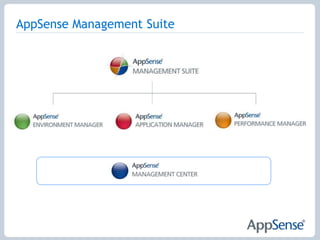
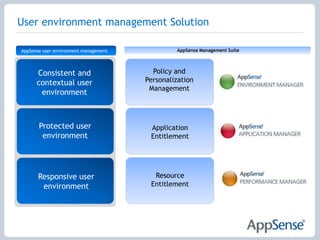
The document discusses the features of AppSense Management Suite, which allows for centralized management and personalization of user environments across different delivery mechanisms. It provides capabilities such as personalization management, application and resource entitlement controls, and centralized management of user environments. The suite aims to improve the user experience, reduce support costs, and ensure compliance. It uses features such as personalization streaming, rules and actions, self-healing, digital signatures, and configuration templates to achieve these goals.