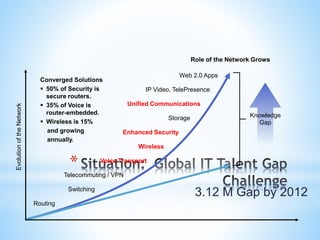
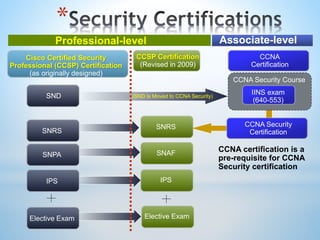
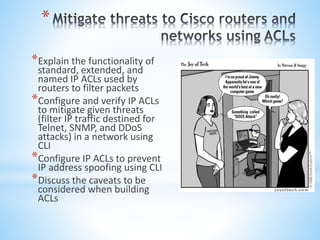
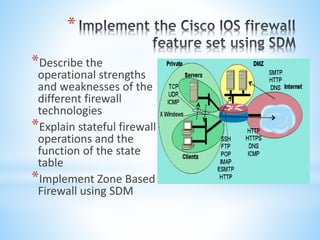
This document discusses Cisco's CCNA Security certification program. It provides an overview of the CCNA Security curriculum, which teaches skills for network security roles like network security specialists and security administrators. These include securing Cisco routers, implementing authentication, authorization and accounting, using access control lists for threat mitigation, and configuring firewalls, intrusion prevention systems and VPNs. Obtaining the CCNA Security certification verifies an individual's ability to install, troubleshoot and monitor Cisco security technologies.