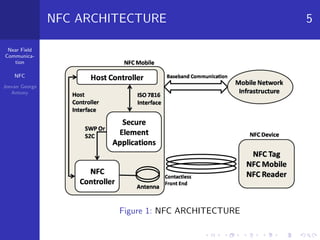
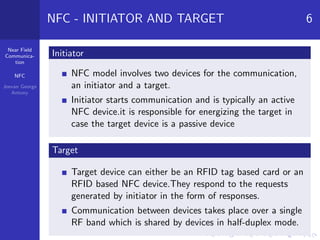
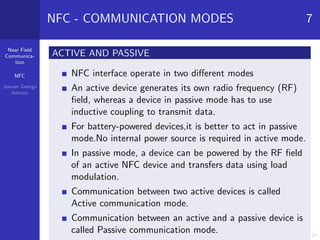
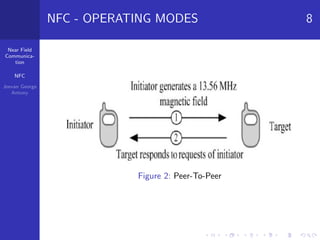
Near field communication (NFC) is a short-range wireless technology that allows data exchange between devices when touched together or brought within close proximity. NFC operates at 13.56 MHz and can communicate at speeds up to 424 kilobits per second within a 10 centimeter range. The document discusses NFC architecture, communication modes, operating modes, threats including eavesdropping and data modification, and defenses such as using encryption to establish a secure channel. It also provides applications of NFC like contactless payments and digital content sharing.










![Near Field
Communica-
tion
NFC
Jeevan George
Antony
References I 19
1 Naveed Ashraf Chattha. ”NFC - Vulnerabilities and De-
fense” - Short Paper, published in Information Assurance
and Cyber Security (CIACS), 2014 Conference on 12-13
June 2014, pp. 35-38 , publisher- IEEE.
2 ”Near Field Communication (NFC)Technology and Mea-
surements”-White Paper Roland Minihold-06-2011(1MA1825e)
3 ISO/IEC 18092. ”Near Field Communication - Interface
and Protocol,”-2004.
4 Near Field Communication’ - White Paper, Ecma/TC32-
TG19/2005/012, Internet: www.ecma international.org, 2005
[May. 24, 2014].
5 NFC-Near Field Communication, Reader/Writer Operating
Mode [May. 28, 2014].](https://image.slidesharecdn.com/nfcfinal-150811164912-lva1-app6892/85/NEAR-FIELD-COMMUNICATION-NFC-19-320.jpg)

