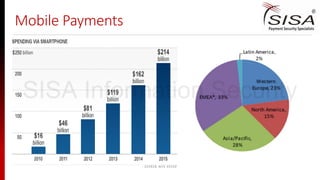
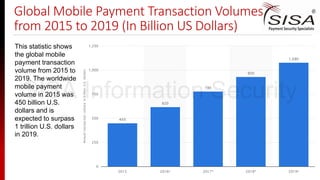
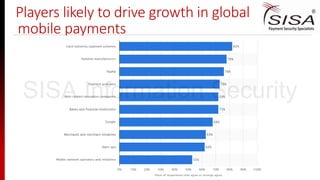
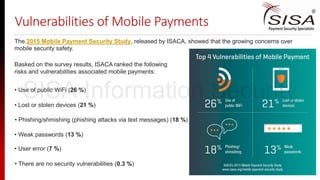
The document discusses emerging trends in payment security, particularly focusing on mobile and NFC technologies, highlighting significant growth in mobile payment transactions from 2015 to 2019. It reviews various advancements and innovations by companies like PayPal, American Express, and Samsung in enhancing mobile payment systems while also addressing the security vulnerabilities these new methods introduce. Key risks associated with mobile payments are identified, including device theft, data breaches, and phishing attacks, stressing the need for robust security protocols and training in payment environments.















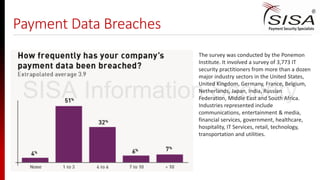


![Wendy’s Card Data Breach
As many as 6000 locations were affected by the breach in
December 2015
Jimmy John's, Rainforest Cafe, Morton's, P.F. Chang's, and Dairy
Queen have been victims of credit card hacks since 2014.
"Traditionally [POS systems] have been some of the weakest
spots [in a restaurant's operations... because restaurant
owners] tend to do really sloppy things like enable the same
password for each system.“, Security Experts.
In all the above cases, Cards impacted by this event appear to
be those swiped at the stores, and did not include those cards
entered manually or online.
SISA Information Security](https://image.slidesharecdn.com/esisaisacabglv13-160219053621/85/New-trends-in-Payments-Security-NFC-Mobile-23-320.jpg)