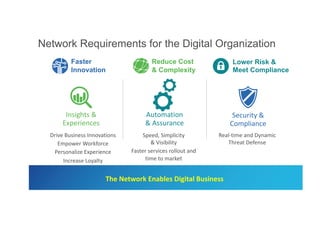
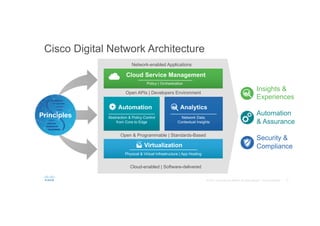
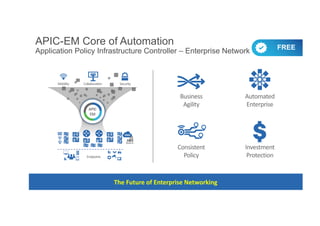
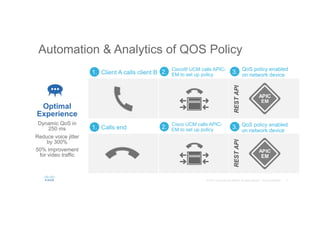
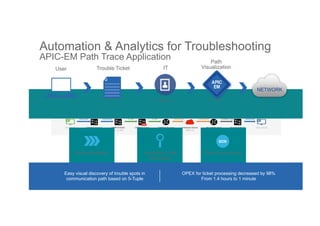
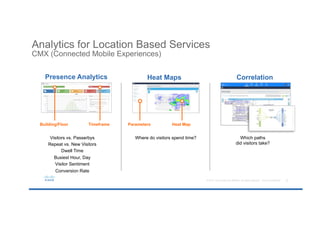
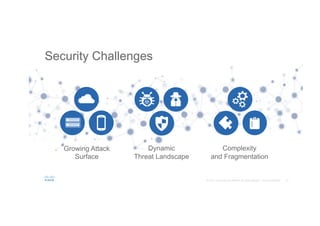
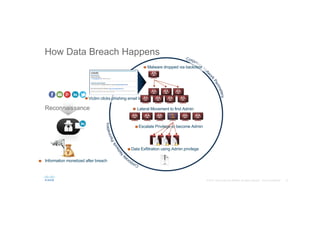
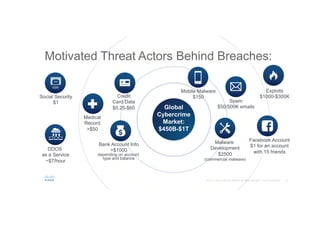
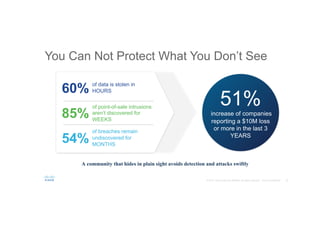
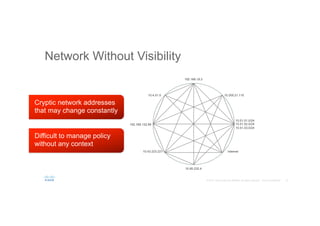
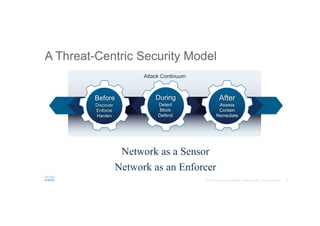
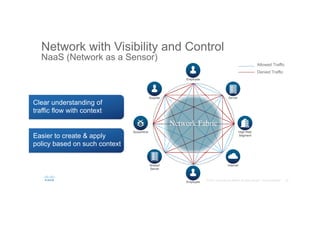
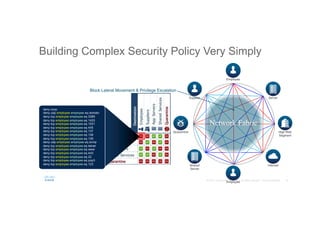
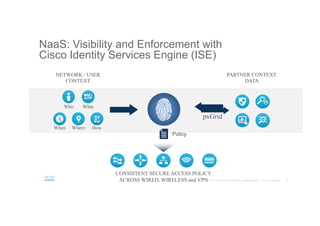
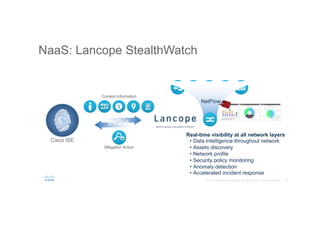
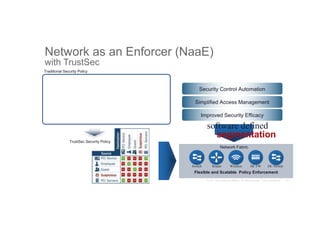
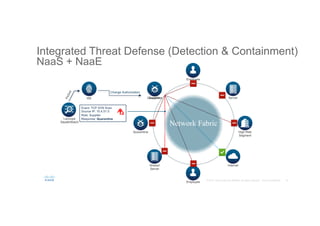
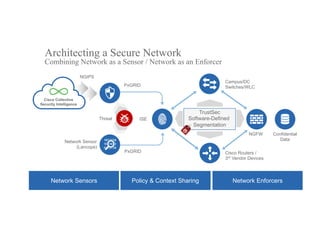
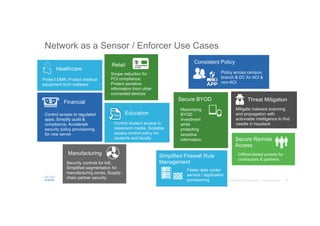
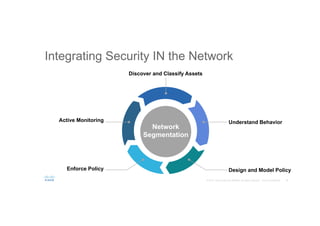
The document discusses the evolving role of networks in supporting digital business and the associated security challenges. It highlights the need for organizations to adapt their network infrastructure to embrace emerging technologies while improving visibility and threat response capabilities. Key topics include digital transformation, Internet of Things, advanced security measures, and the importance of network-centric policies in mitigating potential cyber threats.