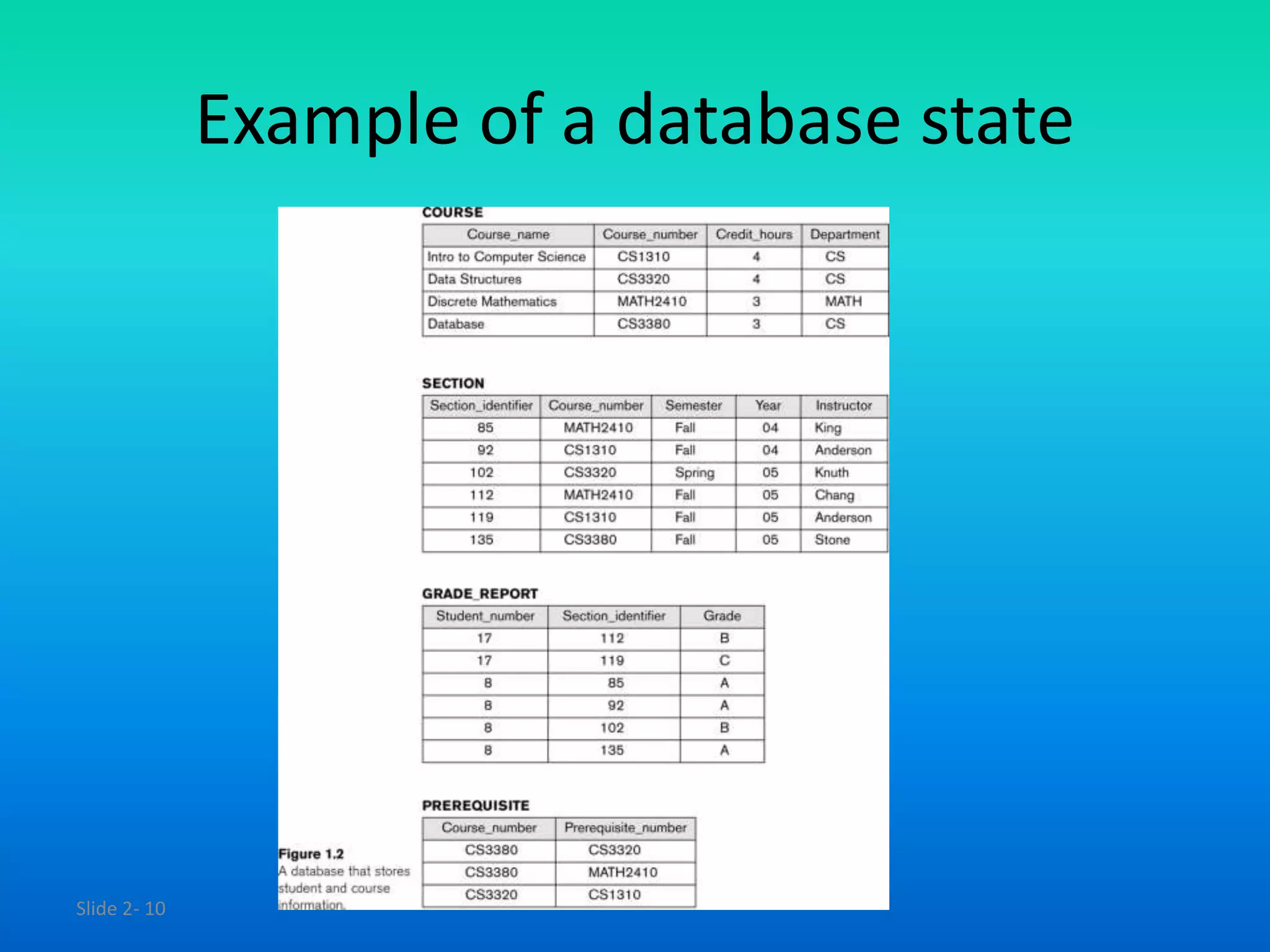
The document discusses data models, schemas, and database states. It defines a data model as a set of concepts that describe a database's structure, operations for manipulating the structure, and constraints. A data model specifies elements, relationships, and restrictions on valid data. A schema defines a database's description, structure, data types, and constraints, while a state refers to the actual data stored at a moment in time. The schema changes infrequently while the state changes with each update.