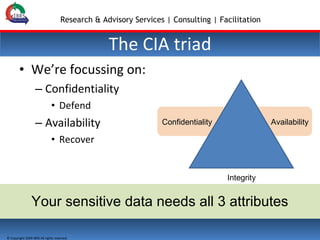
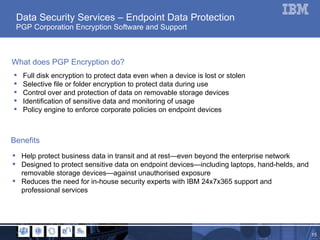
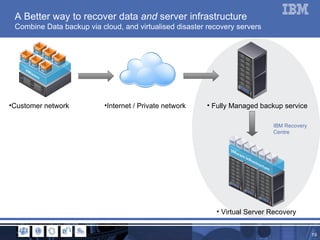
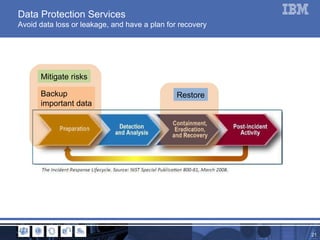
The document outlines a webinar focused on data protection for businesses, discussing current issues in information security and the significance of data confidentiality, integrity, and availability. It highlights the challenges of data loss prevention, mobility of workers, and cloud adoption, emphasizing the need for effective strategies and tools like encryption and managed backup services. Additionally, it presents case studies illustrating how companies successfully implemented data protection solutions to enhance security and operational efficiency.