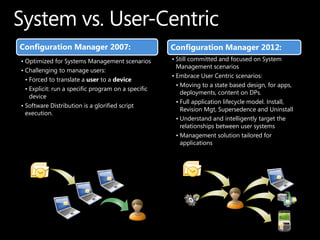
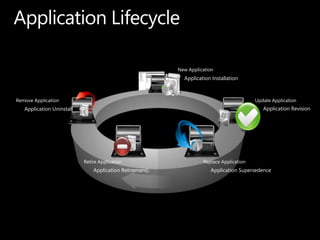
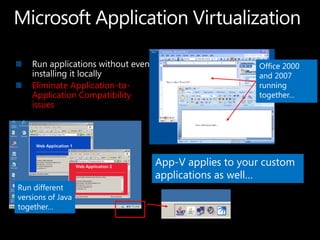
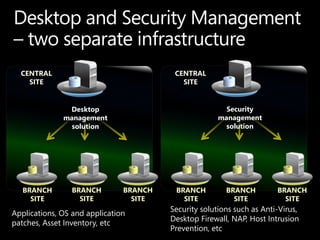
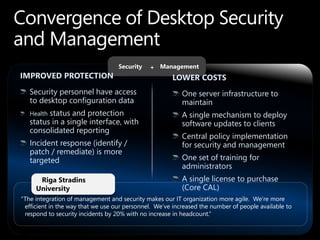
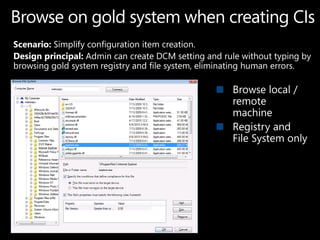
SCCM 2012 provides expanded management capabilities for both systems and users. It focuses on application lifecycle management, including installation, revision, supersedence, and uninstallation of applications. It also aims to intelligently target relationships between users and systems. SCCM 2012 improves upon SCCM 2007 by embracing user-centric scenarios and providing a state-based design for deploying content and applications to devices.