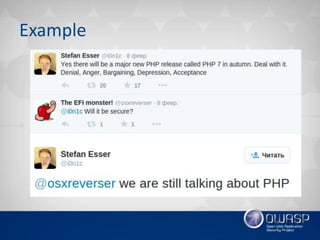
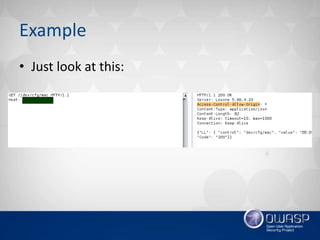
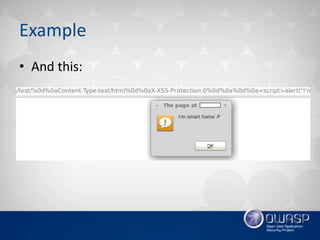
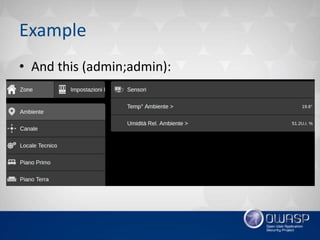
This document summarizes recent trends in web application security vulnerabilities. Client-side attacks like XSS remain prominent along with emerging threats involving cloud computing, big data, and the Internet of Things. Old vulnerabilities persist in widely used software while new issues are found in new technologies. Overall, the growth of web applications and their interactions creates many new attack surfaces despite ongoing security improvements, ensuring hackers will continue finding novel ways to exploit systems.




















![Example
• The name of function has changed, but vulnerability is still there,
AFAICS
...
function fsarcCreate($archive, $files)
...
$cli = 'zip -r -9 -q -S "'.$archive.'" "'.implode('" "', $files).'"';
exec($cli, $e, $r);
...
foreach($_POST['files'] as $file)$list[] = $_CUR_PATH.'/'.$file;
...
if(!function_exists('fsarcCreate') || ($arcfile = fsarcCreate($arcfile, $list))
=== false)die('Failed to create archive, please check
"system/fsarc.php" script.');
...](https://image.slidesharecdn.com/2-150301070554-conversion-gate02/85/2-1-Web-application-Security-Trends-Omar-Ganiev-24-320.jpg)
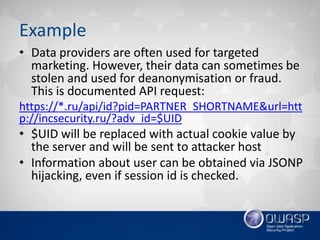
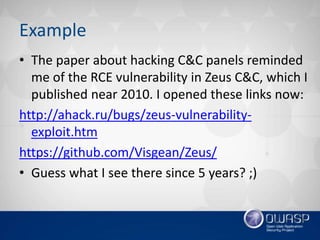
![Example
• This is a small example, probably there’re more critical
vulnerabilities in this popular botnet C&C. BTW, how
do you find vulnerabilities in the source code?
• Paper on contemporary automatic program analysis
mostly tells about grep =)
• Personally I use grep with lovely regular expressions:
w*(include|require)(_once)?[s(]+(?!s*('[^']*'|"[^"]*"|
)[@s.]*(urlencode|rand|rawurlencode|basename|le
venshtein|doubleval|sizeof|base64_encode|strlen|flo
or|crypt|strrpos|filter_input|abs|bin2hex|bindec|has
h|intval|max|decbin|strpos|crc32|ord|md5|count|sh
a1|min|pathinfo|floatval|round|hexdec)s*()[^;]*$.
*](https://image.slidesharecdn.com/2-150301070554-conversion-gate02/85/2-1-Web-application-Security-Trends-Omar-Ganiev-25-320.jpg)