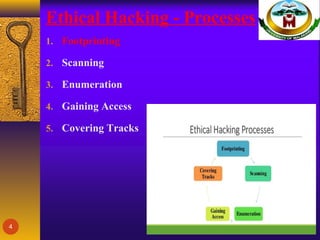
This document discusses ethical hacking and footprinting. It defines footprinting as the process of collecting information about an organization, its network, IP addresses, and employees through open sources like Google searches and social media sites. Footprinting is the first step ethical hackers use to gather technical information and identify vulnerabilities without damaging systems or stealing data. The document outlines different types of passive and active footprinting techniques and explains why footprinting is an important security practice for organizations to evaluate their online exposure and vulnerabilities. It provides recommendations for organizations to limit the information available online and regularly evaluate their digital footprint to combat unauthorized footprinting.