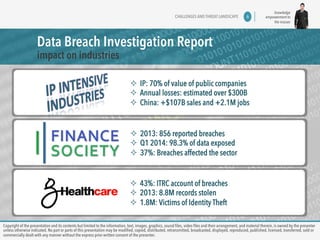
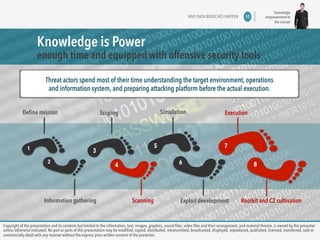
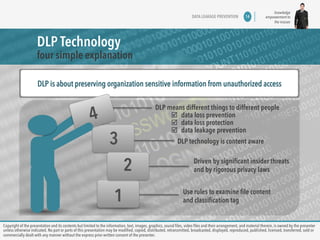
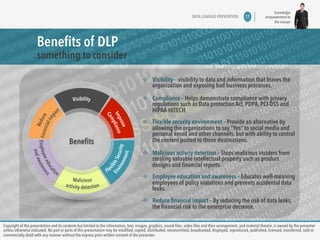
The document discusses copyright information and consent requirements for a presentation on data leakage prevention. It notes that copyright of the presentation contents is owned by the presenter unless otherwise indicated. No parts of the presentation can be modified, copied, distributed, or commercially shared without the express prior written consent of the presenter. The presentation will cover challenges in the threat landscape, reasons why data breaches happen, and approaches to data leakage prevention.