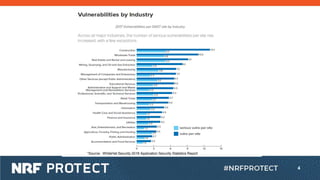
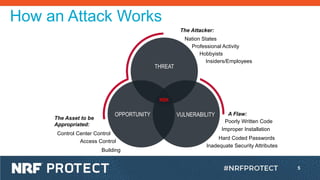
The document discusses the risks of IoT devices and the need for improved security practices. It notes that many applications contain inherited vulnerabilities from reused components and fail to meet basic security standards. The document outlines UL's new 2900 security certification for network-connected products which evaluates vendors' risk management processes and requires documentation of a product's design, use, vulnerabilities, and security controls.