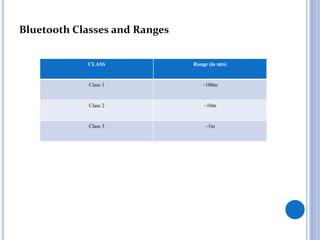
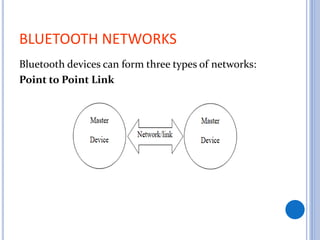
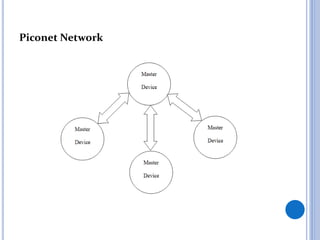
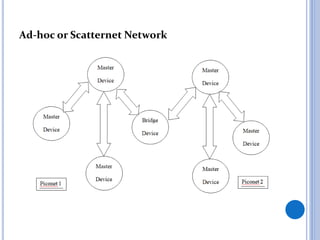
This document is a seminar report on Bluetooth network security submitted in partial fulfillment of a Bachelor of Technology degree. It discusses Bluetooth technology, including its architecture and classes/ranges. It covers security aspects at the link and application layers and tools that can be used to attack Bluetooth networks, like Bluejacking and Bluesnarfing. It also lists advantages like low cost and wireless capability, disadvantages like short range and hackability. Applications discussed include wireless headphones, mobile device connectivity, and medical sensors.










![REFERENCES
o 1.Data Communication and Networking, 4th edition, Behrouz A
Forouzan.
o 2.http://trifinite.org
o 3.http://en.wikipedia.org/wiki/Bluetooth/
o 4.Wireless Network Security 802.11, Bluetooth and Handheld
Devices, National Institute of Standards and Technology, Technology
Administration, U.S. Department of Commerce.
o 5.BLUETOOTH SPECIFICATION Version 2.1 + EDR [vol 0] ,
www.Bluetooth.com
o 6.Andreas Becker, “Bluetooth Security and Hacks”, Ruhr-University
Bochum, 2007.
o 7.Essential Bluetooth hacking tools, http://www.security-
hacks.com/2007/05/25/essential bluetooth hacking-tools.
o 8.Marek Bialoglow, “Bluetooth Security Review”,
http://www.securityfocus.com/infocus/1830](https://image.slidesharecdn.com/seminarppt-180330125538/85/Bluetooth-Network-security-18-320.jpg)
