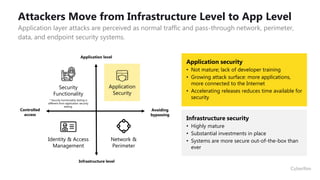
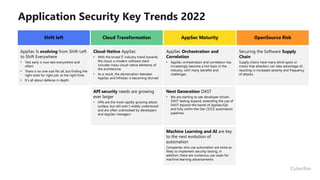
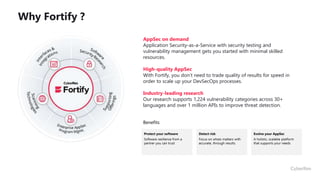
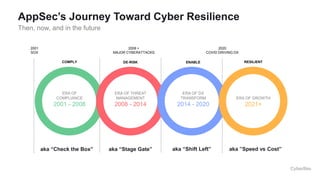
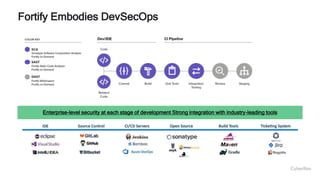
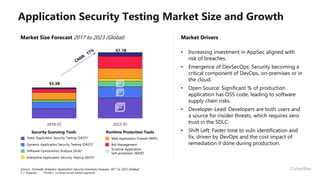
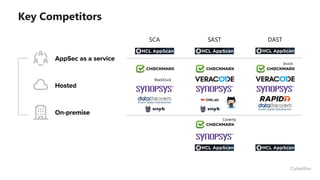
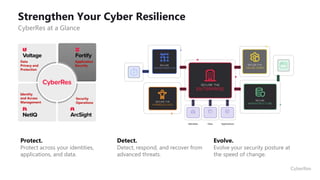
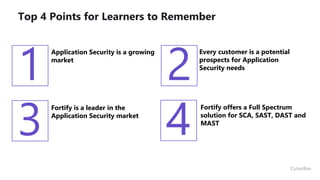
This document provides an overview of application security challenges and trends. It discusses how attacks have moved to target applications directly rather than just infrastructure. It also notes that security is often an afterthought for developers focused on speed and that maturity varies. Key trends include shifting security left in the development process, addressing open source risks, and leveraging tools like machine learning. Stakeholders have different priorities around protecting the organization versus meeting deadlines. Primary use cases involve finding and fixing vulnerabilities throughout the development lifecycle. The Fortify platform aims to provide application security that scales with development needs.