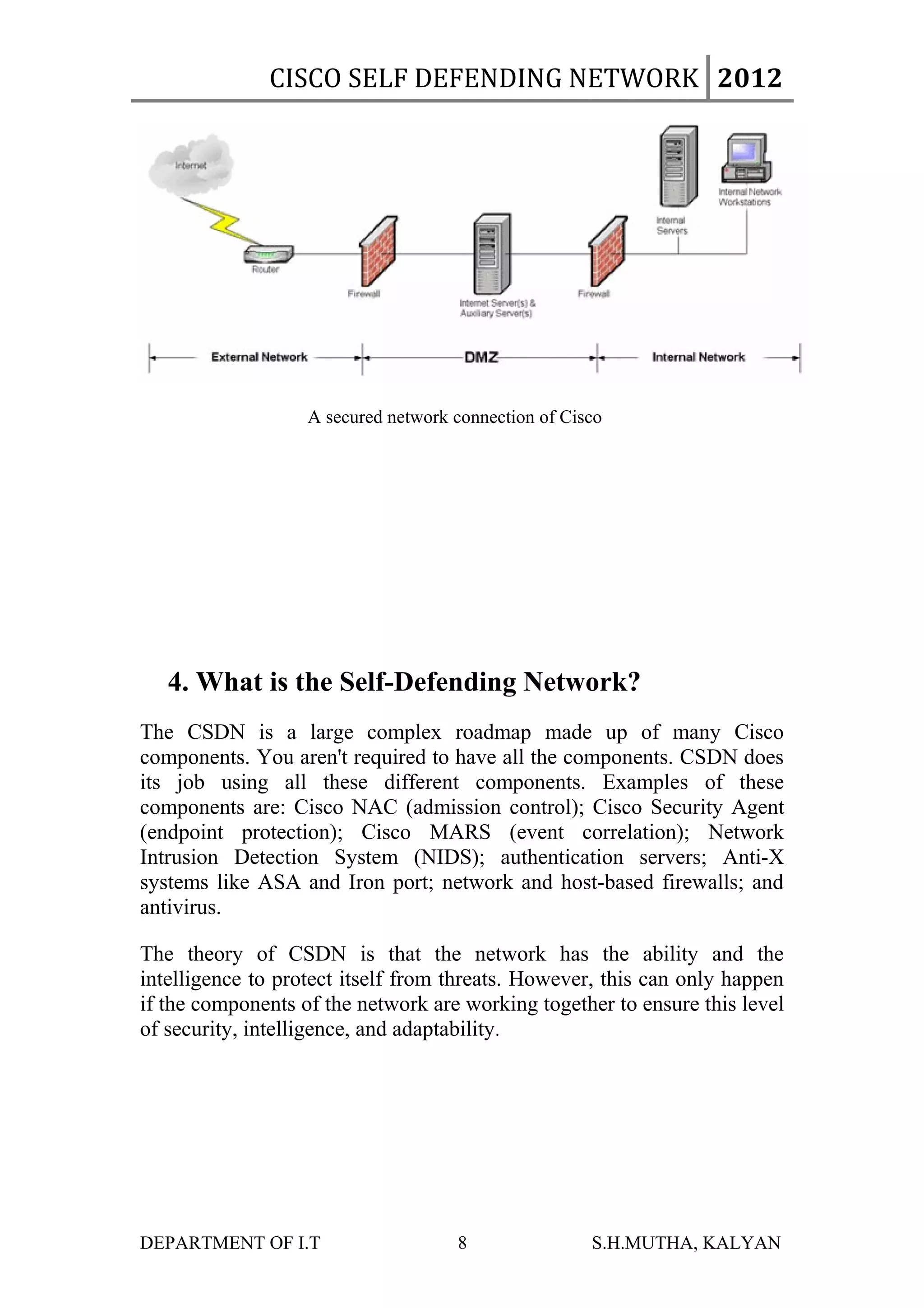
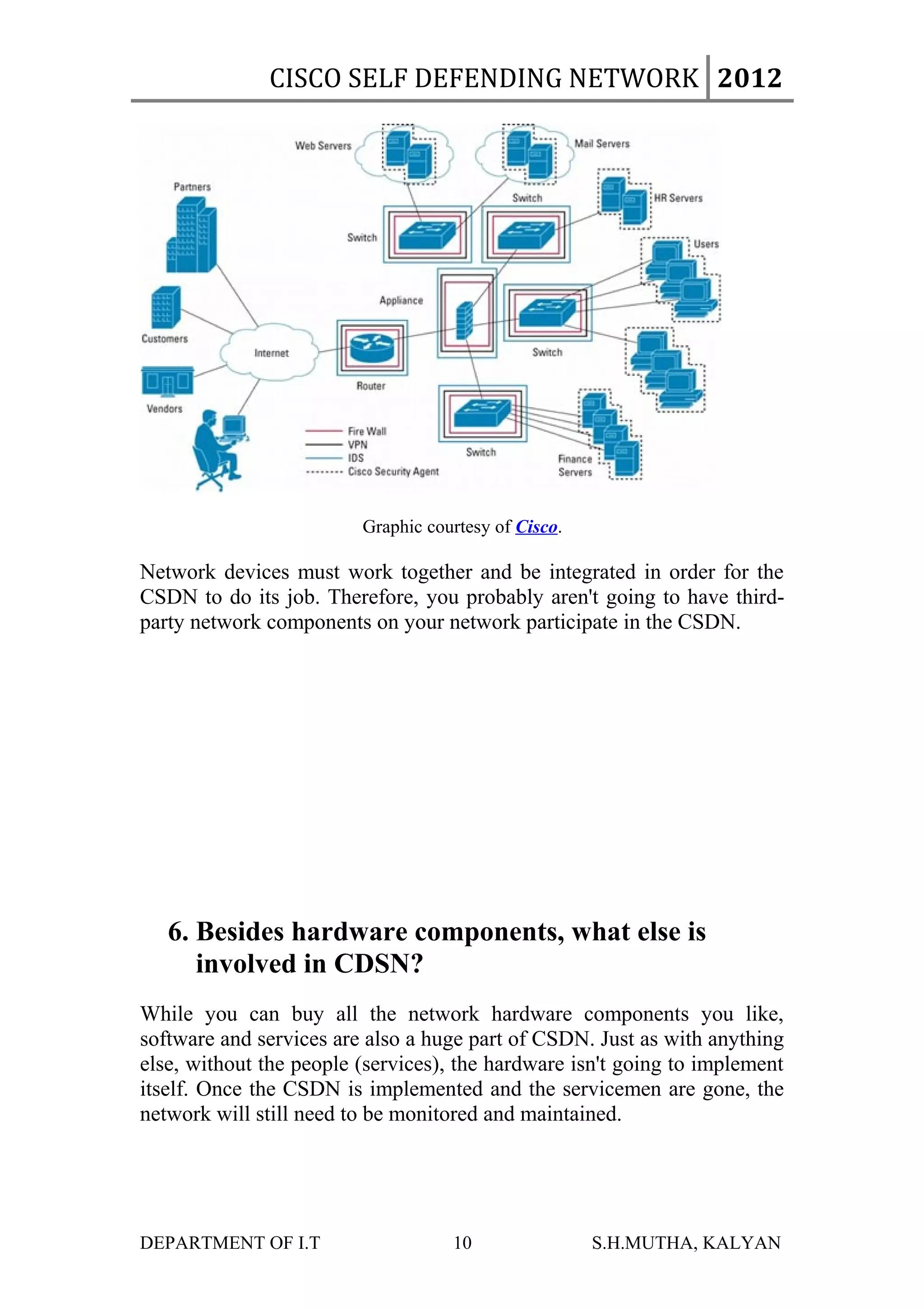
The document discusses Cisco's Self-Defending Network (CSDN) security solution. The CSDN uses various Cisco components like firewalls, intrusion detection systems, and authentication servers that work together to secure the network. It aims to provide end-to-end visibility of security events and adapt to threats. Standards like Network Admission Control are also important to CSDN. While an integrated solution, fully implementing and maintaining CSDN is challenging and expensive.












![CISCO SELF DEFENDING NETWORK 2012
3. www.wikipedia.com
4. Tanenbaum, Computer Networks [144-216].
Homework Help
https://www.homeworkping.com/
Math homework help
https://www.homeworkping.com/
Research Paper help
https://www.homeworkping.com/
Algebra Help
https://www.homeworkping.com/
Calculus Help
https://www.homeworkping.com/
Accounting help
https://www.homeworkping.com/
Paper Help
https://www.homeworkping.com/
Writing Help
https://www.homeworkping.com/
Online Tutor
https://www.homeworkping.com/
Online Tutoring
https://www.homeworkping.com/
DEPARTMENT OF I.T 15 S.H.MUTHA, KALYAN](https://image.slidesharecdn.com/85320337-networking-case-study-150908150227-lva1-app6891/75/85320337-networking-case-study-15-2048.jpg)