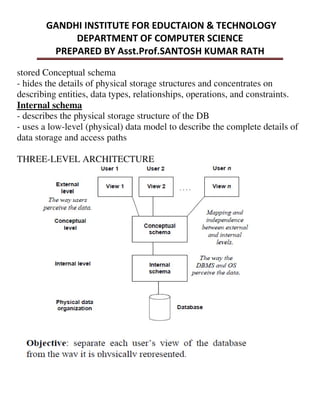
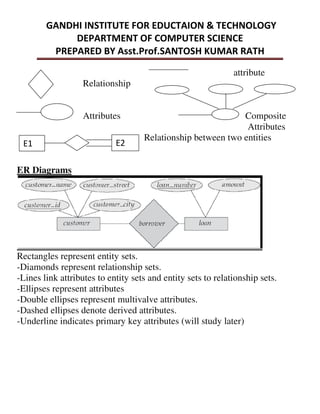
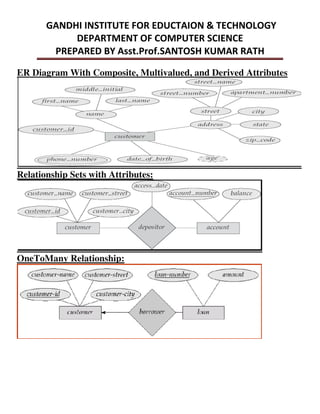
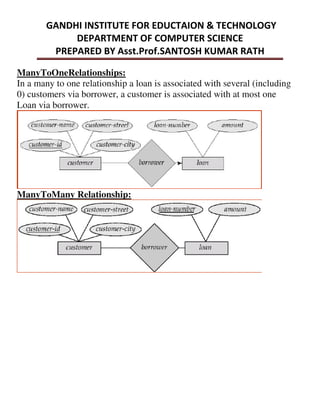
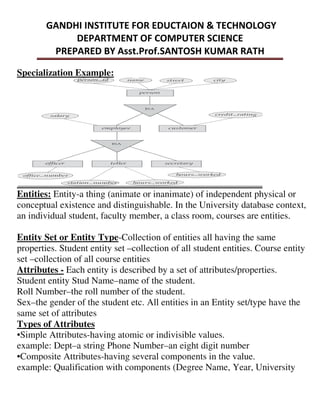
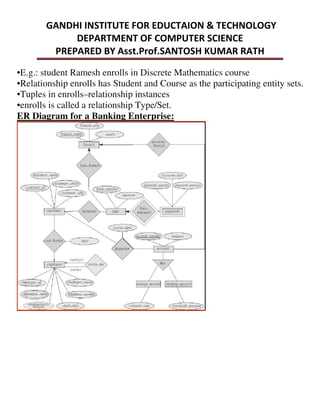
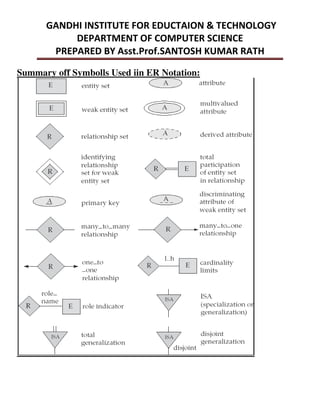
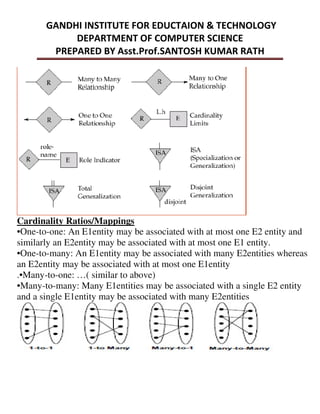
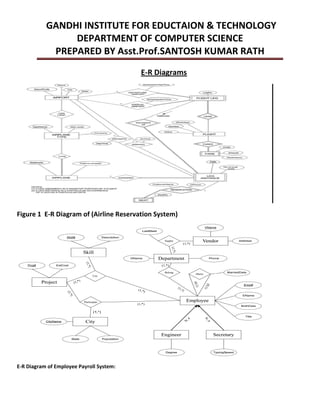
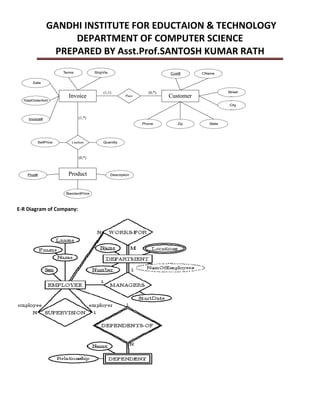
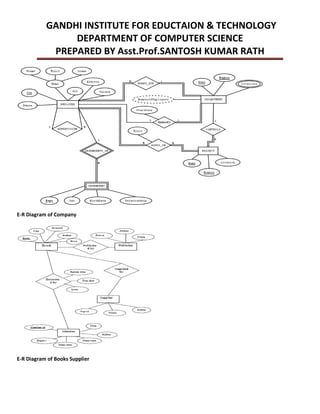
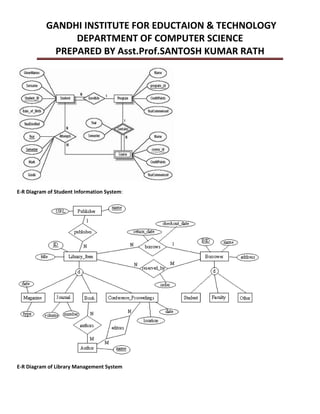
This document provides an overview of database management systems and related concepts. It discusses the three schema architecture including external, conceptual, and internal schemas. It also covers data models, data definition and manipulation languages, database administrators, keys such as primary keys and foreign keys, and integrity constraints including referential integrity, check constraints, and NOT NULL constraints. The goal of these concepts is to provide a structured and standardized way to define, manipulate, and manage database systems and data.