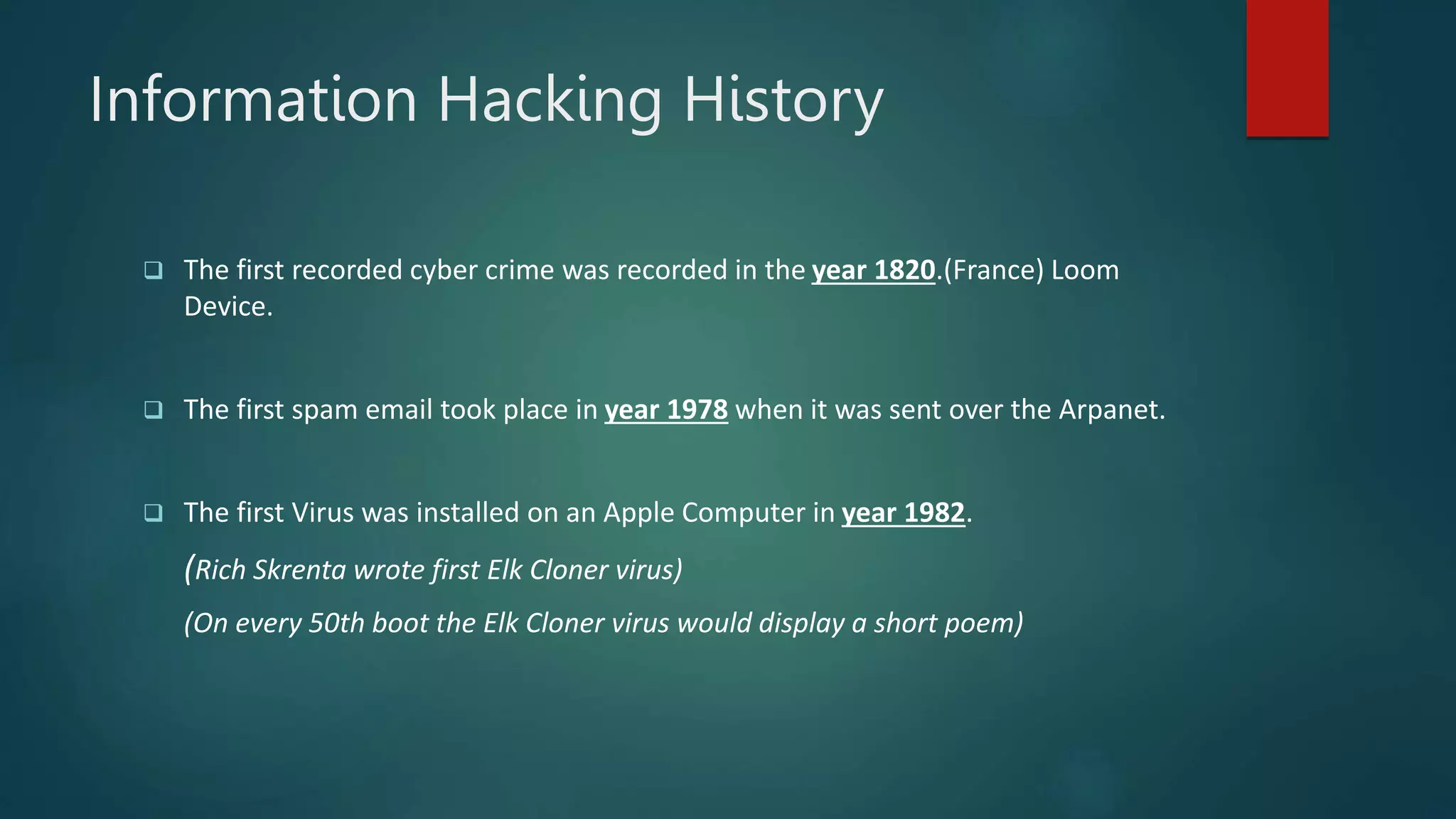
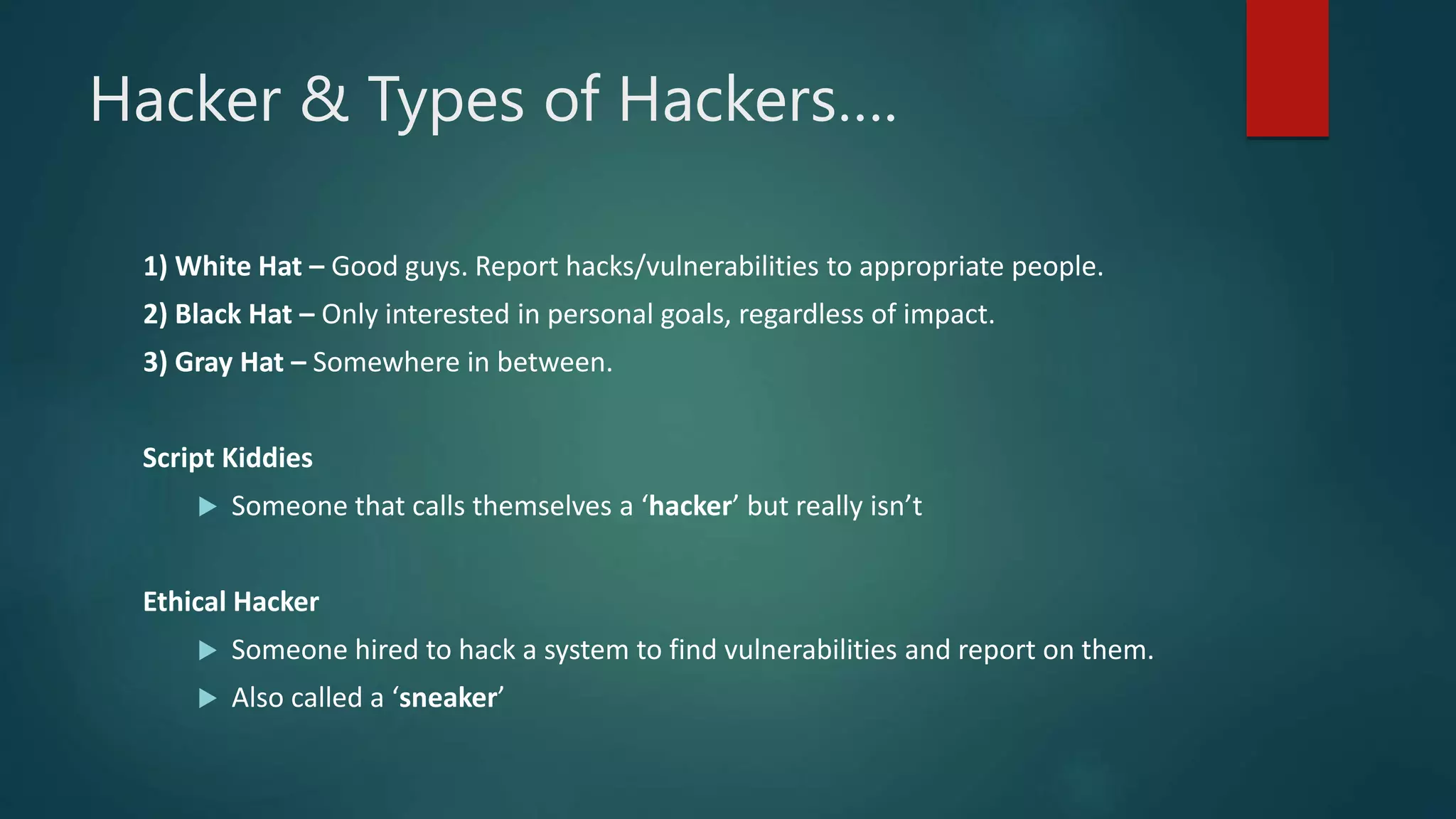
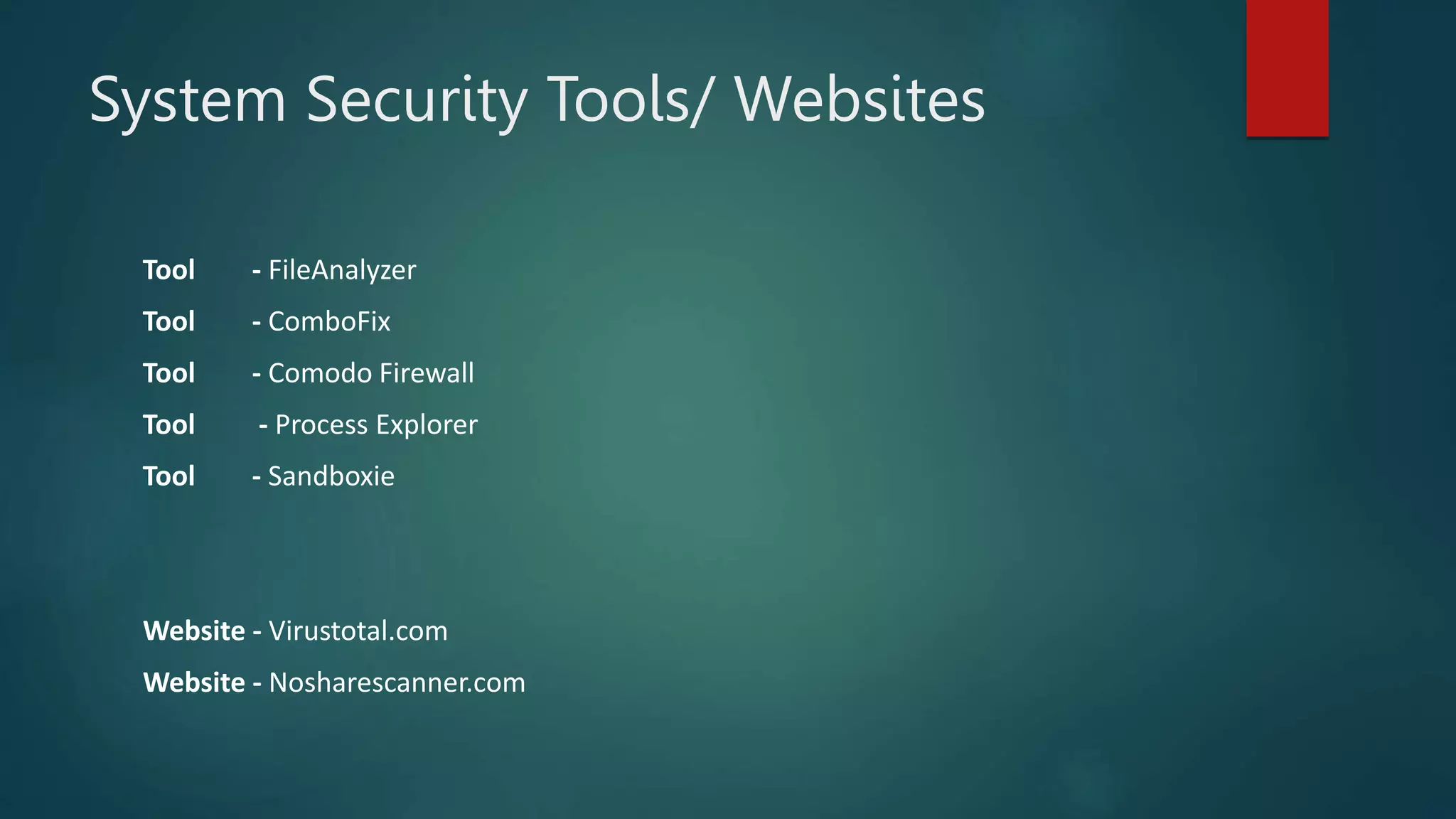
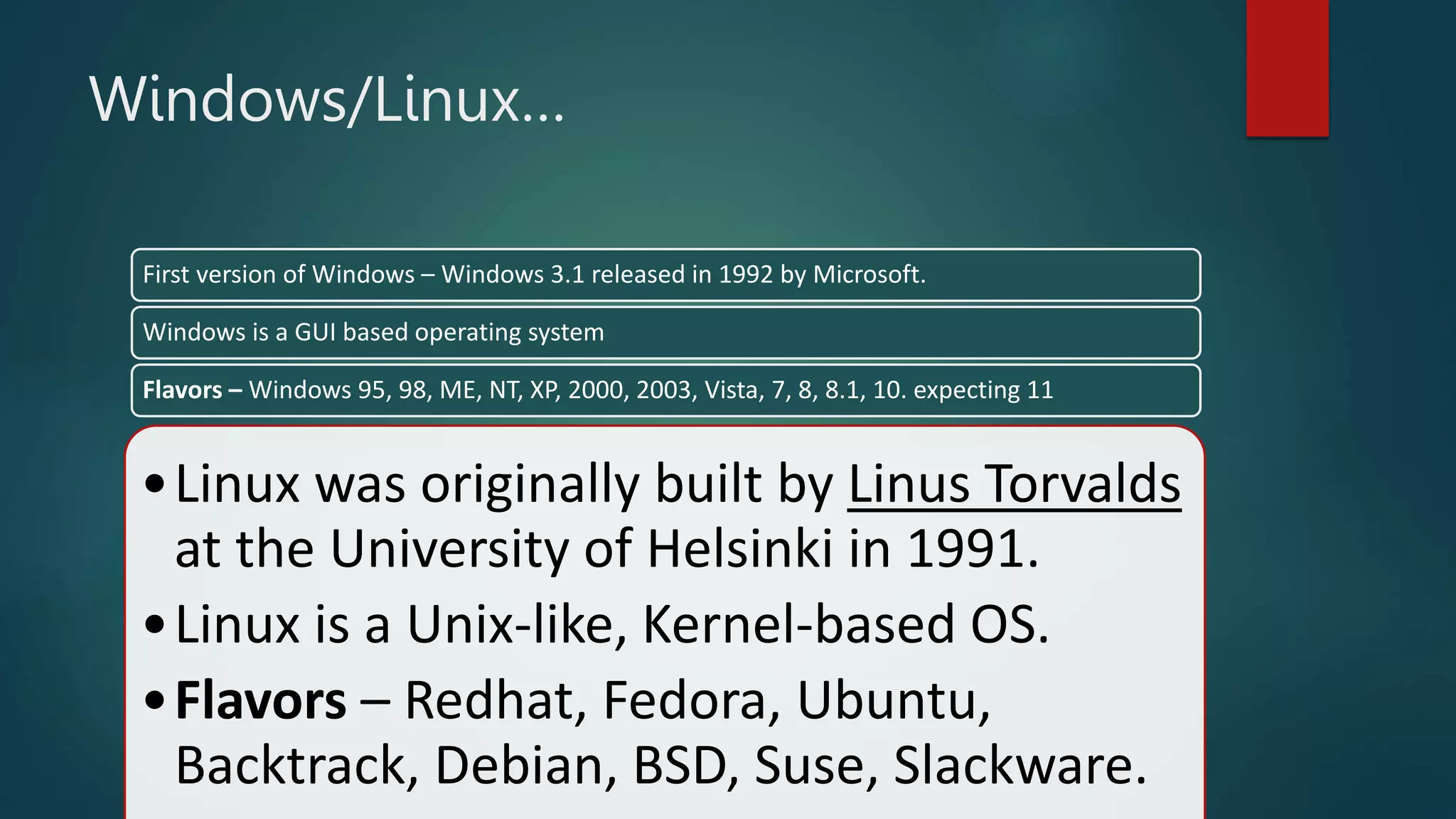
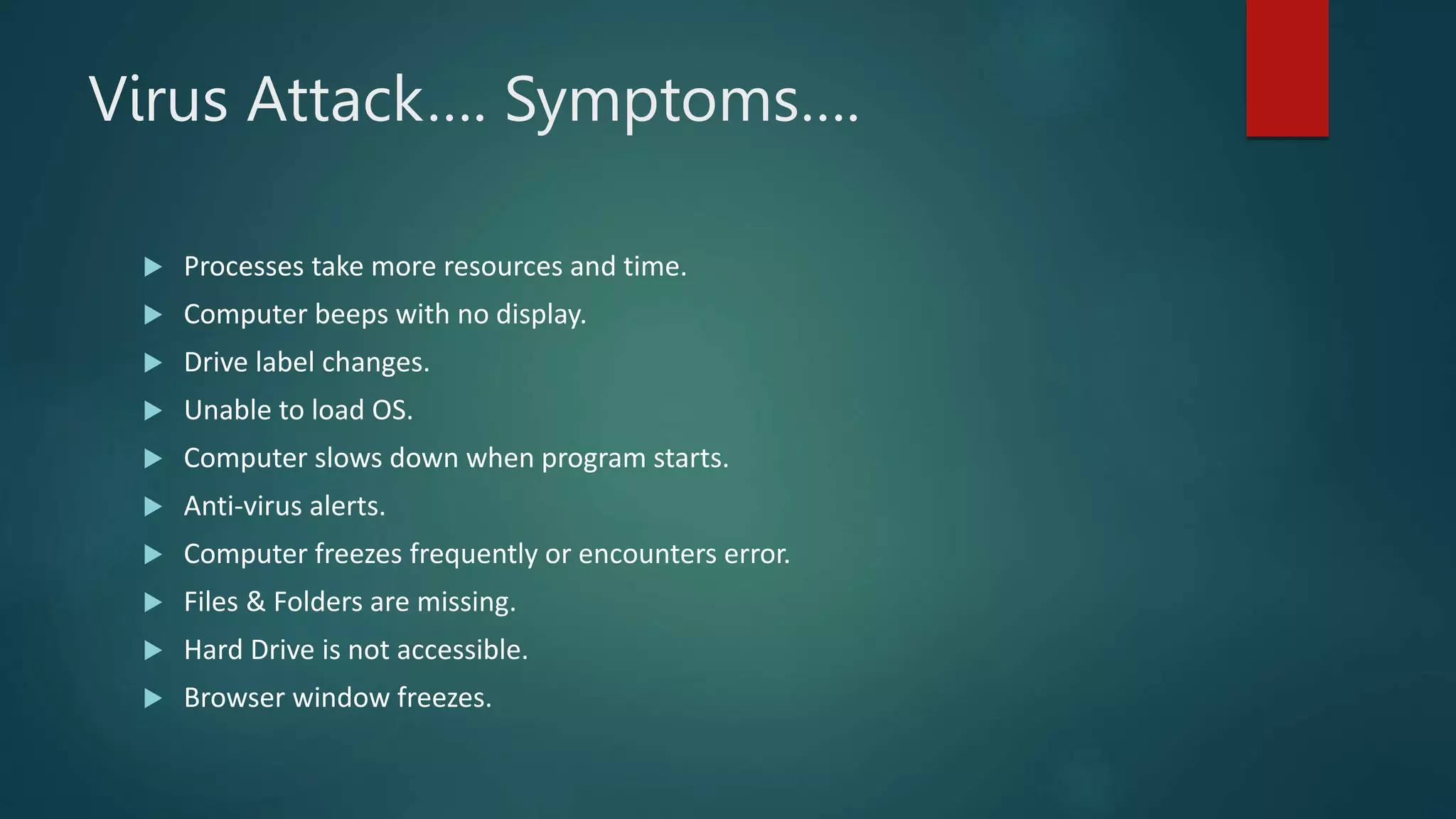
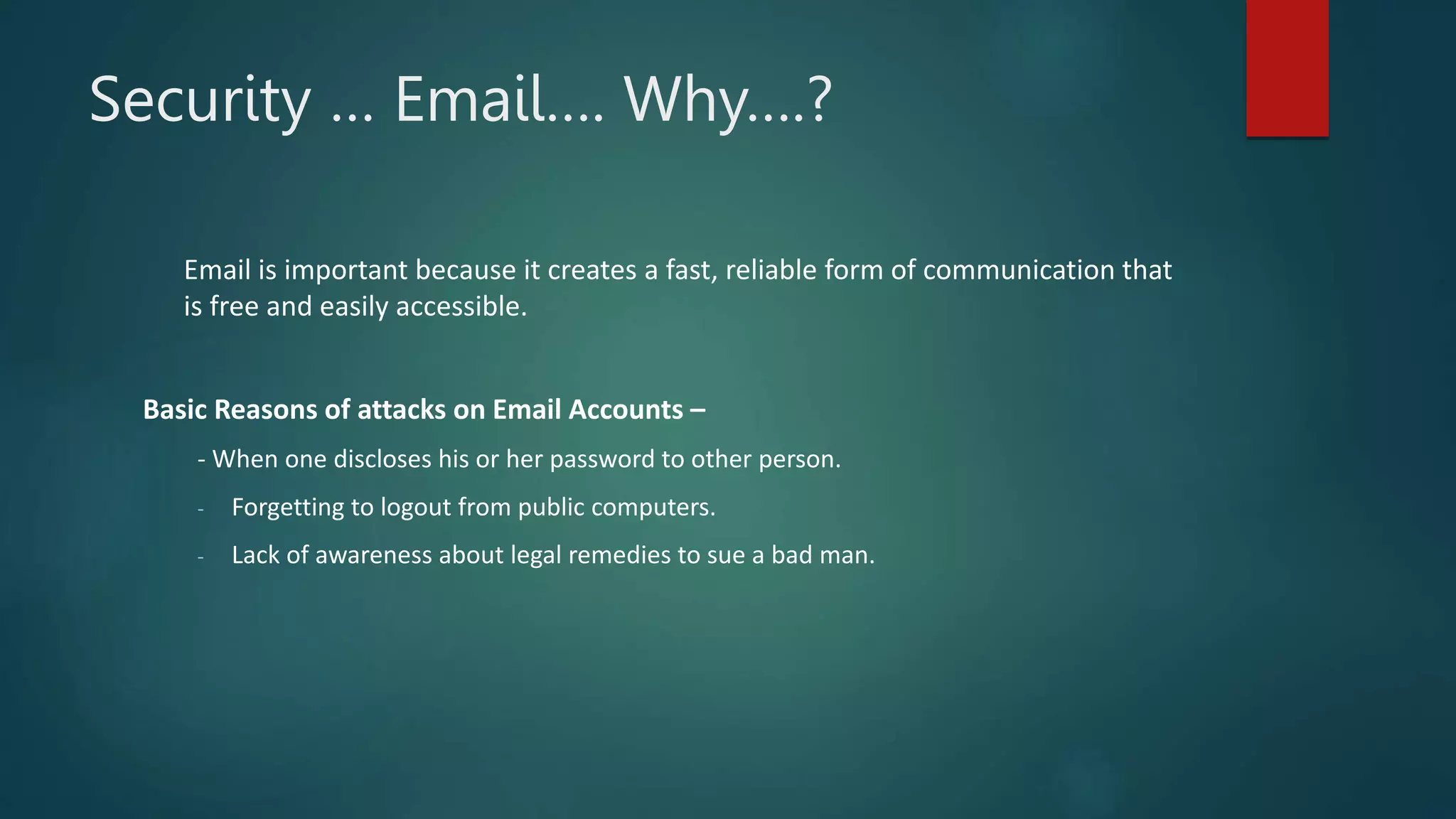
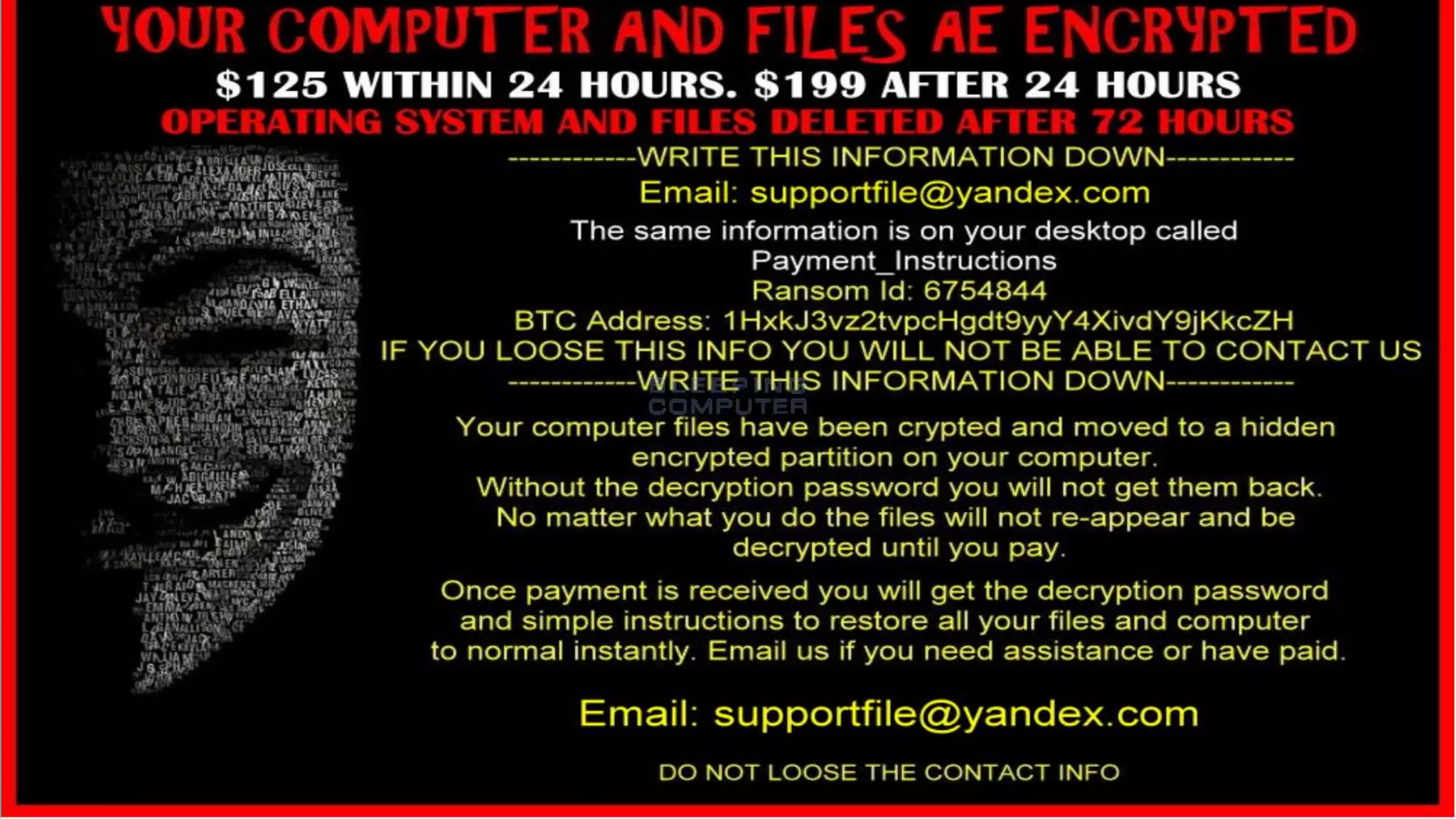
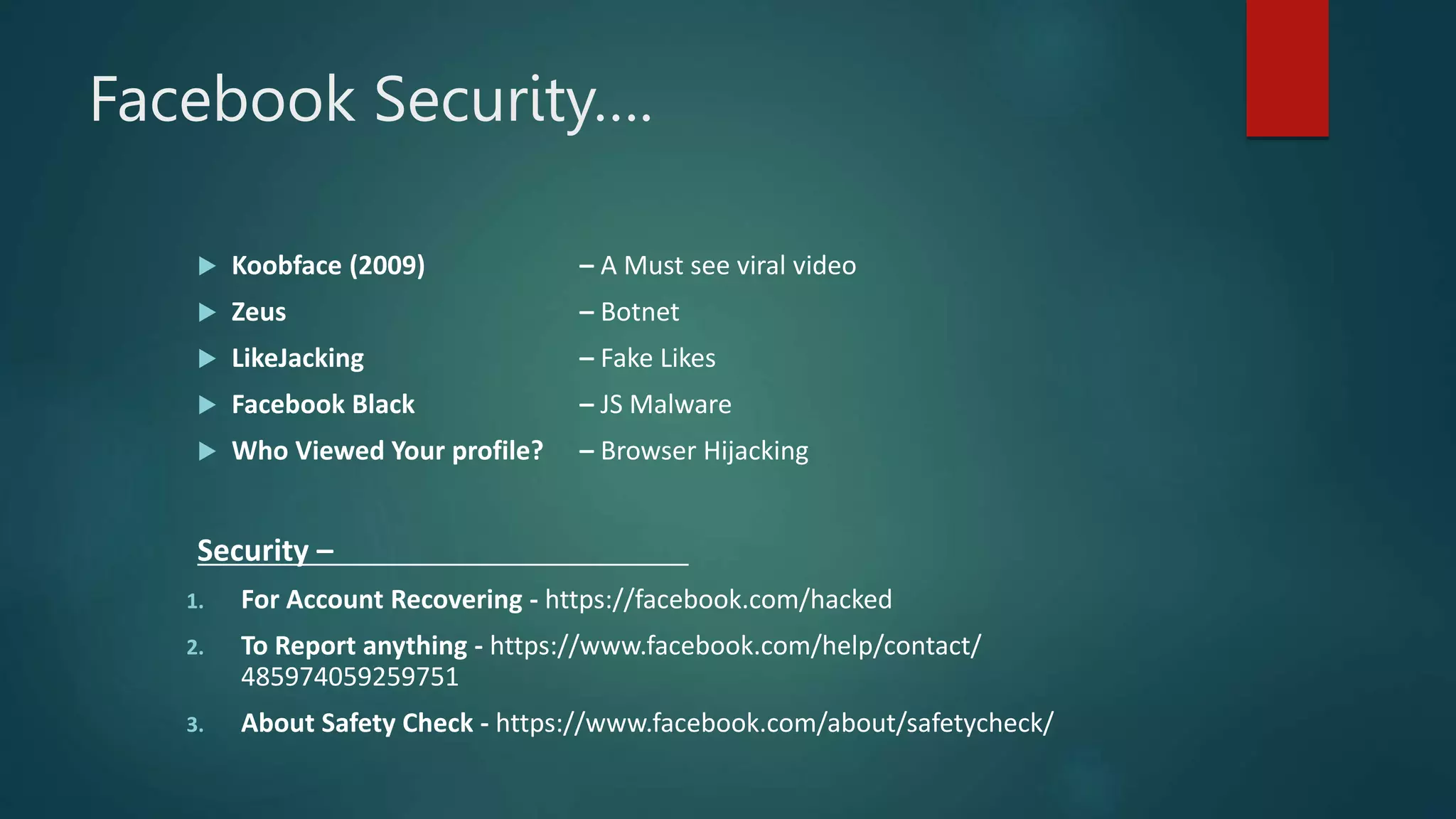
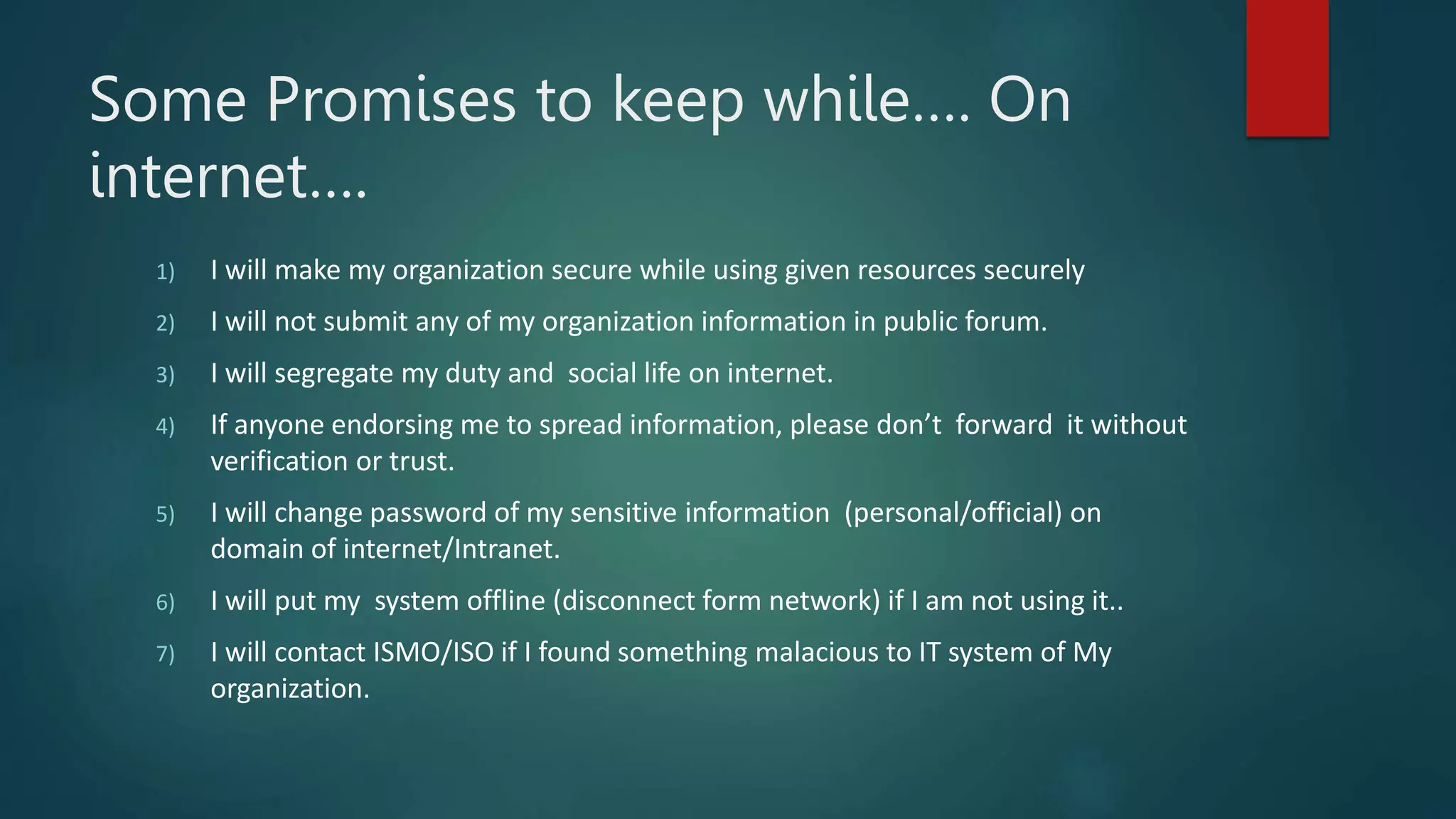
This document provides an overview of cyber security topics and best practices. It discusses basics of information security, standards like ISO 27001, and how to harden operating systems. It covers password security, securing USB devices, email security, ransomware prevention, safe browsing, social media security, and mobile device security. Key advice includes using strong and unique passwords, encrypting USB drives, backing up data, updating software, and avoiding public Wi-Fi. The document also discusses cyber threats, types of hackers, and security incidents from the past as examples.