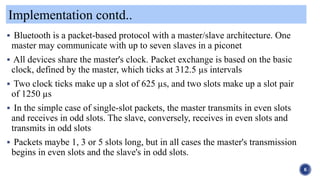
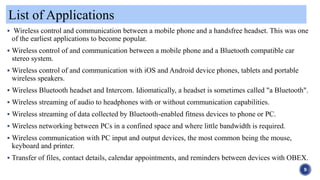
Bluetooth is a wireless technology standard used for exchanging data over short distances. It was originally conceived as a wireless alternative to RS-232 data cables. Bluetooth uses short-wavelength UHF radio waves to connect devices like mobile phones, headphones, laptops and other electronic devices. It employs a frequency hopping spread spectrum technique to avoid interference and jamming between other devices. Bluetooth implements security measures like encryption and authentication to keep communications private and secure between paired devices. Common applications of Bluetooth include wireless headsets, streaming audio to headphones, wireless keyboards and mice, and transferring files between devices.







![References
• "Basics Bluetooth Technology Website". Bluetooth.com. 23 May 2010.
• "Bluetooth.org". Bluetooth.org. Retrieved 3 May 2011.
• "Brand Enforcement Program". Bluetooth.org. Archived from the original on 4
November 2013. Retrieved 2 November 2013.
• "The Bluetooth Blues". Information Age. 24 May 2001. Archived from the original
on 22 December 2007. Retrieved 1 February 2008.
• "Bluetooth traveler". hoovers.com. Archived from the original on 11 January 2011.
Retrieved 9 April 2010.
• Google Images
[https://www.google.com/search?q=bluetooth+gif&source=lnms&tbm=isch&sa=X
&ved=0ahUKEwjvjKGK7PHfAhVMpI8KHe3eABsQ_AUIDigB&biw=1319&bih
=672#imgrc=Jz5fCtFclxU_fM:]
• Youtube video[https://www.youtube.com/watch?v=LLNtZKpL0P8&t=7s]
10](https://image.slidesharecdn.com/firstcnpresentation-190220000308/85/Bluetooth-10-320.jpg)
