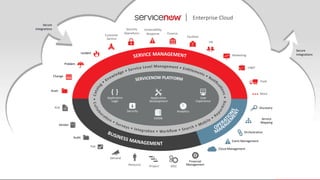
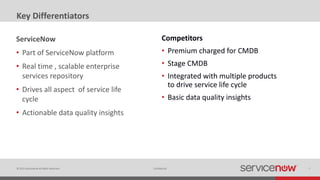
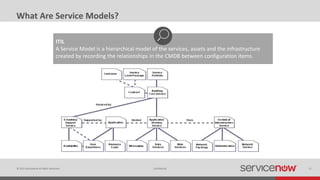
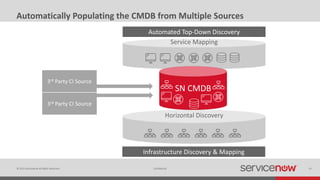
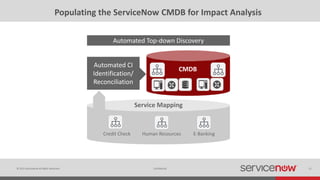
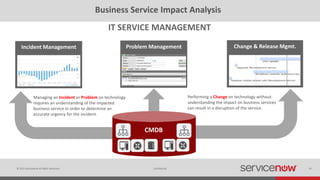
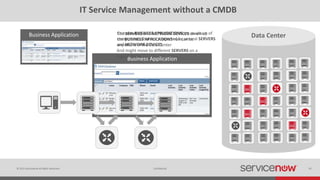
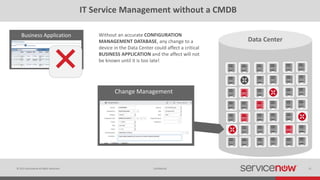
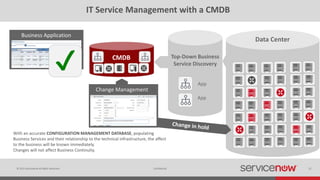
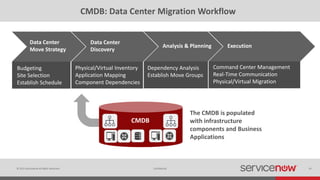
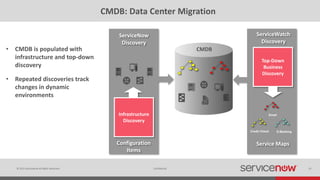
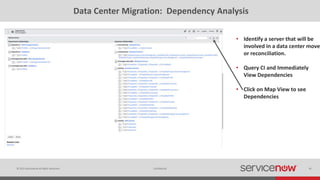
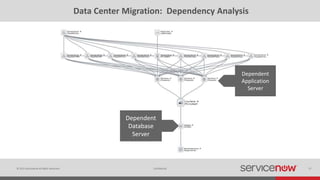
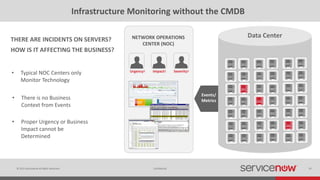
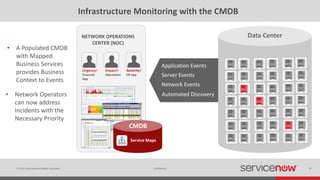
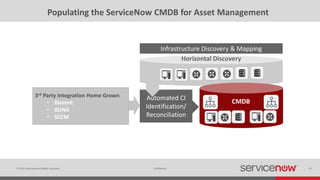
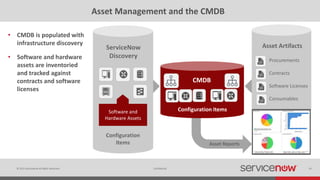
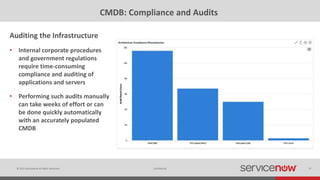
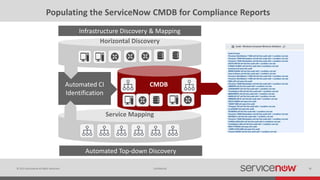
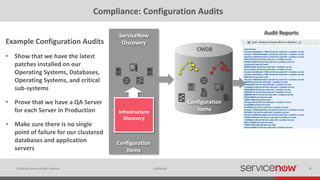
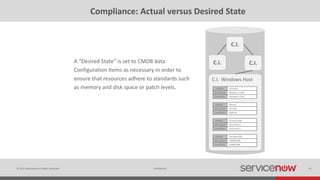
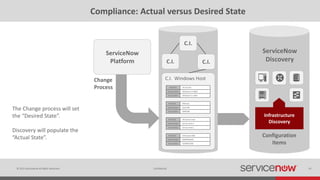
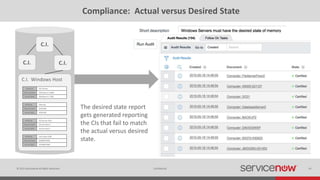
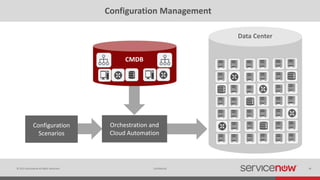
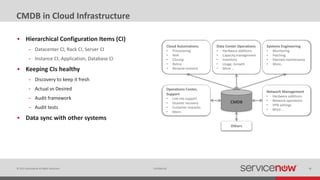
The document discusses the importance of a Configuration Management Database (CMDB) for managing IT infrastructure and services, noting that a CMDB provides a single system of record that supports IT operations, service, asset and configuration management. It describes how ServiceNow's CMDB integrates these capabilities and provides real-time data to drive automation. Examples of how a CMDB supports use cases like impact analysis, asset management, compliance and cloud management are also provided.