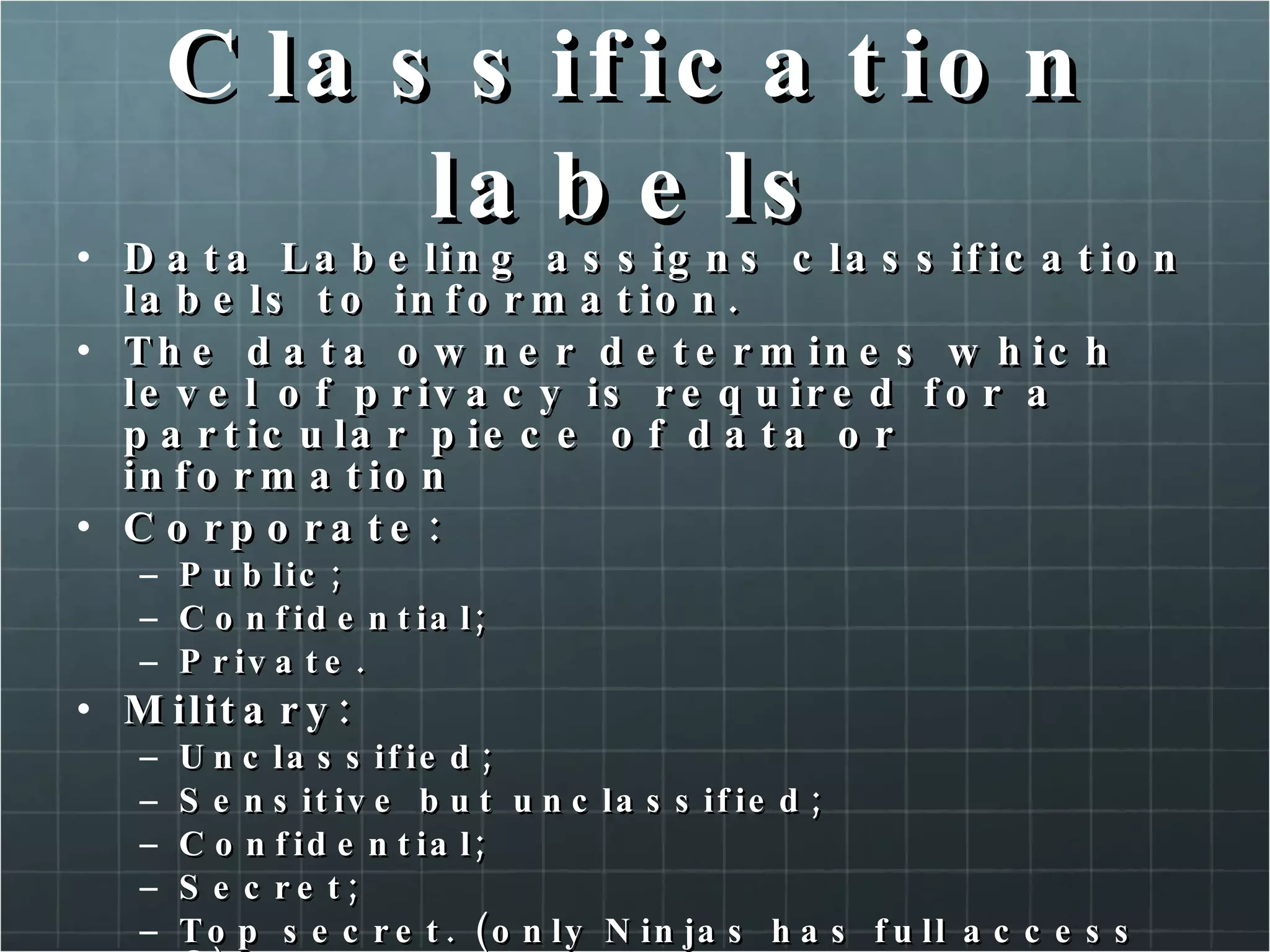
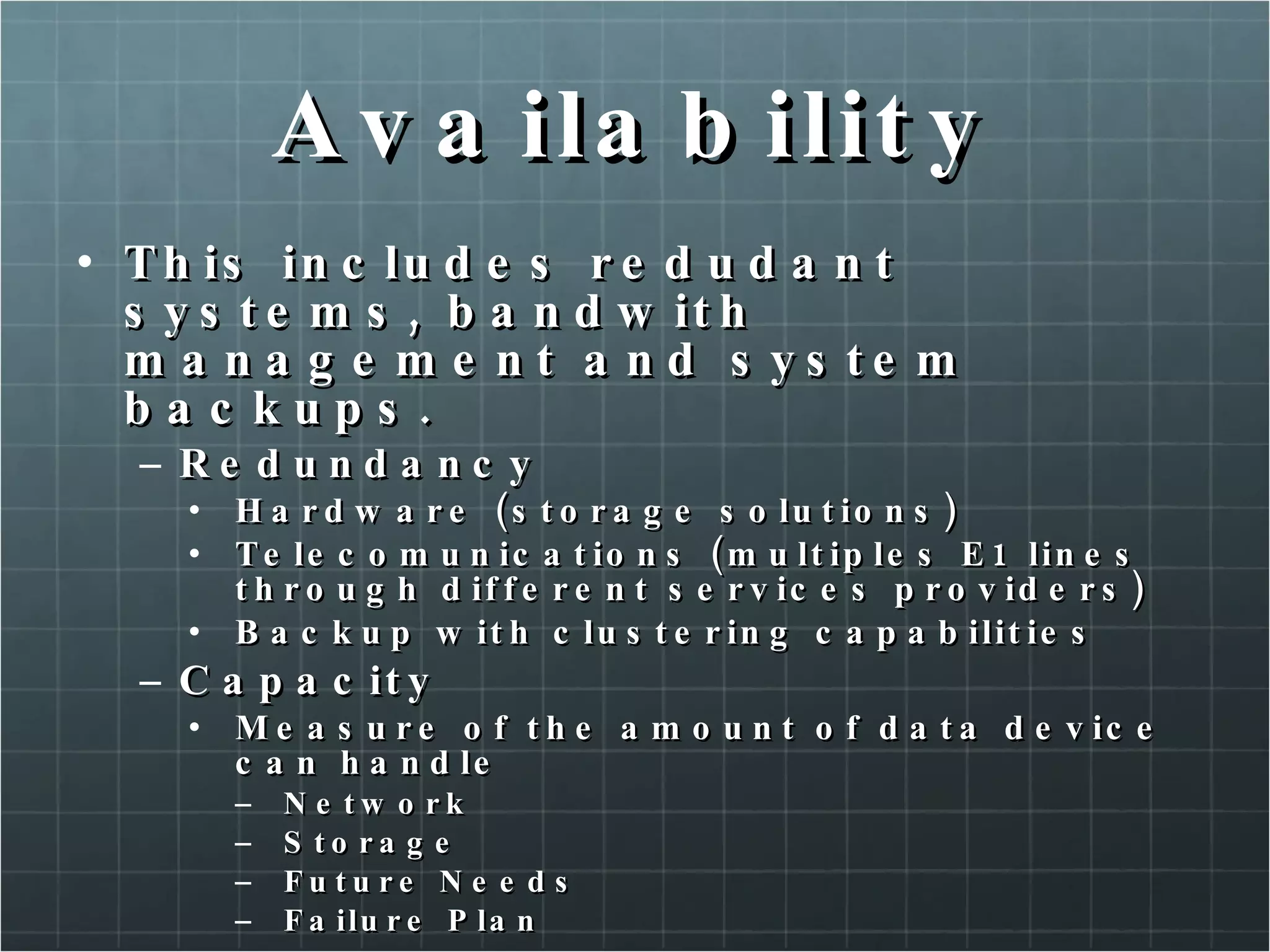
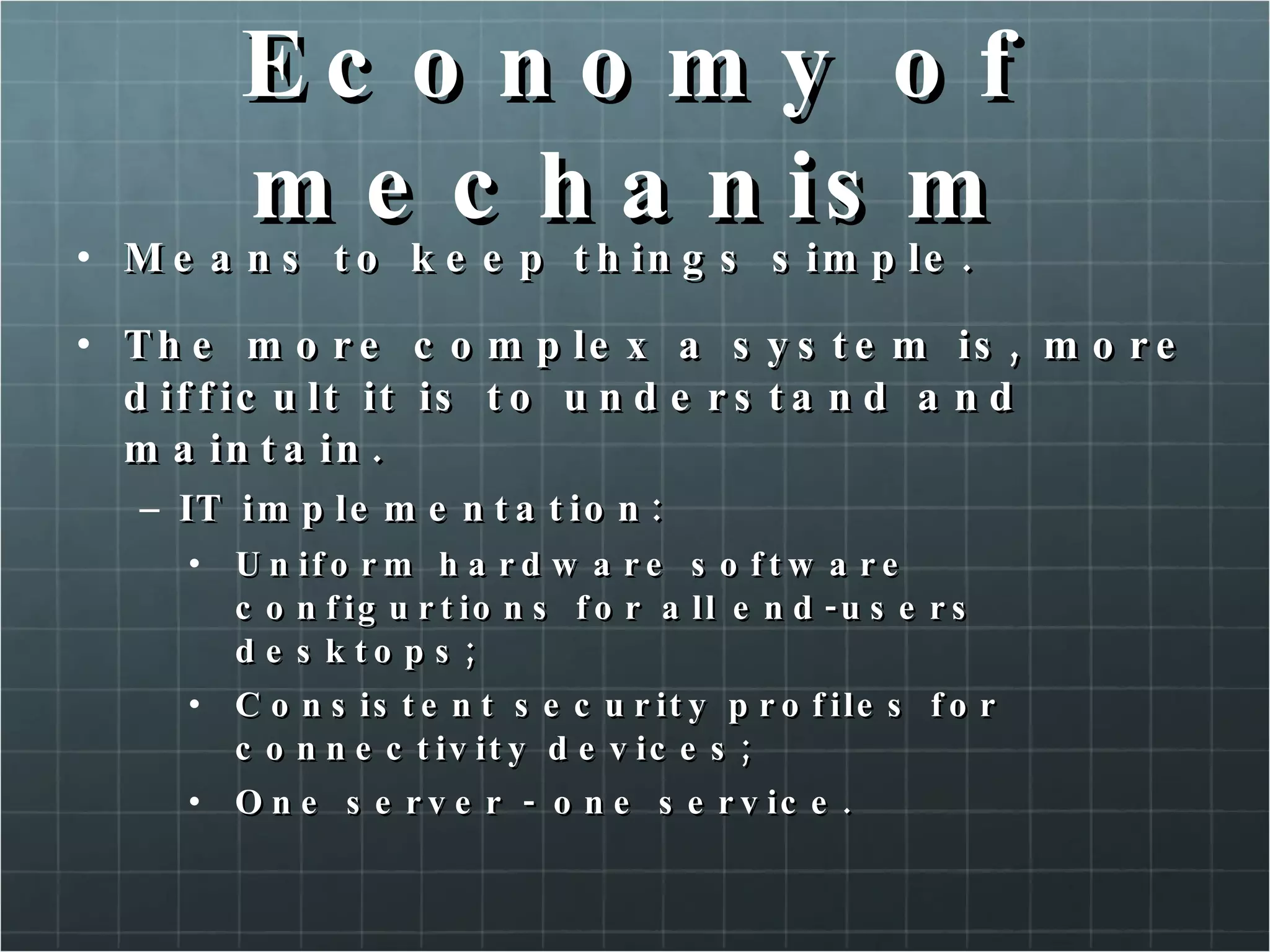
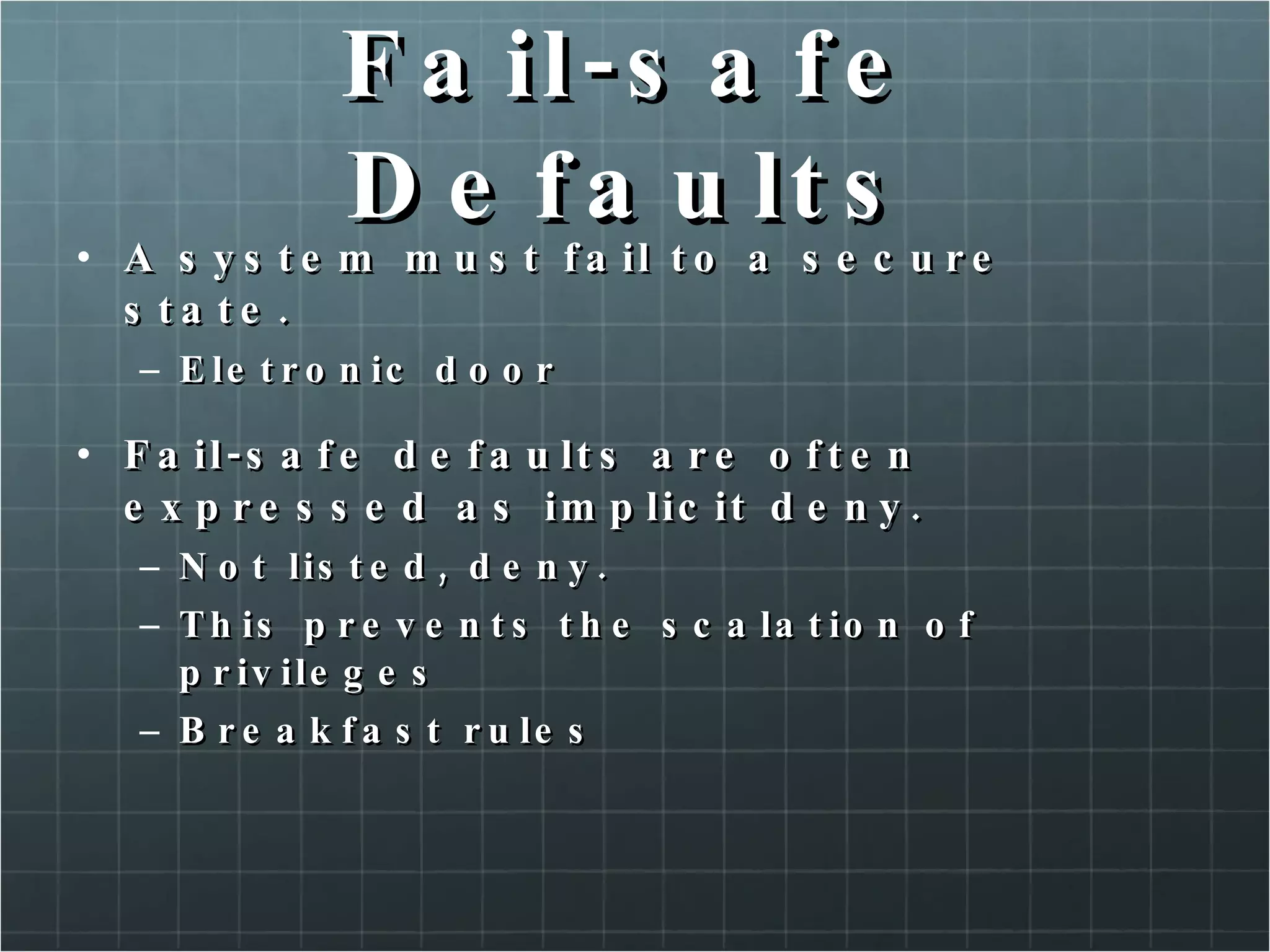
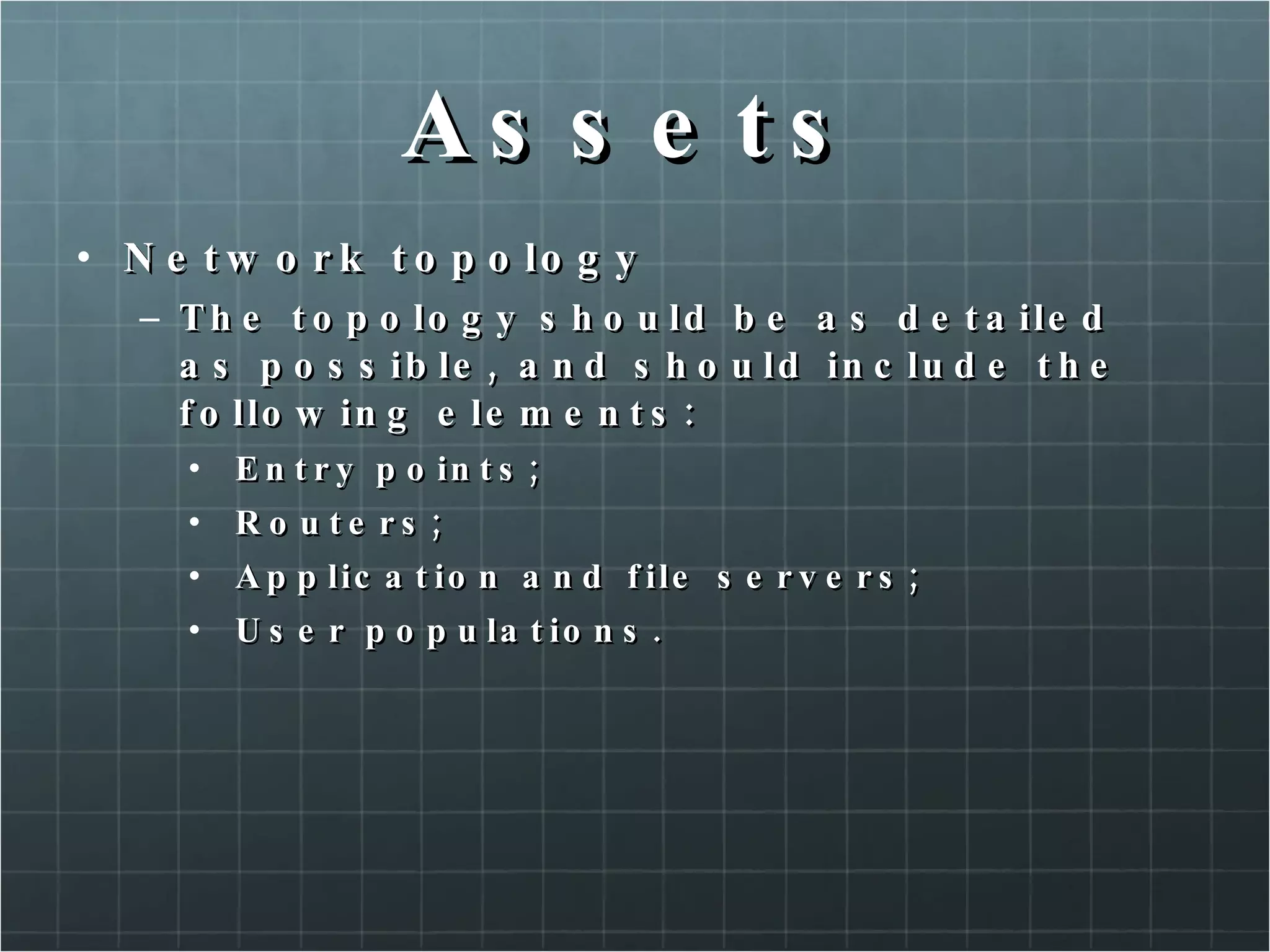
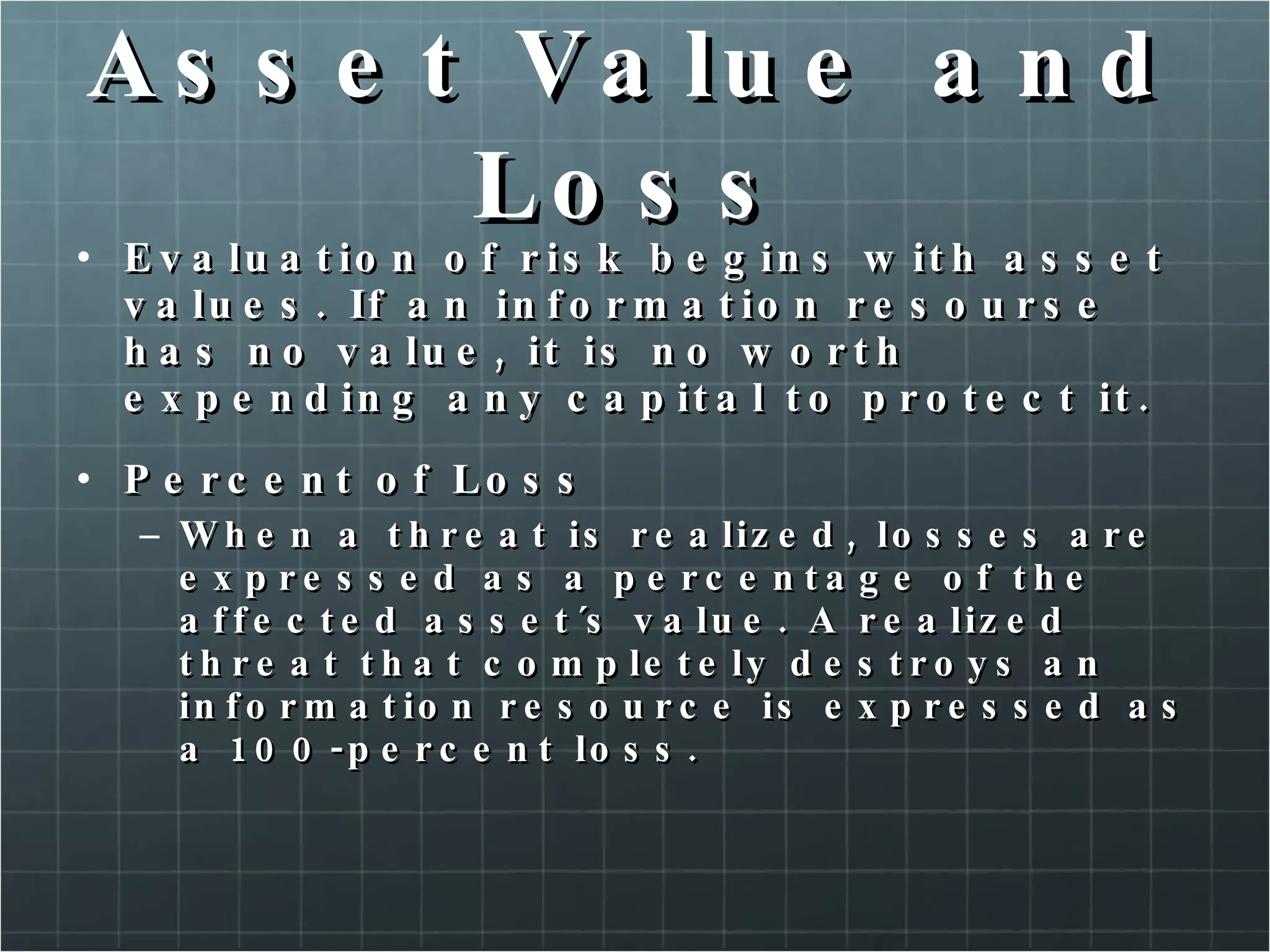
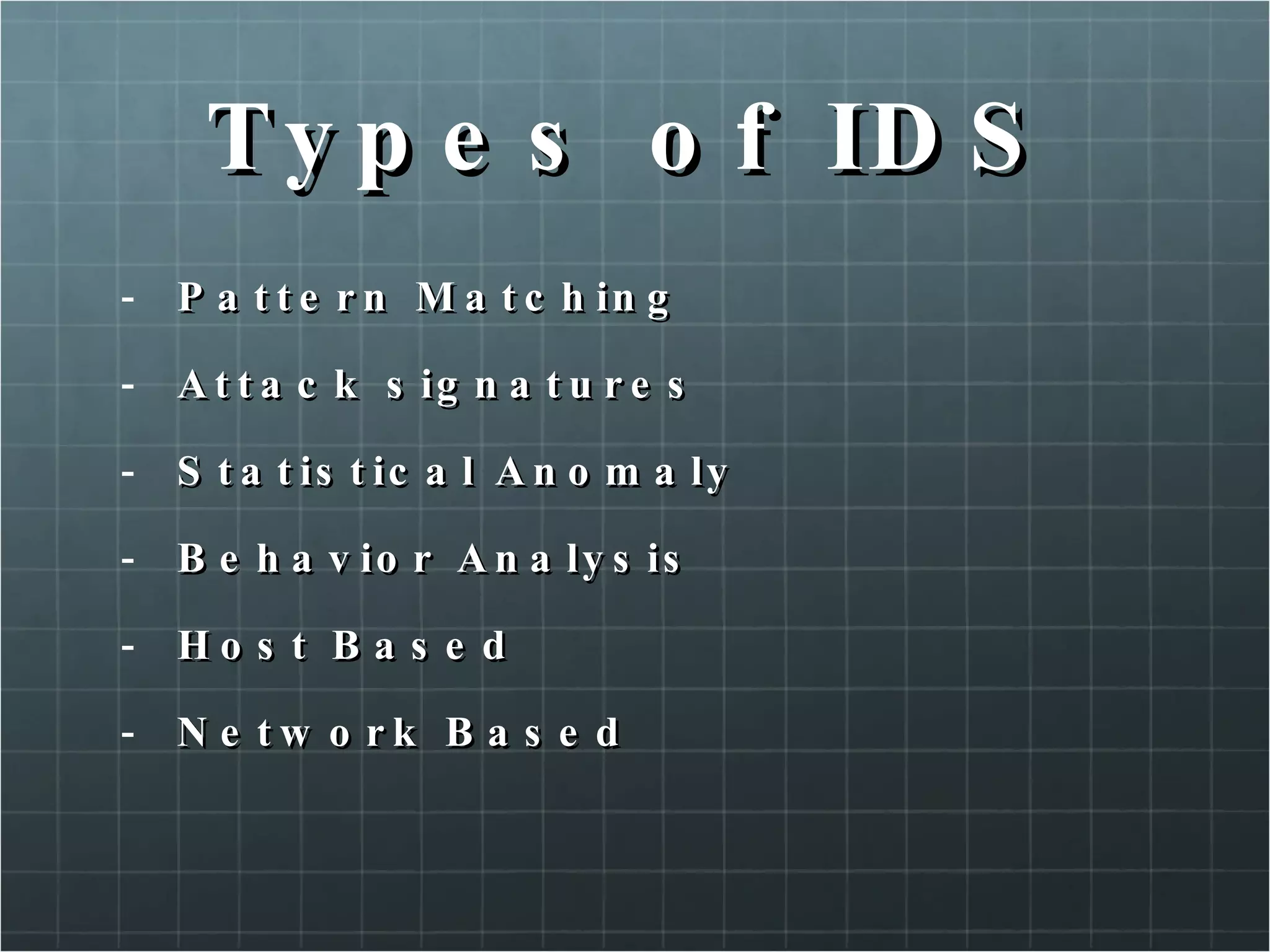
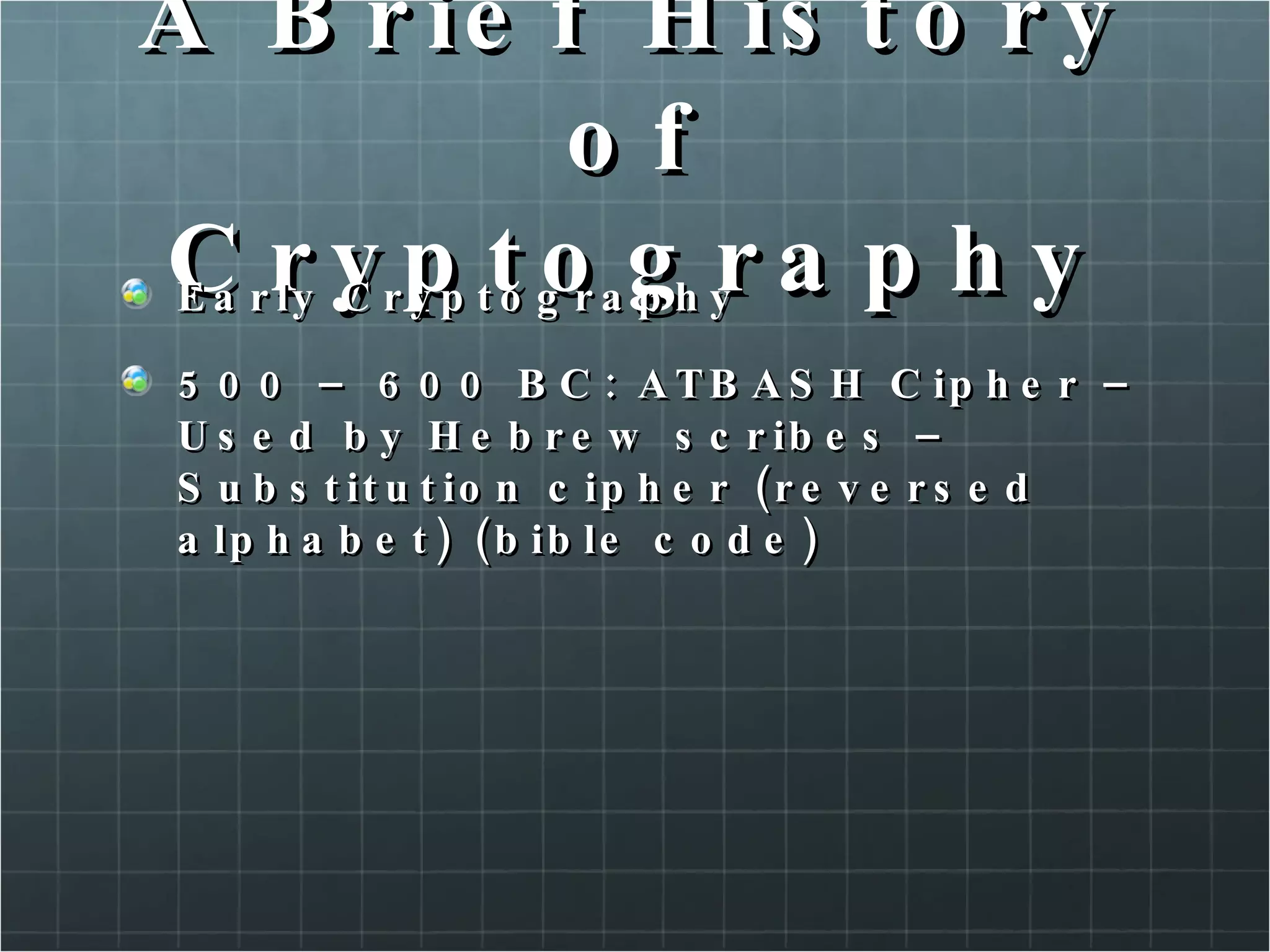
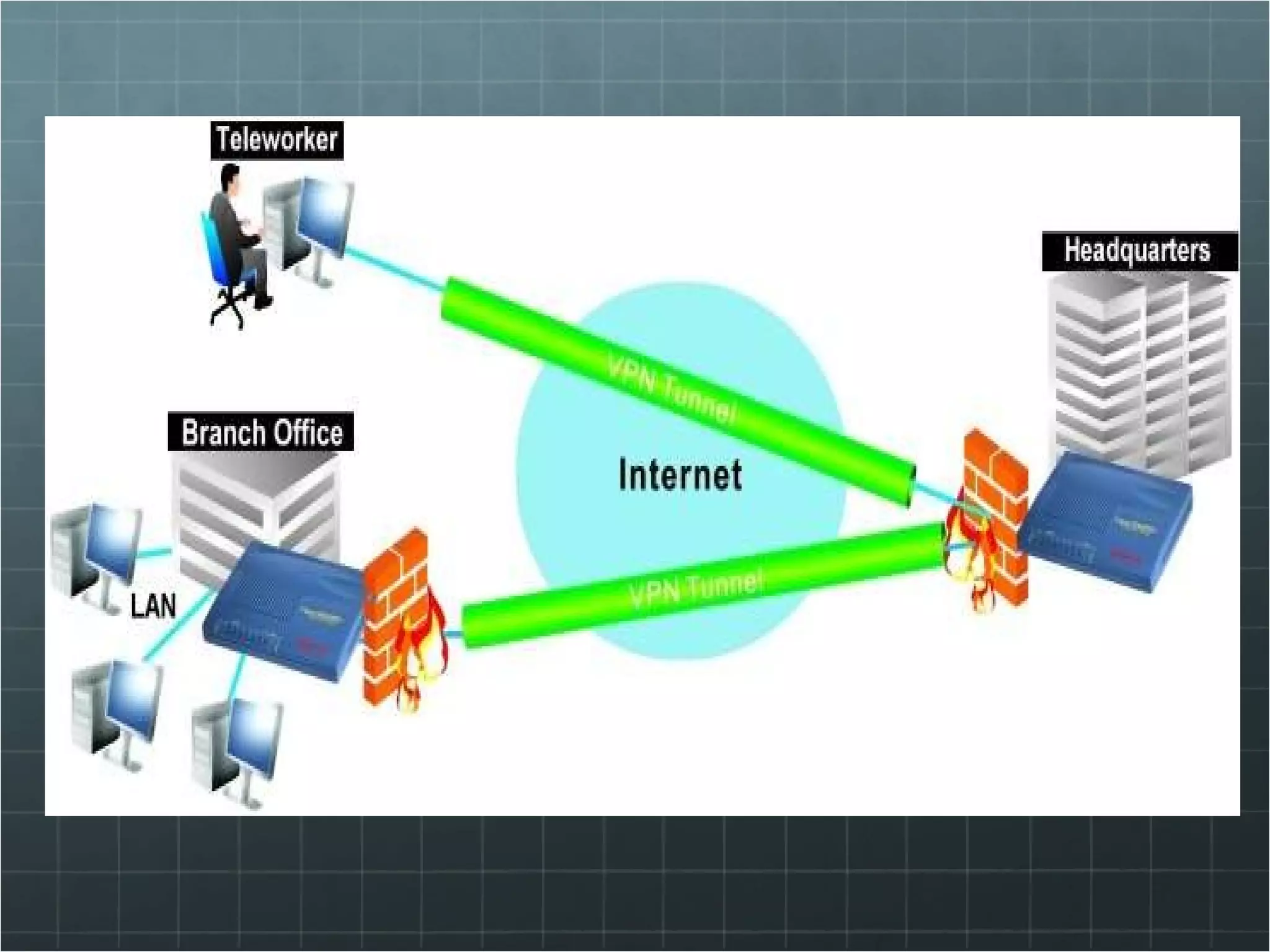
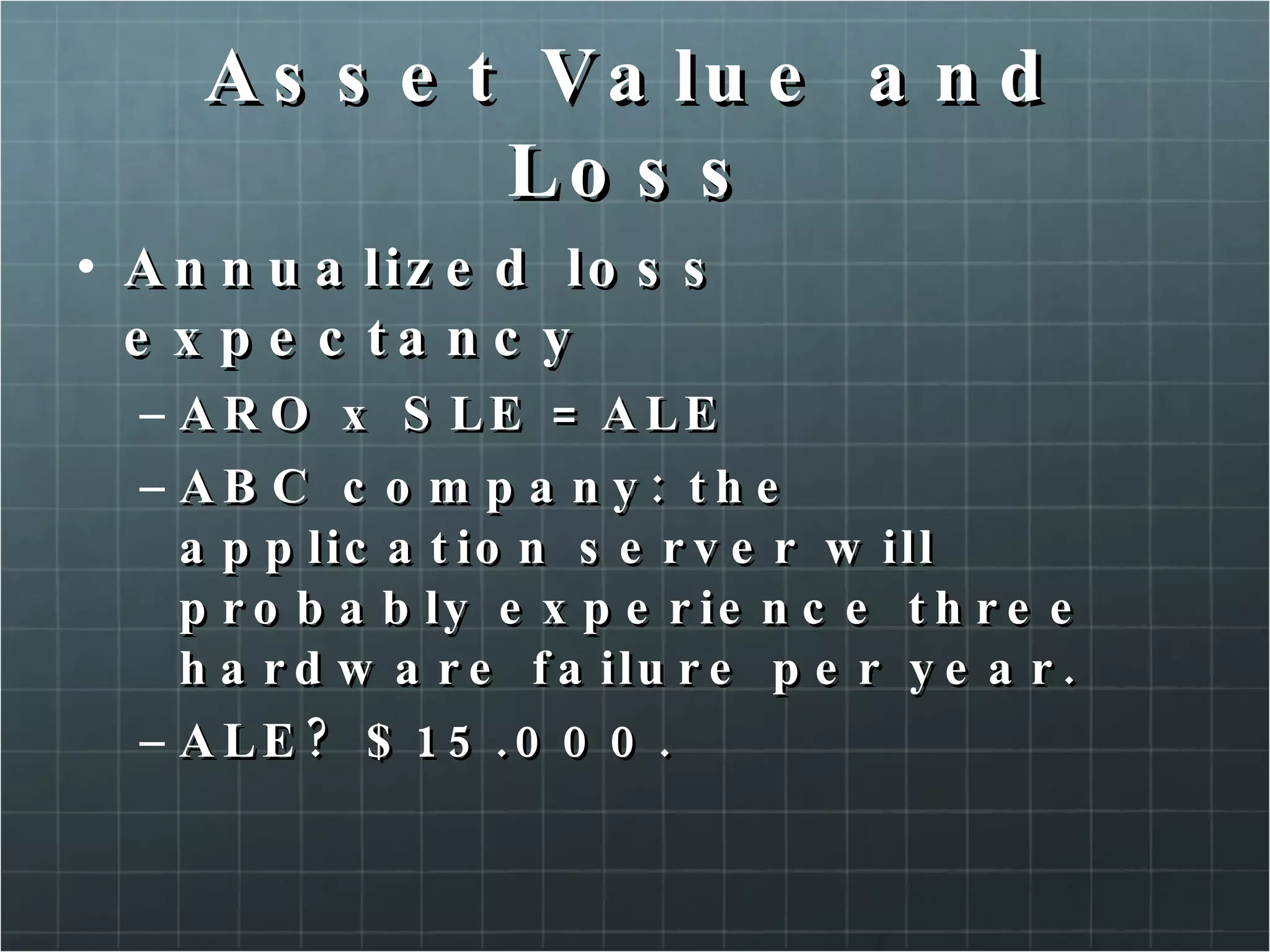The document provides an overview of information security concepts including confidentiality, integrity, availability, encryption, access control, classification labels, risk management, security policies, business continuity planning, operational security, intrusions and attacks, and cryptography. Key terms like encryption algorithms, internet key exchange, and types of intrusion detection systems are defined. A brief history of cryptography from ancient times to modern ciphers is also presented.