The document outlines seven golden rules for data leakage prevention:
1. Accept that there is a risk of data breaches.
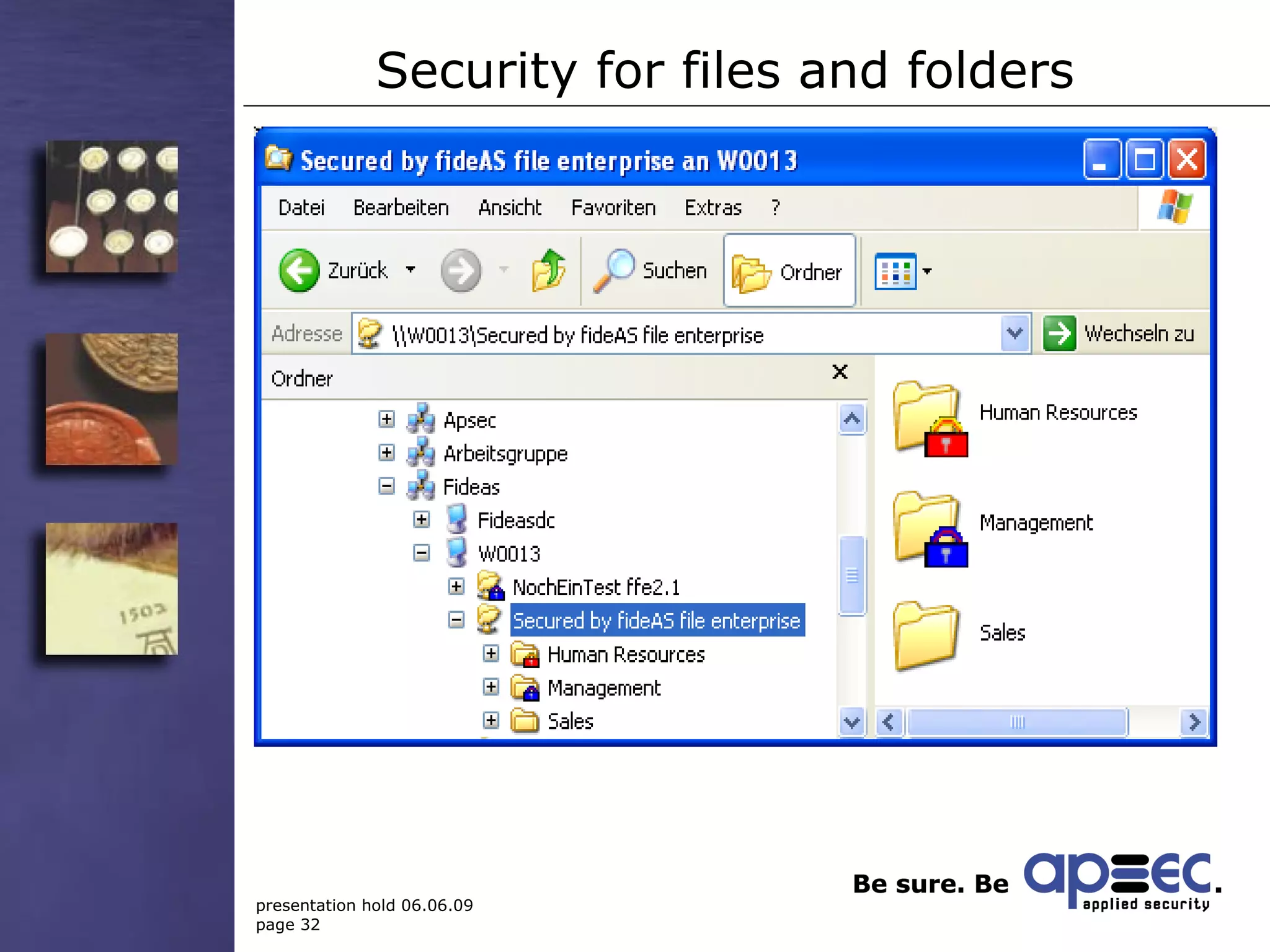
2. Provide endpoint security by identifying sensitive data and protecting it at its origin.
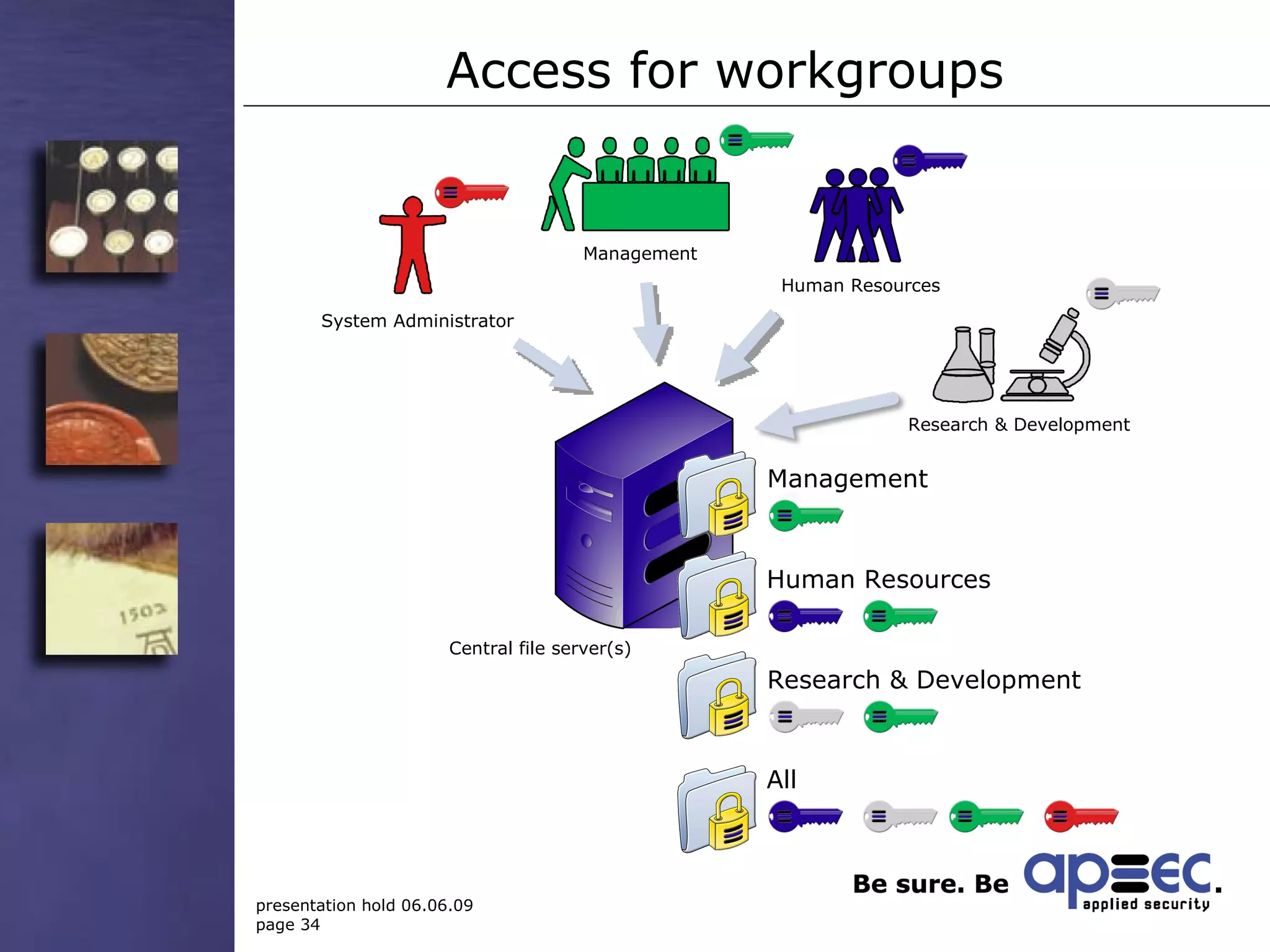
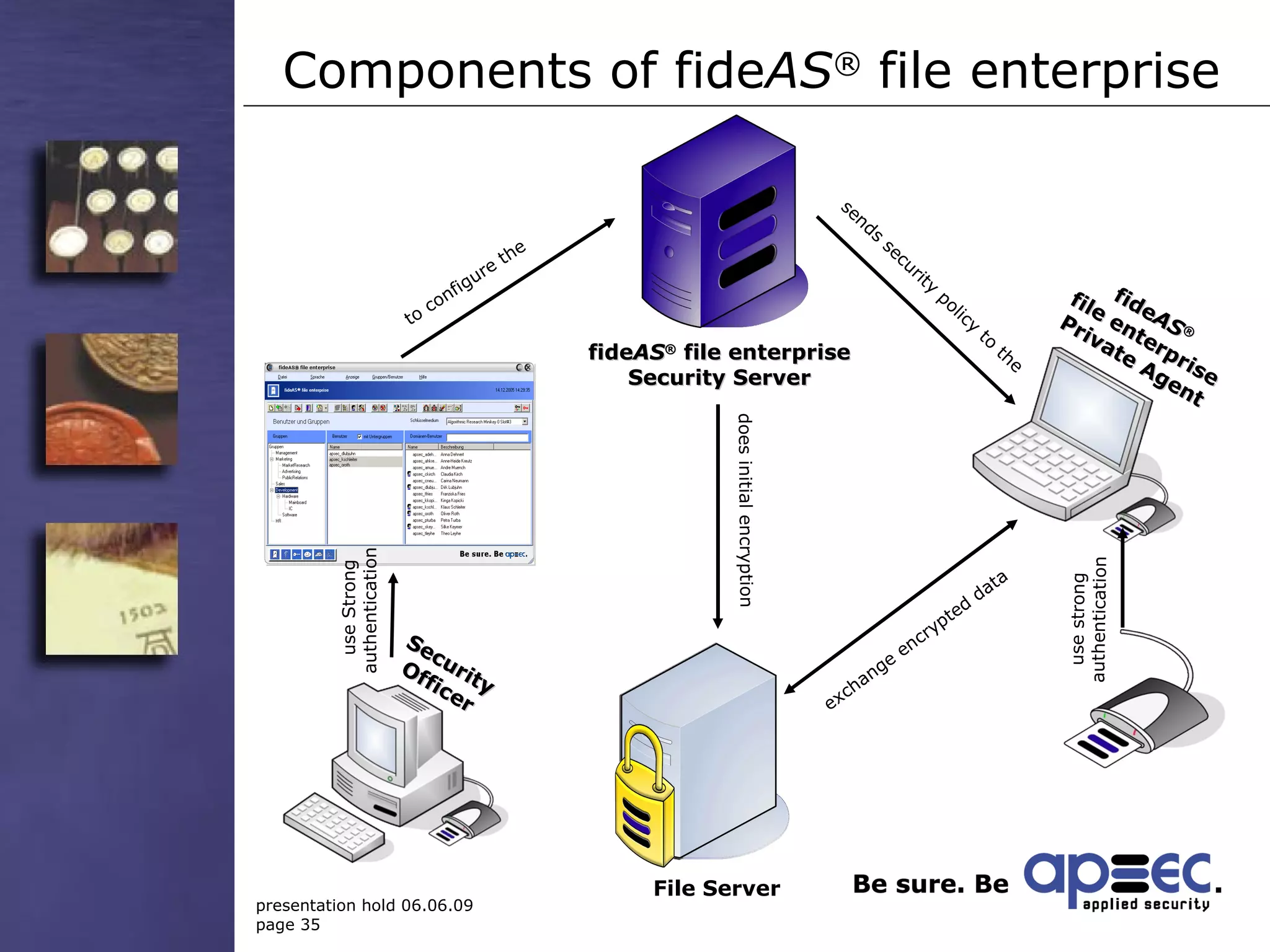
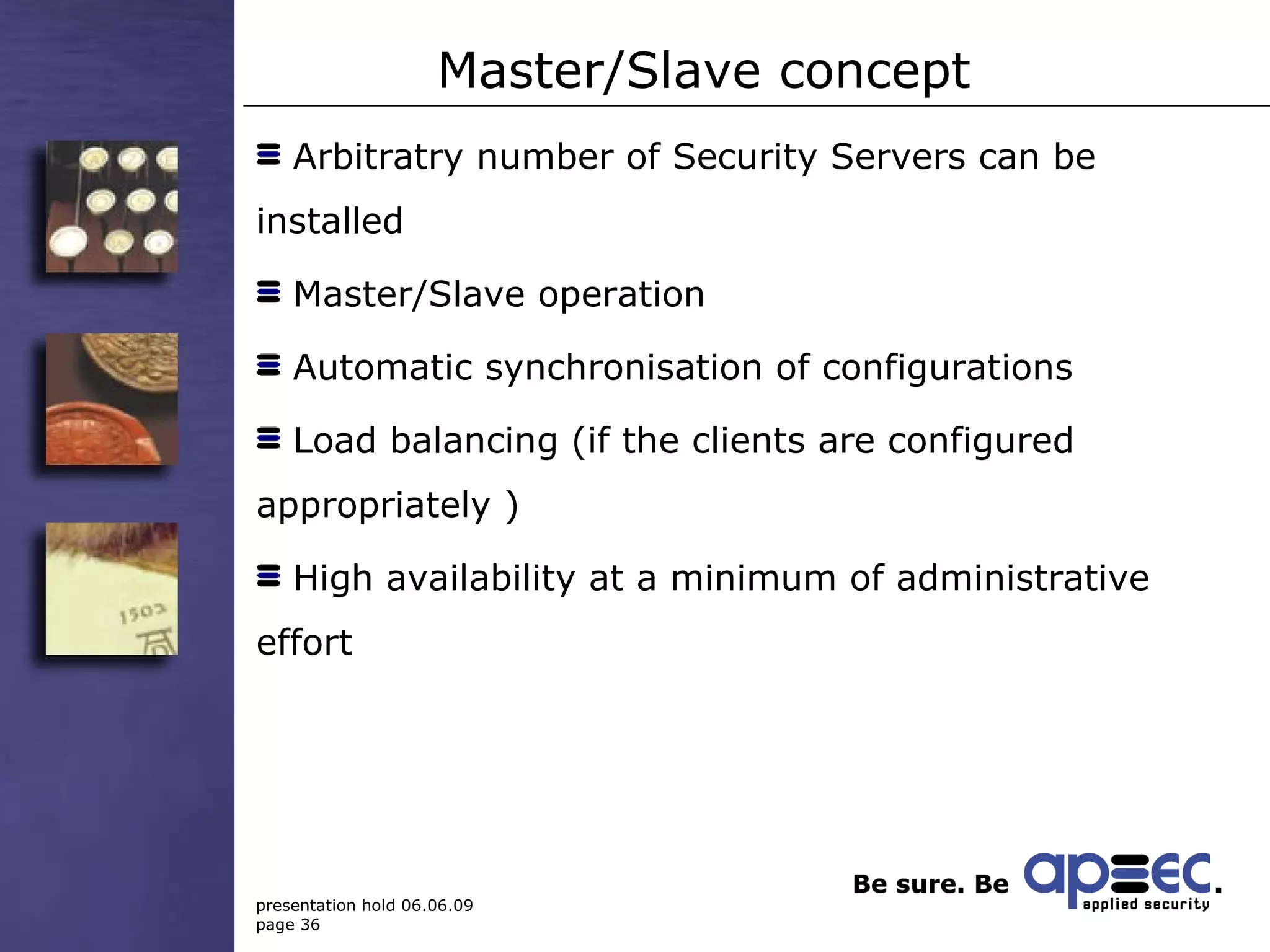
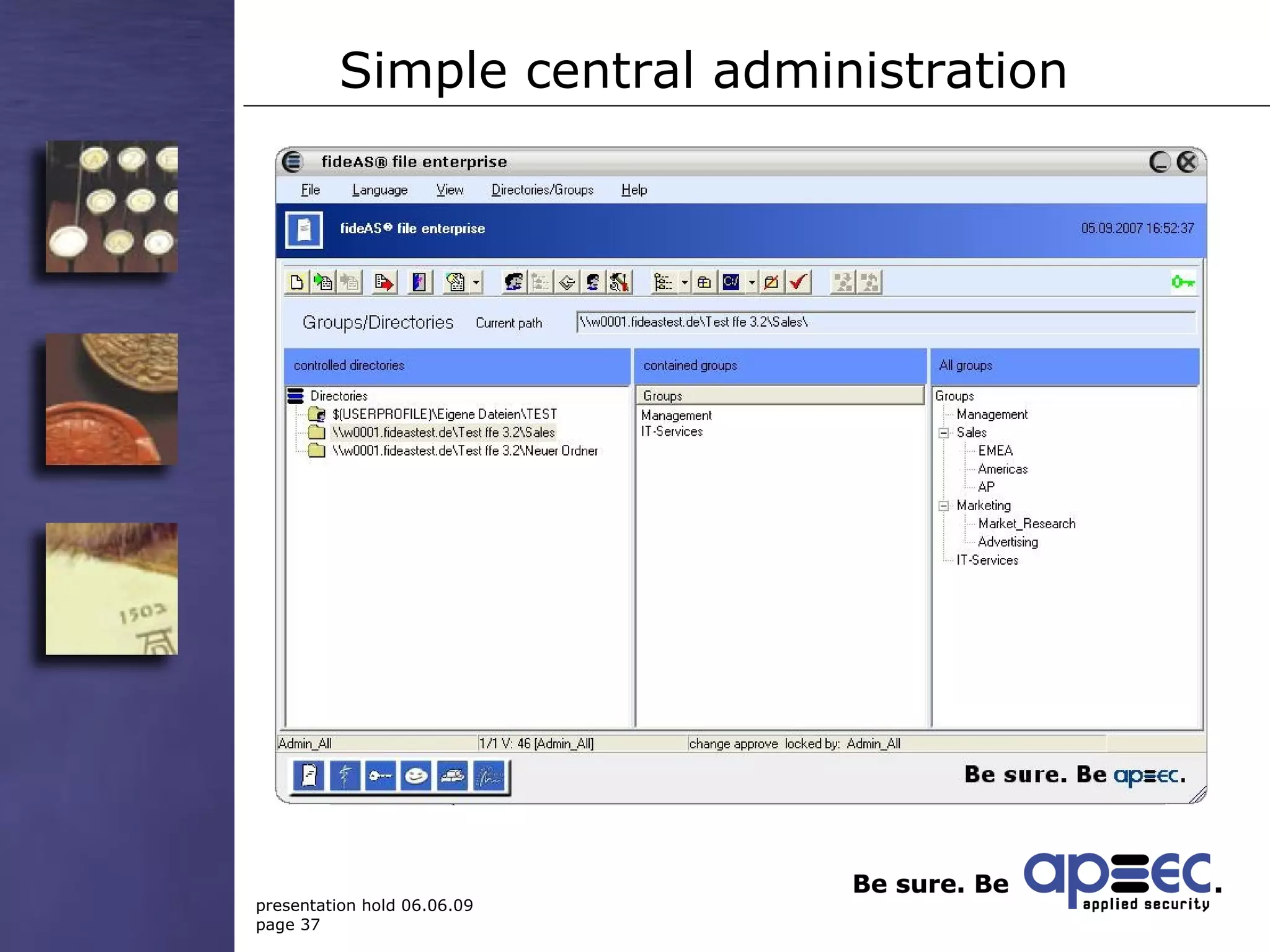
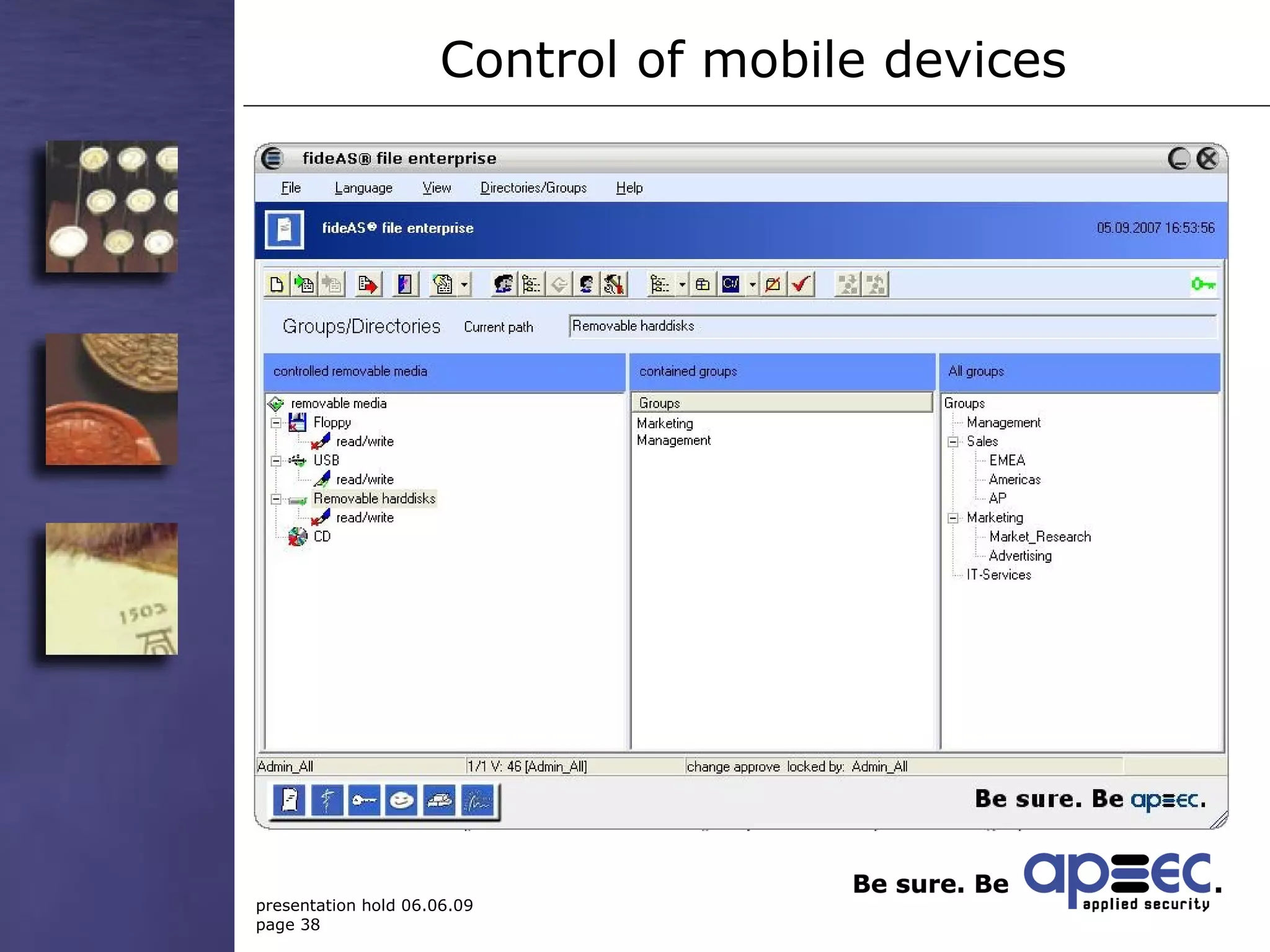
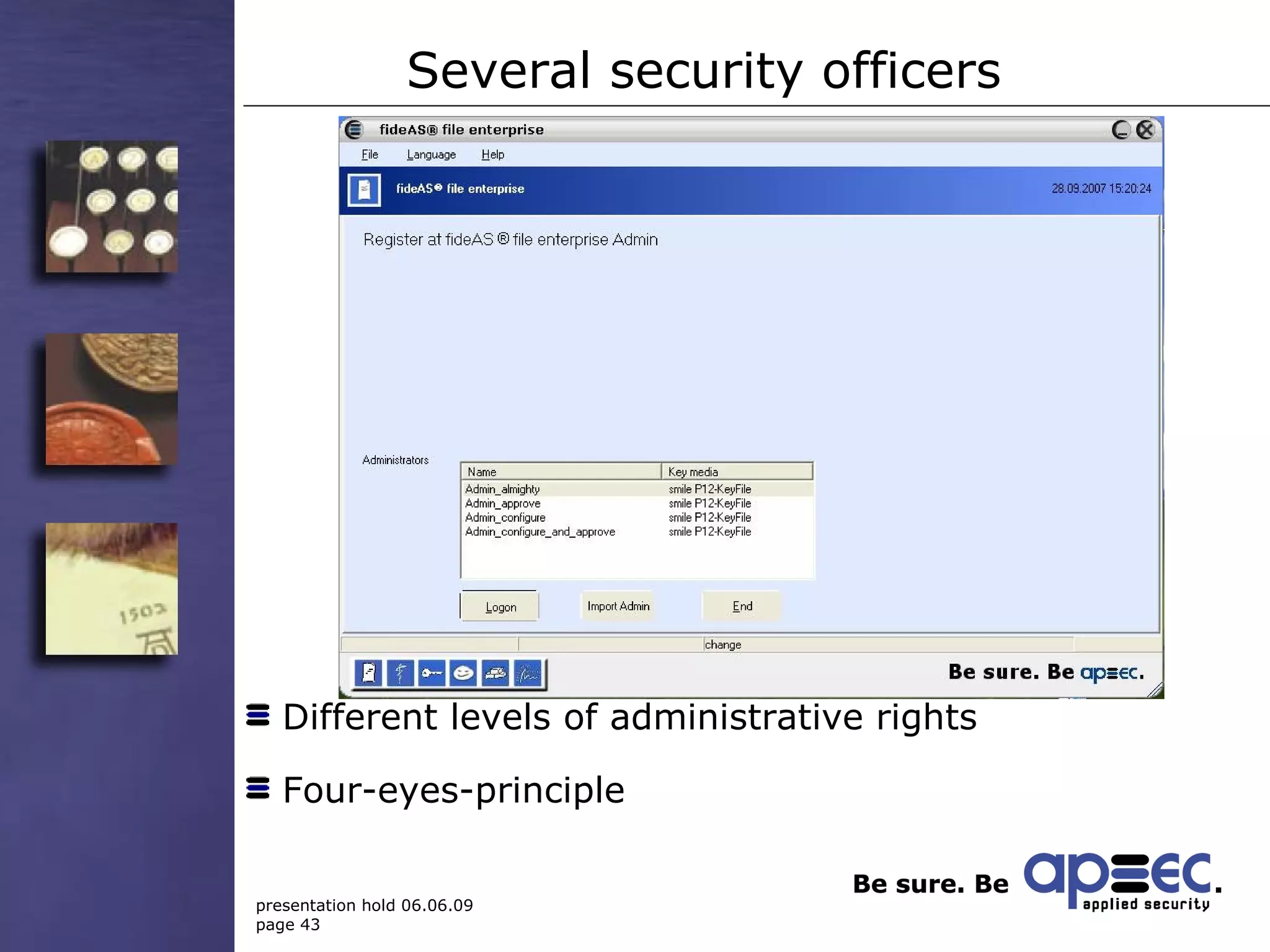
3. Take security into your own hands through centralized policy management and access controls.
4. Make security easy to reduce human errors through invisible encryption and easy administration.
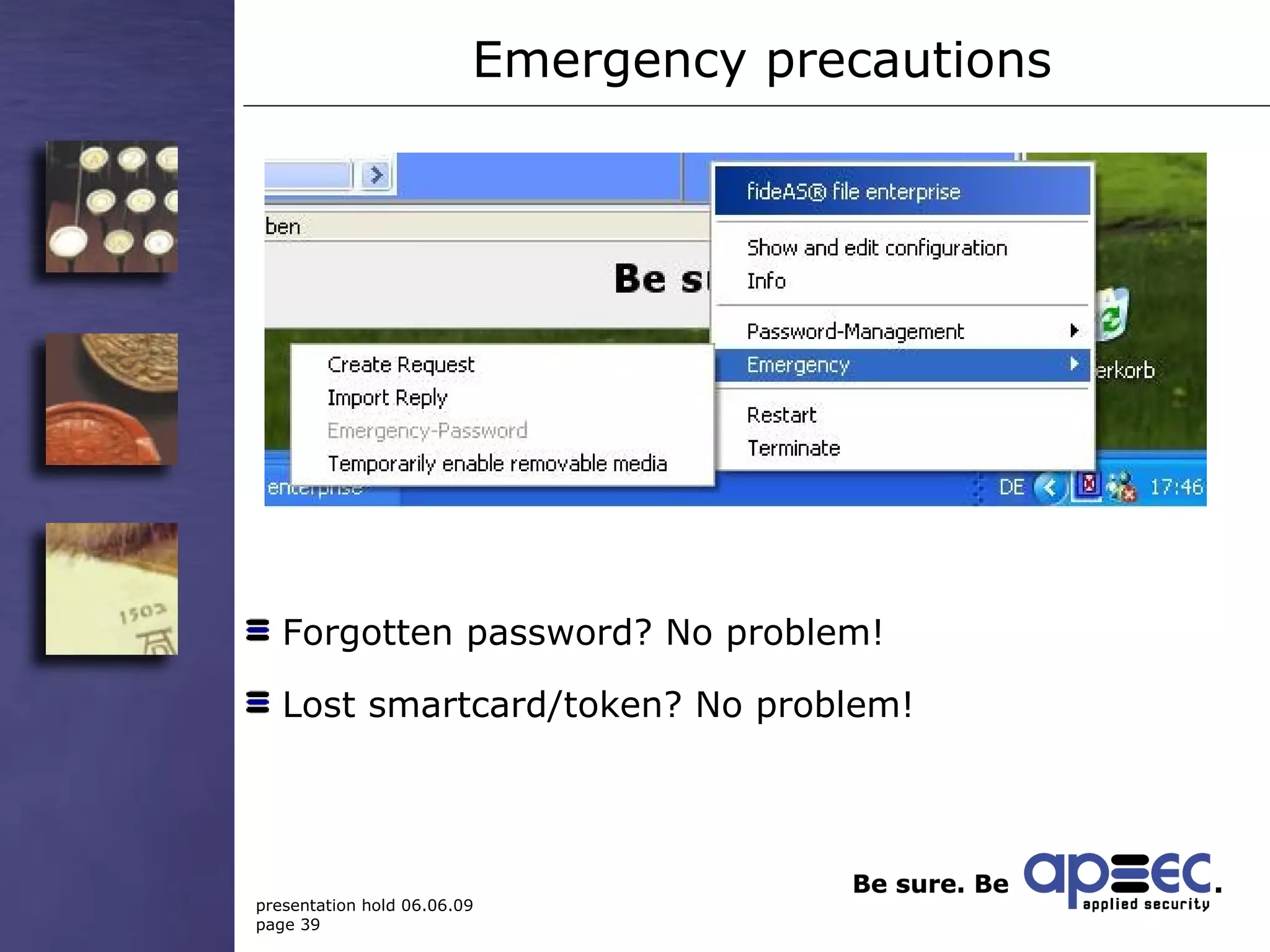
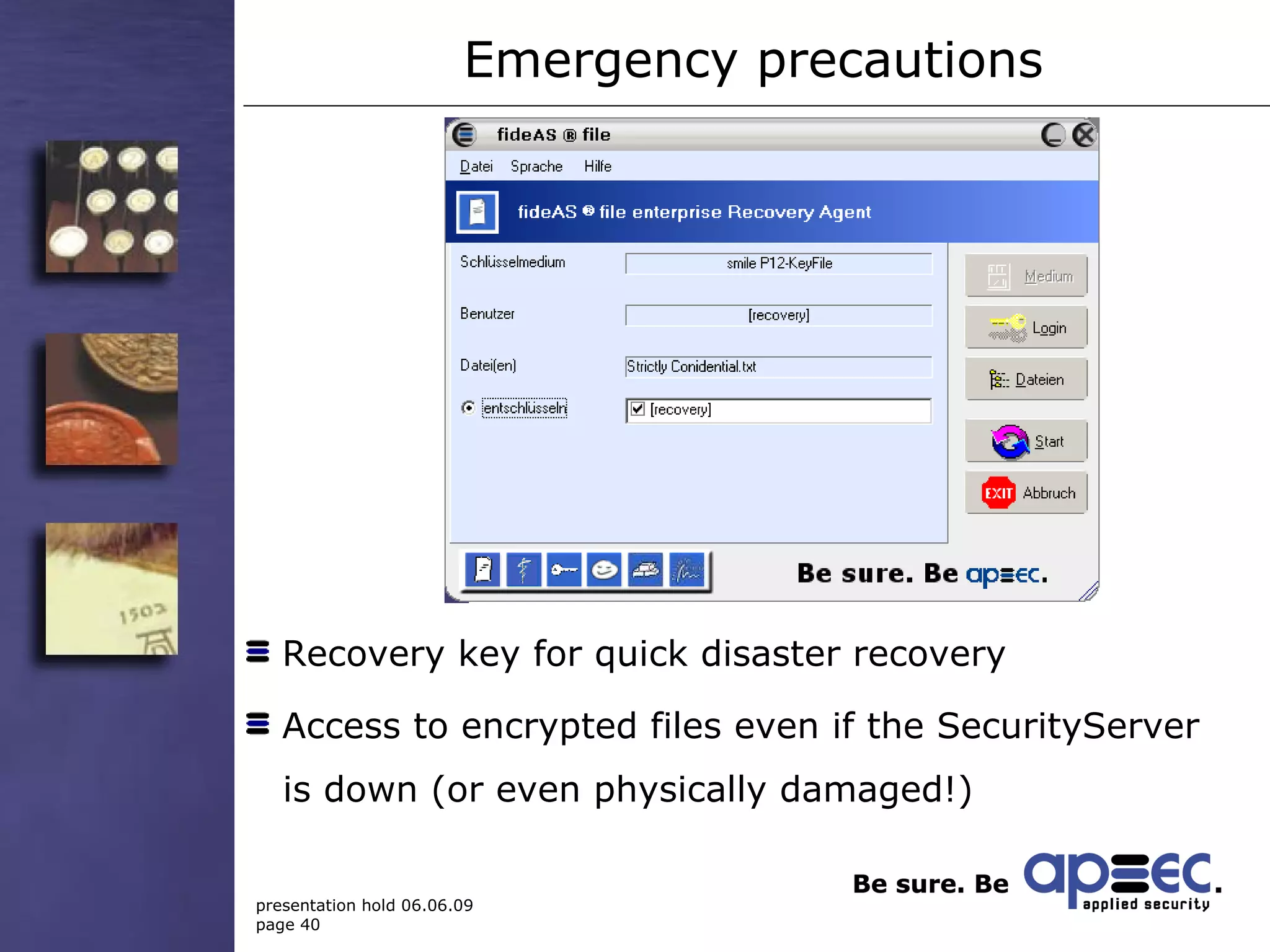
5. Have emergency precautions like encryption key recovery to ensure data availability.
6. Prioritize security using the 80/20 rule to find an acceptable risk level.
7. Understand that security costs money but it is worth it to prevent data loss.





























![Thank you for your attention! Your contact: Andreas Schuster [email_address] Business Development Manager M.E. www.applied-security.com](https://image.slidesharecdn.com/apsec7goldenrulesdlplinkedin-124426924528-phpapp02/75/apsec-7-Golden-Rules-Data-Leakage-Prevention-DLP-56-2048.jpg)