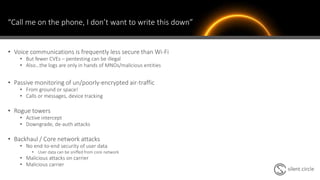
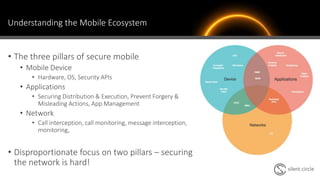
The document discusses the cybersecurity risks associated with mobile communications, particularly highlighting various case studies involving financial firms where sensitive information was intercepted using rogue cell towers and malicious applications. It emphasizes the insufficient regulations and security standards in mobile networks, which allow such attacks to occur, and outlines practical recommendations for enterprises to enhance their communication security. Key solutions include using secure communication tools and training employees on the vulnerabilities of traditional voice calls.








![What about the network?
“As early as 1996, members of Congress experienced calls being illegally
intercepted, however no technological solution to this problem has been
systematically deployed and it remains to this day.”
April 2017 Dept. Homeland Security. Study on Mobile Device Security
“In the United States, there are
no regulations requiring carriers
to run encryption or provide
privacy protections to users on
their networks”
“The caller ID display is
unauthenticated and can be
made to display any data,
including fraudulent
information.”
“[mobile devices] remain fully functional when running on non-encrypted
networks; no notification is provided to the user when operating in this mode.”](https://image.slidesharecdn.com/201805-finseccyberv5-190103210339/85/Cybersecurity-Risks-In-the-Mobile-Environment-10-320.jpg)
![What about the network?
“LTE standards do not provide confidentiality protection for user traffic as
the default configuration”
“integrity protection for user traffic is explicitly prohibited”
“…security capabilities provided by LTE are markedly more
robust [than previous]…yet [LTE systems] coexist with
previous cellular infrastructure.”
“Current mobile devices do not provide the option for a user to know if
their [device’s] connection is encrypted...”
December 2017 NIST SP 800-187 Guide to LTE Security
[1] Jian A. Zhang, Peng Cheng, Andrew R. Weily, Y. Jay Guo. 2014. Towards 5th Generation Cellular Mobile Networks . Australian Journal of Telecommunications and the Digital Economy, Vol 2,
No 2, Article 34. http://doi.org/10.18080/ajtde.v2n2.34(link is external). Published by Telecommunications Association Inc. ABN 34 732 327 053. https://telsoc.org](https://image.slidesharecdn.com/201805-finseccyberv5-190103210339/85/Cybersecurity-Risks-In-the-Mobile-Environment-11-320.jpg)
![Is Old News still News?
• To security professionals, telecommunication risk is
nothing new[1]!
• Why hasn’t this situation (drastically)?
• Thousands of companies in hundreds of countries
• Tens of technologies
• ~4.7 billion deployed phones
• 2G/3G fallback is consistent – GSM is still prevalent
• Making cellular networks at scale is very hard work
• CVEs may not exist – pentesting can be illegal!
[1] April 2016, NISTR 8071. Jeffrey Cichonski (NIST), Joshua Franklin (NIST), Michael Bartock (NIST) LTE Architecture Overview and Security Analysis
http://theinternetofthings.report/Resources/Whitepapers/
8965b6c5-40e0-448b-950a-a3adc428144b_
The%20Global%20State%20of%202G,%203G,%204G,%20and%205G.pdf](https://image.slidesharecdn.com/201805-finseccyberv5-190103210339/85/Cybersecurity-Risks-In-the-Mobile-Environment-12-320.jpg)
![Is Old News still News?
• Why has this situation changed, drastically?
• Access to low-cost radio hardware
• In 2014
• “Baseband attacks are considered extremely difficult”[1]
• “system costs as much as $400,000”[2]
• In 2016, GSM ISMI Catcher for $1400[3]
• In 2018, “The cost of the hardware is about €1,250…”[4]
• Ettus USRP, HackRF, BladeRF, etc
• Prevalence of readily-available software
• OpenBTS, OpenBSC, OpenLTE
• Proactive nation-state attackers[5] puts backhaul & core at greater risk
[1] https://www.welivesecurity.com/2014/08/28/android-security-2/
[2] https://resources.infosecinstitute.com/stingray-technology-government-tracks-cellular-devices/
[3] https://securityaffairs.co/wordpress/41513/hacking/low-cost-imsi-catcher-lte.html
[4] https://www.evilsocket.net/2016/03/31/how-to-build-your-own-rogue-gsm-bts-for-fun-and-profit/
[5] https://securelist.com/regin-nation-state-ownage-of-gsm-networks/67741/](https://image.slidesharecdn.com/201805-finseccyberv5-190103210339/85/Cybersecurity-Risks-In-the-Mobile-Environment-13-320.jpg)