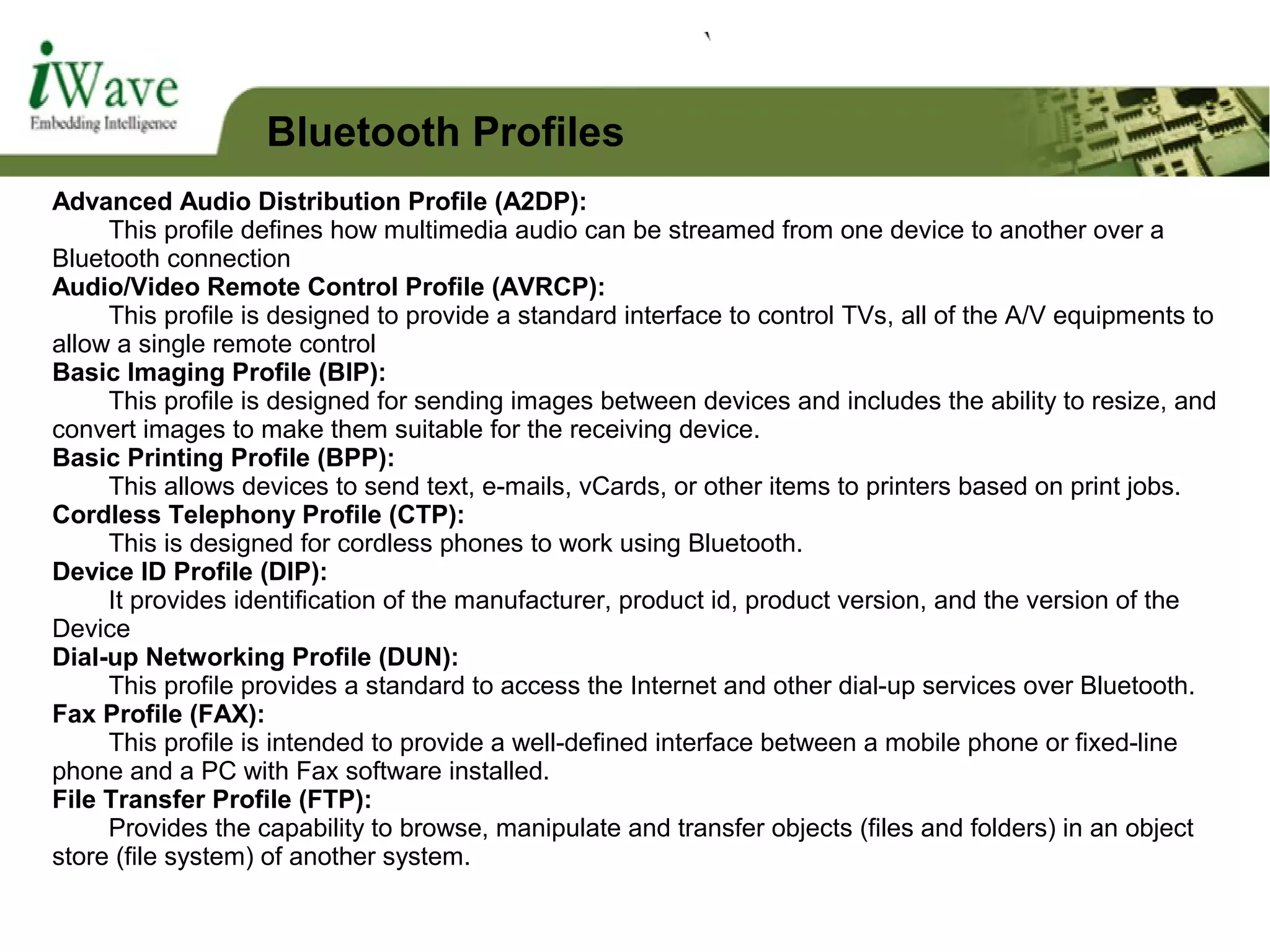
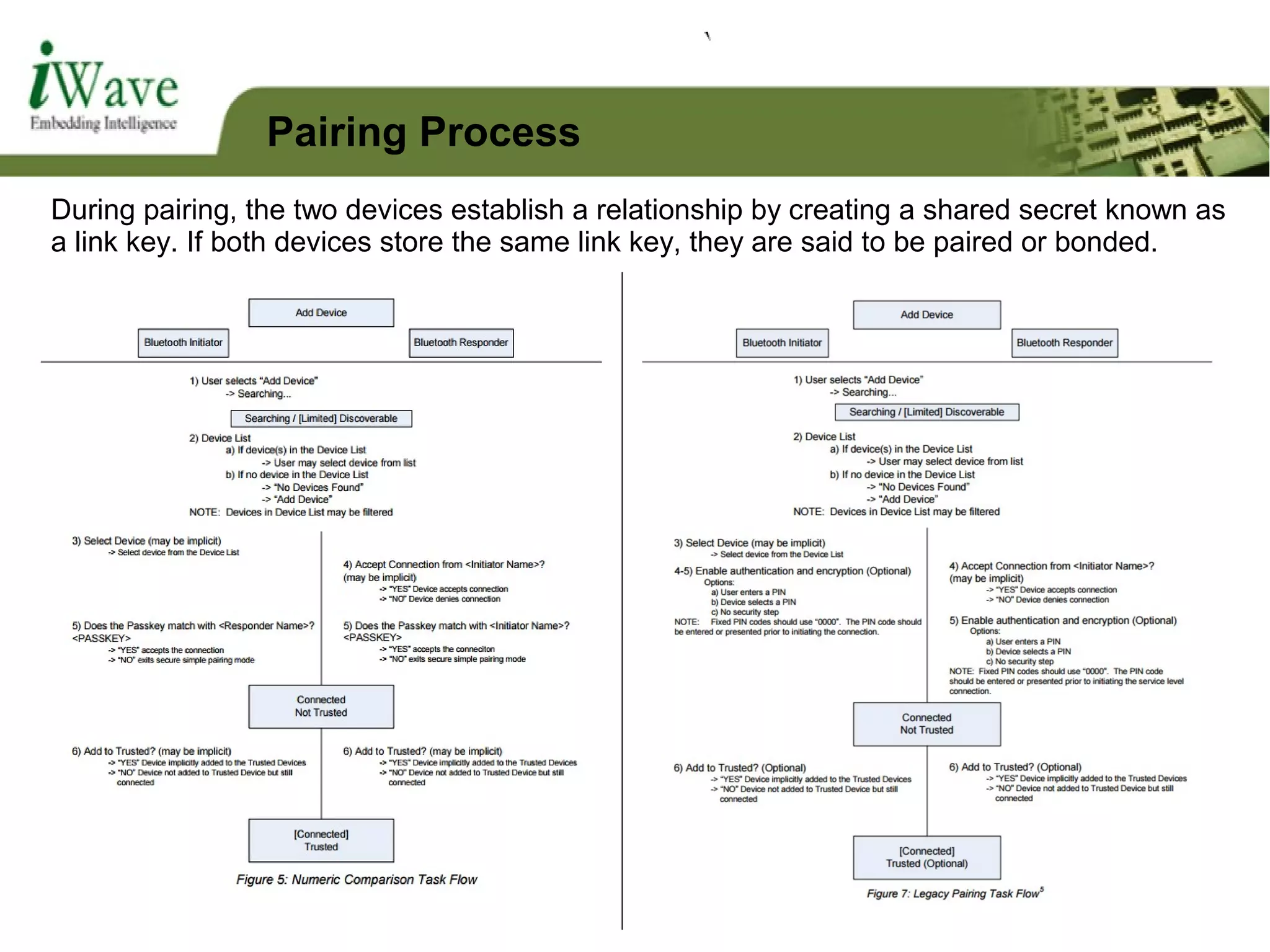
Bluetooth and Profiles
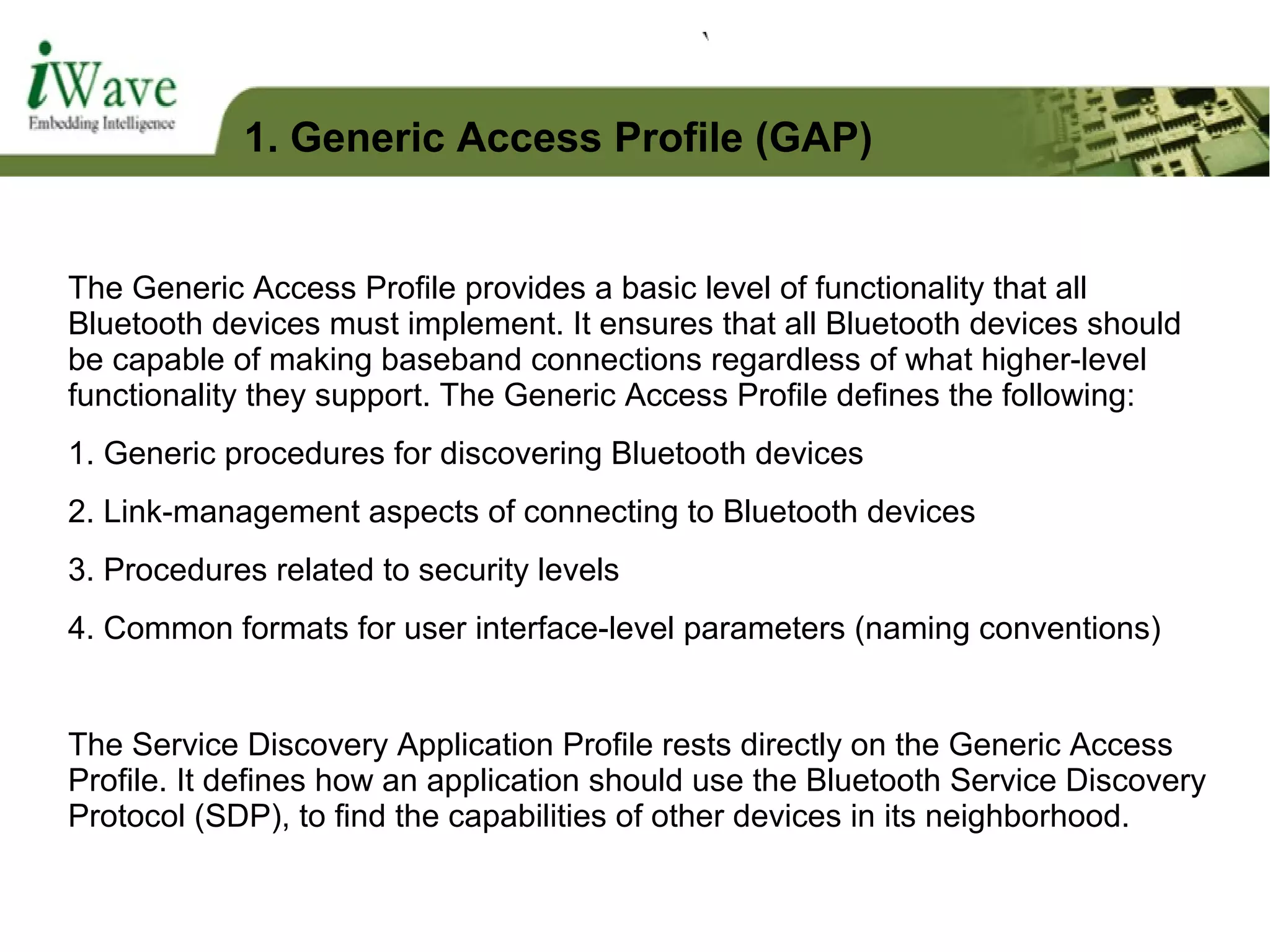
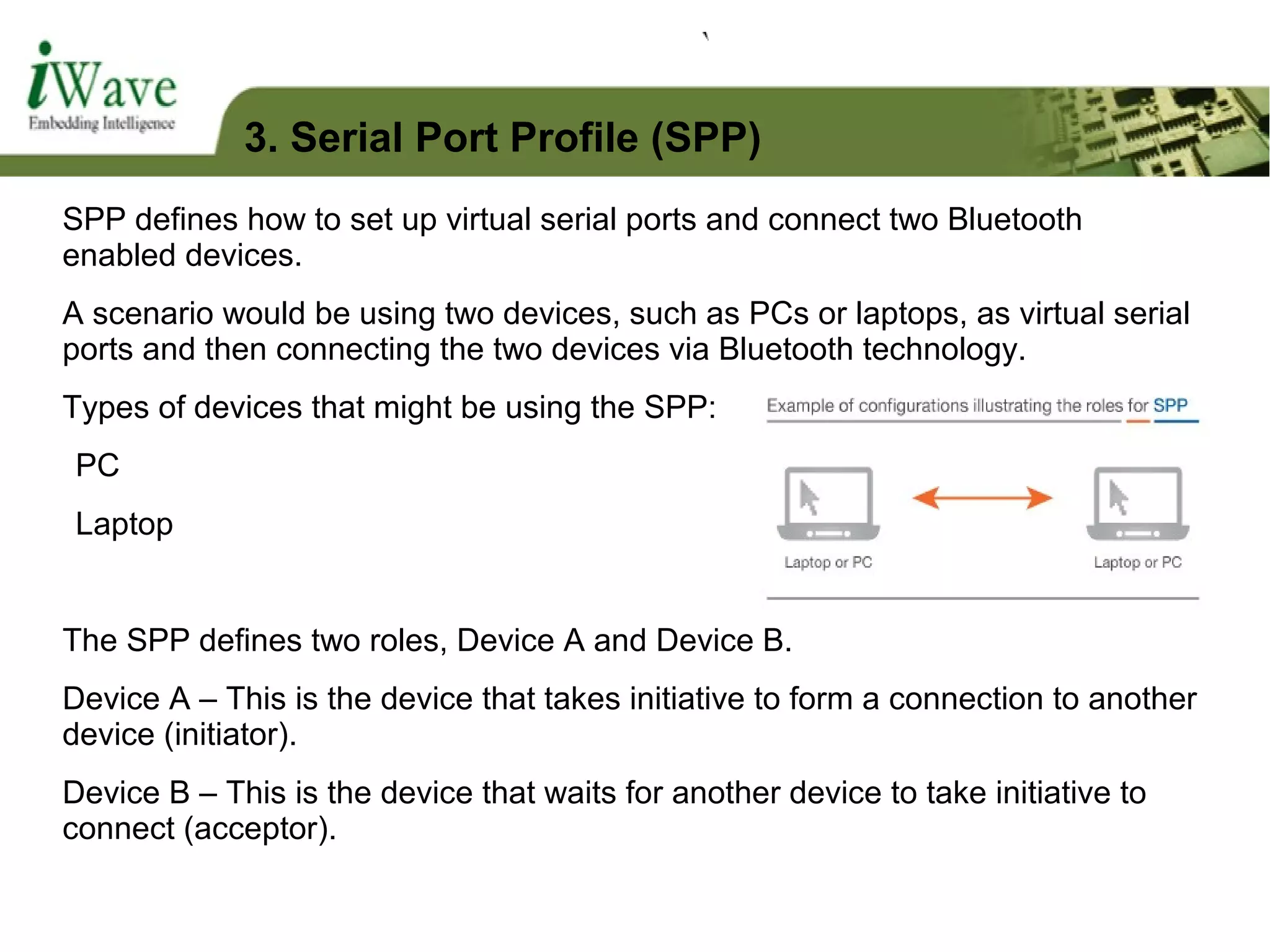
The document discusses Bluetooth technology and Bluetooth profiles. It provides an overview of Bluetooth including its history and development of different Bluetooth versions. It describes Bluetooth architecture and core system components. It also explains various Bluetooth profiles such as Generic Access Profile, Object Exchange Profile, Serial Port Profile, and File Transfer Profile which define how Bluetooth devices communicate and establish connections.
























![[HKEY_LOCAL_MACHINESoftwareMicrosoftBluetoothTransportsPnP{<GUID>}]
"flags"=dword:80000000
"driver"="bthusb.dll"
"resetdelay"=dword:0
"PacketSize"=dword:200
"BlockSize"=dword:5
[HKEY_LOCAL_MACHINESoftwareMicrosoftBluetoothsys]
"Power"=dword:1 ; Radio on by default
"ScanMode"=dword:3 ; Radio is discoverable
"DisableAutoSuspend"=dword:1 ; Allow suspend when connected
[HKEY_LOCAL_MACHINEDriversUSBLoadClients5656_37139DefaultDefaultBluetooth_USB_Driver]
"DLL"="bthusb.dll"
[HKEY_LOCAL_MACHINEDriversSDCARDClientDriversCustomMANF-041B-CARDID-9330-FUNC-1]
"Dll"="bthsdio.dll"
HCI Transport layer driver - Registry](https://image.slidesharecdn.com/btandprofiles-160114045846/75/Bluetooth-and-profiles-on-WEC7-43-2048.jpg)



