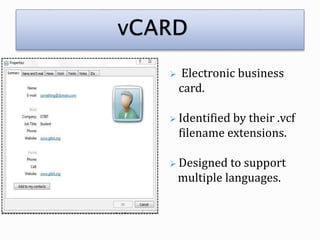
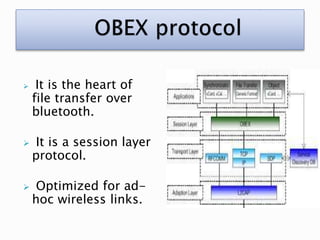
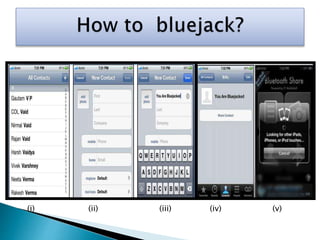
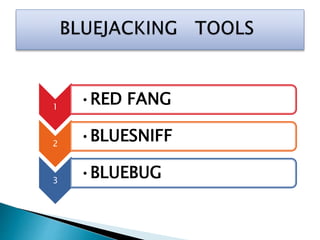
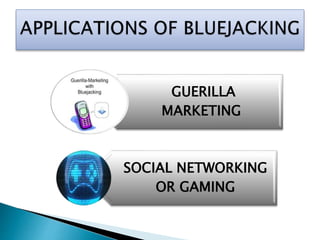
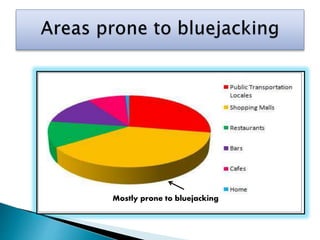
This document discusses bluejacking, which is sending unsolicited messages to Bluetooth-enabled devices by sending a vCard containing contact information. It was first used in Malaysia for advertising. The document outlines the history of bluejacking and the technologies involved, including Bluetooth, vCards, and the OBEX protocol. It describes how to perform bluejacking and lists some applications like guerilla marketing. Advantages include easy data transfer, but disadvantages include security risks and potential irritation of recipients. The conclusion states that bluejacking could revolutionize advertising through mobile devices.







![[1] International Journal of Engineering Trends
and Technology (IJETT) – Volume 4 Issue 7 July,
2013.
[2] International Journal Of Engineering And
Computer Science Volume 2 Issue 6 June, 2013.
[3] International Journal of Distributed and
Parallel Systems (IJDPS) Vol.3, No.1, January
2012.](https://image.slidesharecdn.com/nehasonali-150505161034-conversion-gate01/85/Bluejacking-16-320.jpg)
