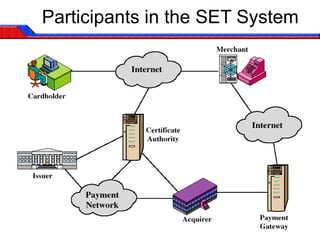
SET was developed by Visa and MasterCard to securely transmit credit and debit card information over the internet. It uses public key encryption and digital certificates to authenticate parties and encrypt transactions for confidentiality. All parties must have digital certificates and information is only shared when necessary to protect privacy. SET supports common transaction types and uses technologies like 3DES, RSA signatures, and SHA-1 hashing to provide security.