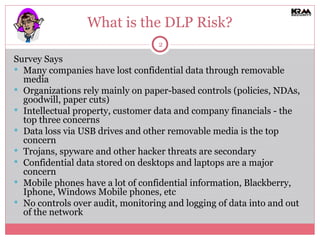
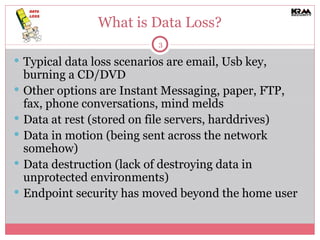
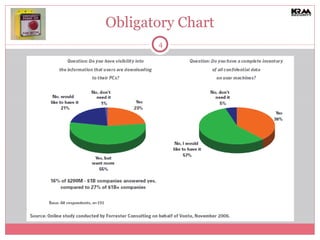
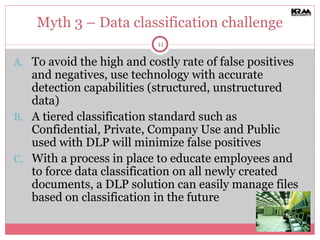
The document discusses the importance of Data Loss Prevention (DLP) for organizations, specifically addressing common myths that small and medium-sized businesses (SMBs) have about DLP solutions. It emphasizes that DLP is not only for large companies and highlights various tactical, less expensive solutions available for SMBs. Additionally, it stresses the need for classification, employee education, and robust technology controls to mitigate data loss risks effectively.








![Gary Bahadur CEO KRAA Security www.kraasecurity.com [email_address] Blog.kraasecurity.com Consulting Services | Managed Security Services](https://image.slidesharecdn.com/5mythsaboutdatalossprevention-100404123116-phpapp01/85/5-Myths-About-Data-Loss-Prevention-17-320.jpg)